BOOK THIS SPACE FOR AD
ARTICLE ADThe Blackwood APT is using the NSPX30 backdoor in cyberespionage attacks against individuals and companies in China, Japan, and the UK.
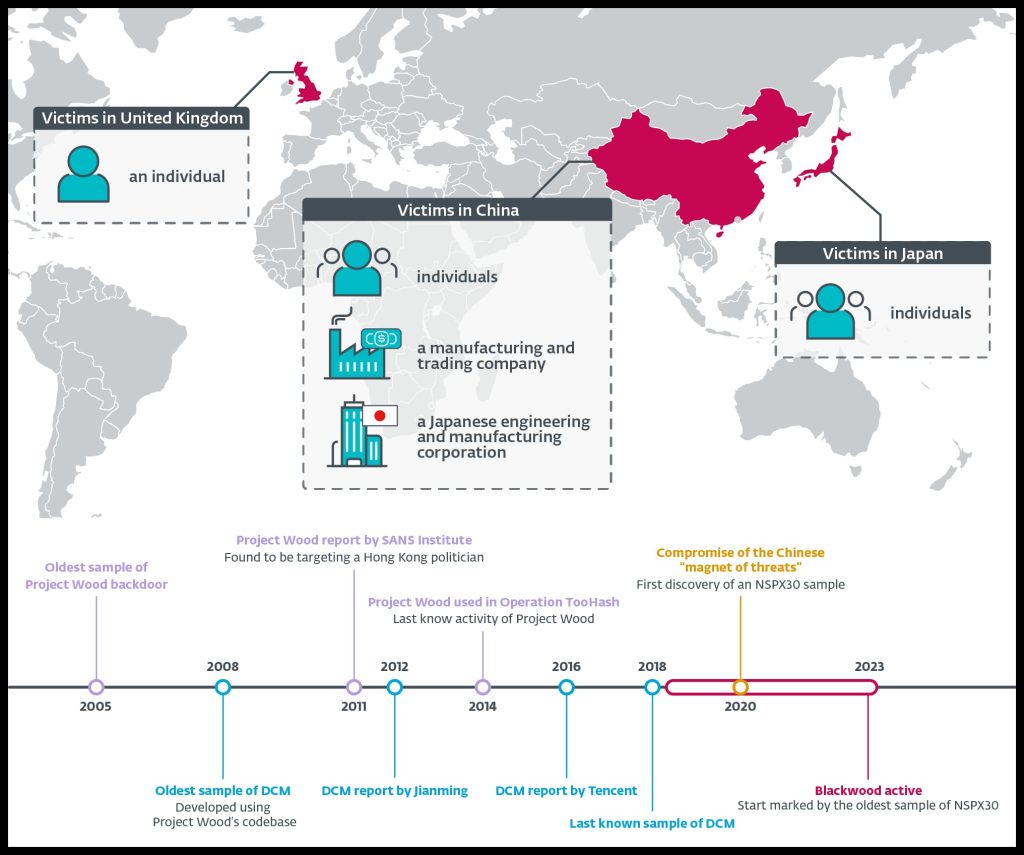
ESET researchers have discovered a new China-aligned APT group, Blackwood, using advanced implants in cyberespionage attacks targeting individuals and companies in China, Japan, and the UK.
The researchers identified NSPX30, a sophisticated implant used by Blackwood, which uses adversary-in-the-middle (AiTM) techniques to hijack update requests from legitimate software.
ESET traced NSPX30’s evolution back to Project Wood, a simple backdoor, with the oldest sample found in 2005. The implants’ evolution began on January 9th, 2005. The backdoor collects system and network information, records keystrokes, and takes screenshots, as indicated by PE (Portable Executable) header timestamps in the loader and backdoor components
Blackwood backdoor has been operating since 2018, and in 2020, malicious activity on a targeted system in China increased. The NSPX30 implant, a multistage implant, was detected on a few systems, with victims including:
“Unidentified individuals in China and Japan, a Chinese-speaking individual connected to a high-profile UK public research university, a large Chinese manufacturing company, and China-based offices of a Japanese corporation,” researchers stated in a blog post.
NSPX30 is a modular implant with plugins that can steal sensitive data, monitor user activity, and disrupt system operations, potentially causing damage. Utilizing the NSPX30 implant, a sophisticated spying tool, attackers employ a strategy to re-compromise systems in the event of lost access.
ESET Research has identified a concerning pattern where legitimate software, such as Tencent QQ, Sogou Pinyin, and WPS Office, downloads updates from unencrypted HTTP servers. This vulnerability enables attackers to establish communication channels, gather data, and capture screenshots.
To further hide their activities, attackers leverage interception techniques to anonymize their infrastructure. The malicious traffic generated by NSPX30 is then seamlessly forwarded to the attackers’ infrastructure through an undisclosed mechanism.
The discovery of NSPX30 active since 2005, highlights how cybersecurity threats have evolved over the years. The discovery also emphasizes the need for strong cybersecurity practices, including keeping software updated, being cautious about suspicious attachments, and investing in security solutions with advanced malware detection capabilities, to better defend against this persistent threat.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·