Cybersecurity researchers have managed to build a clone of Apple Airtag that circumvents the anti-stalking protection technology built into its Find My Bluetooth-based tracking protocol.
The result is a stealth AirTag that can successfully track an iPhone user for over five days without triggering a tracking notification, Positive Security's co-founder Fabian Bräunlein said in a deep-dive published last week.
Find My is Apple's asset tracking app that allows users to track the GPS location of iOS, iPadOS, macOS, watchOS devices, AirPods, AirTags as well as other supported third-party accessories through a connected iCloud account. It also enables users to view the location of others who have opted to share their location.
This is far from the first time weaknesses have been uncovered in Apple's Find My system. In March 2021, the Secure Mobile Networking Lab at the Technical University of Darmstadt, Germany (SEEMO) disclosed design and implementation flaws in the protocol that can lead to a location correlation attack and unauthorized access to users' location histories
Then in May 2021, Bräunlein followed it up by sharing details of a communication protocol built on top of Find My that enables arbitrary data to be uploaded from non-internet-connected devices by sending "Find My" Bluetooth broadcasts to nearby Apple devices that can carry out the data upload.
The development also comes as Apple, earlier this month, introduced a raft of new anti-stalking measures to AirTags to prevent their misuse associated with tracking unsuspecting individuals without their consent, inserting a warning notifying users that doing so has criminal repercussions.
"If an AirTag, set of AirPods, or Find My network accessory is discovered to be unlawfully tracking a person, law enforcement can request any available information from Apple to support their investigation," Apple spells out in an updated support article.
But the "Find You" AirTag clone devised by Positive Security aims to get around "every current and upcoming protection measure." It's also built using OpenHaystack, an open-source framework developed by SEEMO researchers for tracking personal Bluetooth devices via Apple's crowdsourced Find My network.
By broadcasting new, never-seen-before public keys every 30 seconds from a list of 2,000 preloaded public keys through the proof-of-concept (PoC) device, it was found that the mechanism renders the tracking device undetectable, raising no alerts in iOS and Apple's own Tracker Detect Android app even when unwanted AirTags are present.
Interestingly, AirGuard, which was developed by SEEMO as a third-party alternative to Tracker Detect, is capable of discovering the clone in "manual scan" mode, calling into question the effectiveness of the safety and security barriers implemented by Apple to safeguard users from the malicious use of AirTags.
"The ubiquitous nature of the Find My network, combined with its high accuracy and low entry cost, lowers the bar for abuse," SEEMO researchers Alexander Heinrich, Niklas Bittner, and Matthias Hollick said in a new paper, pointing out how "AirGuard found more actual trackers in different scenarios compared to the iOS tracking detection."
"Apple needs to incorporate non-genuine AirTags into their threat model, thus implementing security and anti-stalking features into the Find My protocol and ecosystem instead of in the AirTag itself, which can run modified firmware or not be an AirTag at all," Bräunlein said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
143
2 years ago
143 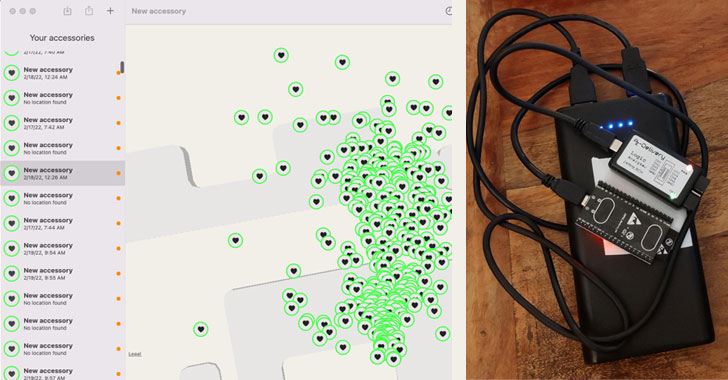

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·