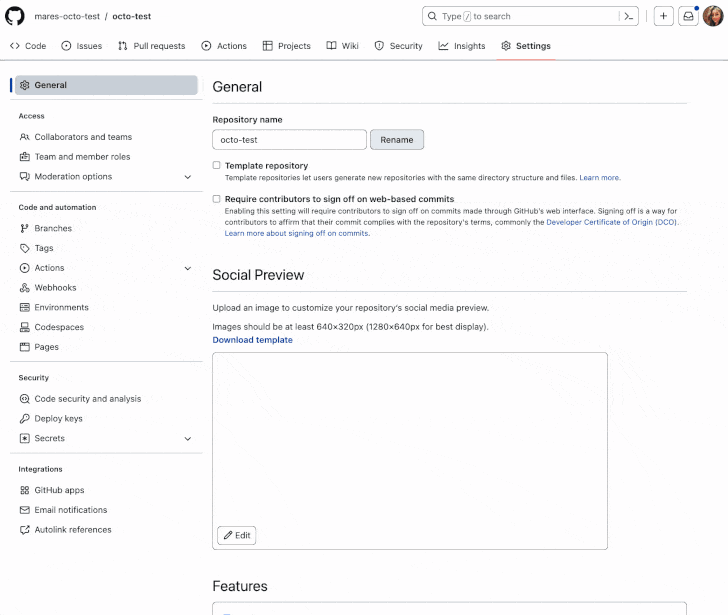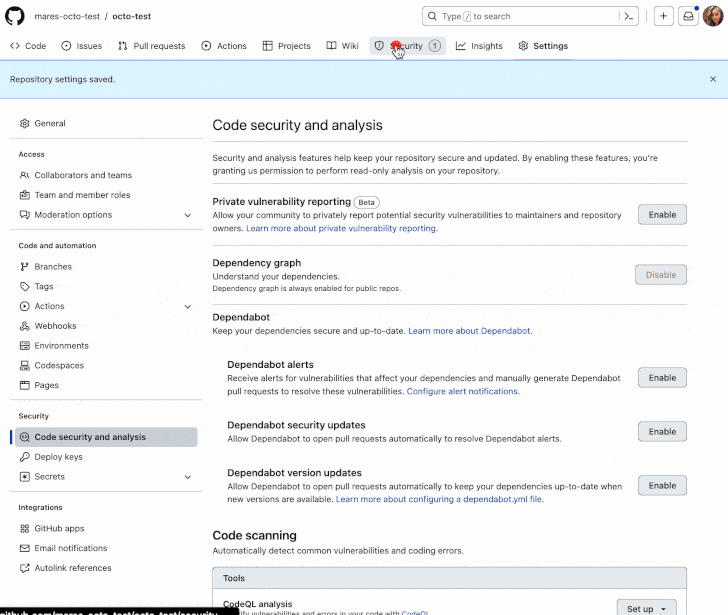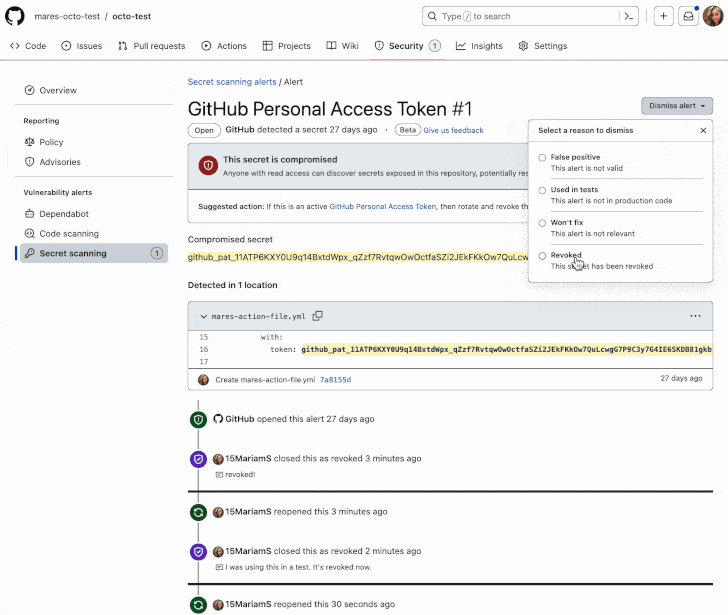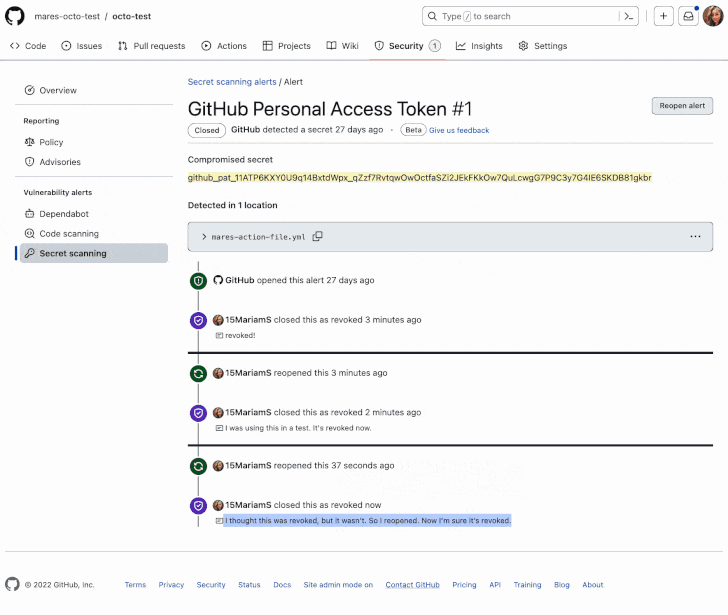
GitHub on Thursday said it is making available its secret scanning service to all public repositories on the code hosting platform for free.
"Secret scanning alerts notify you directly about leaked secrets in your code," the company said, adding it's expected to complete the rollout by the end of January 2023.
Secret scanning is designed to examine repositories for access tokens, private keys, credentials, API keys, and other secrets in over 200 formats that may have been accidentally committed, and generate alerts to prevent their misuse.
The security option was previously limited to repositories owned by organizations that use GitHub Enterprise Cloud and have a GitHub Advanced Security license.
For customers of GitHub Advanced Security, the protections go a step further by performing the scans for exposed secrets, including custom patterns, during code pushes.
The Microsoft subsidiary also said it's planning to turn on two-factor authentication requirements for "distinct groups of users" starting March 2023 with the goal of expanding it to all GitHub users by the end of next year.
The users are likely to comprise those who have published GitHub or OAuth apps, created a release, contributed code to critical open source repositories, and are Enterprise and Organization administrators.
The company further stated it's "hard at work" to integrate passkey support for stronger phishing-resistant authentication.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
.png)
 1 year ago
161
1 year ago
161 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·