BOOK THIS SPACE FOR AD
ARTICLE AD
PSI Software SE, a German software developer for complex production and logistics processes, has confirmed that the cyber incident it disclosed last week is a ransomware attack that impacted its internal infrastructure.
The company operates at a global level with a staff of more than 2,000 and specializes in software solutions for major energy suppliers.
It also provides "control system solutions for operational management, network utilization, pipeline management, leak detection and location, portfolio management, energy trading and sales."
On February 15, PSI Software announced that a cyberattack forced it to disconnect several IT systems, including email, as a measure to mitigate the risk of data loss.
In an update yesterday, the company confirmed that the disruption was caused by ransomware actors targeting its systems. The firm has yet to determine the exact intrusion vector.
"We detected unusual activity in our network during the night of February 15, 2024. As a result, all external connections and systems were successively shut down still in the night" - PSI Software
PSI says the investigation so far has not revealed any evidence that the attacker pivoted to customer systems.
Authorities have been informed of the incident and experts from the Federal Office for Information Security have been helping PSI's incident response and remediation efforts since February 16.
Hunters International claims responsibility
Though PSI Software has not shared specific details about the threat group responsible for the attack, the Hunters International ransomware gang has claimed the breach.
The threat actors posted PSI Software on their extortion portal on the dark web on February 17, two days after the attack.
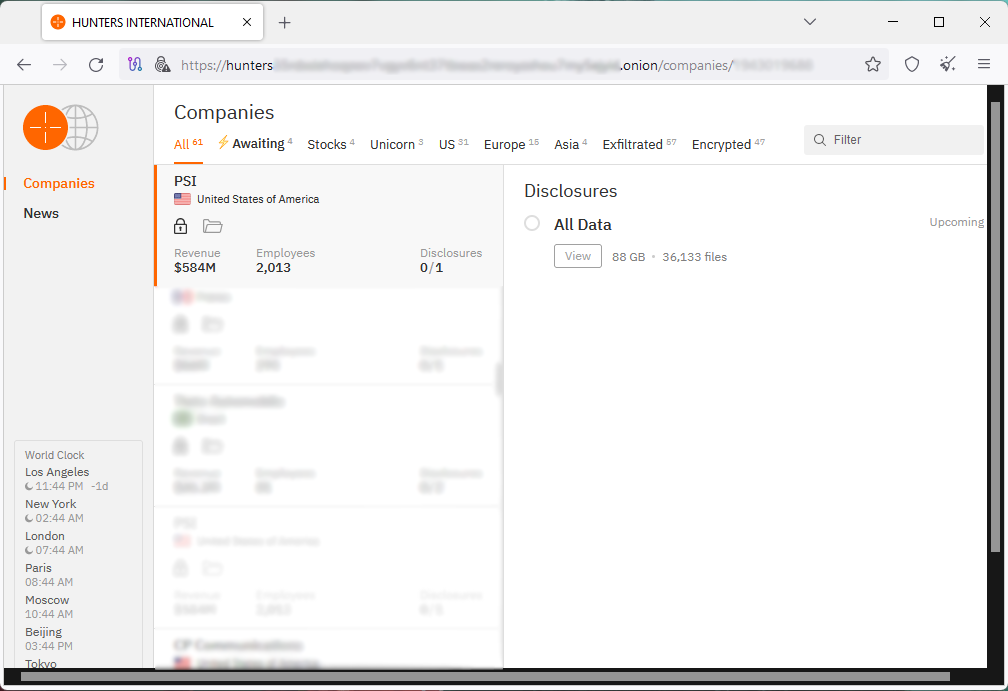
The hackers claim to have stolen 36,133 files from PSI's systems, totaling 88 GB in size. No data samples have been published yet, so the validity of the threat actor's statement is not confirmed.
Hunters International is a ransomware-as-a-service operation that emerged in October 2023 as a possible rebrand of Hive.
The threat actors have published numerous victims on the extortion portal since then, including US Navy contractor Austral USA and the Fred Hutchinson Cancer Center.
In the case of the Fred Hutch cancer research center, the hackers demonstrated low moral principles and blackmailed patients individually.
.png)
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·