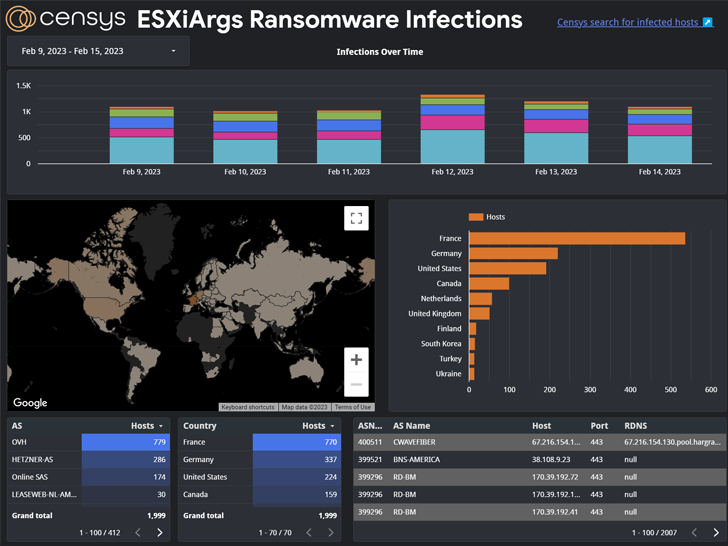
More than 500 hosts have been newly compromised en masse by the ESXiArgs ransomware strain, most of which are located in France, Germany, the Netherlands, the U.K., and Ukraine.
The findings come from attack surface management firm Censys, which discovered "two hosts with strikingly similar ransom notes dating back to mid-October 2022, just after ESXi versions 6.5 and 6.7 reached end of life."
The first set of infections dates back to October 12, 2022, much earlier than when the campaign began to gain traction at the start of February 2023. Then on January 31, 2023, the ransom notes on the two hosts are said to have been updated with a revised version that matches the ones used in the current wave.
Some of the crucial differences between the two ransom notes include the use of an onion URL instead of a Tox chat ID, a Proton Mail address at the bottom of the note, and a lower ransom demand (1.05 Bitcoin vs. 2.09 Bitcoin).
"Each variant of the ransom notes from October 2022 through February 2023 are strikingly similar in wording to the note of an earlier ransomware variant, Cheerscrypt, which gained notoriety in early 2022," researchers Mark Ellzey and Emily Austin said.
It's worth noting that ESXiArgs is suspected to be based on the leaked Babuk ransomware code, which also spawned other variants such as Cheerscrypt and PrideLocker last year.
The development comes less than a week after the threat actors returned with a new variant that tweaks the encryption method and the ransom note following the release of a decryptor to help recover infected systems.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has since stated that the attackers are "likely targeting end-of-life ESXi servers or ESXi servers that do not have the available ESXi software patches applied."
"The vulnerability in VMware ESXi is a clear reminder of the importance of keeping systems up to date with the latest security patches while also employing strong perimeter defense," Bitdefender's Martin Zugec said.
"Attackers don't need to scour for new exploits or novel techniques when they know that many organizations are vulnerable to older exploits due, in part, to the lack of proper patch management and risk management."
The spike also coincides with an 87% year-over-year increase in ransomware attacks targeting industrial organizations in 2022, with 437 out of 605 attacks striking the manufacturing sector, per a new report from Dragos, in part fueled by continued evolution in ransomware-as-a-service (RaaS) models.
Data gathered by the industrial security firm reveals that 189 ransomware attacks were reported in the final quarter of 2022 alone. Top targeted verticals included manufacturing (143), food and beverage (15), energy (14), pharma (9), oil and gas (4), and mining (1).
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
.png)
 1 year ago
110
1 year ago
110 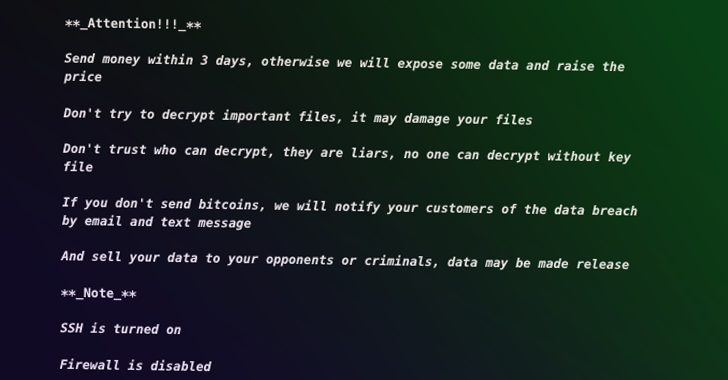















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·