Details of a new nation-state sponsored phishing campaign has been uncovered setting its sights on European governmental entities in what's seen as an attempt to obtain intelligence on refugee and supply movement in the region.
Enterprise security company Proofpoint, which detected the malicious emails for the first time on February 24, 2022, dubbed the social engineering attacks "Asylum Ambuscade."
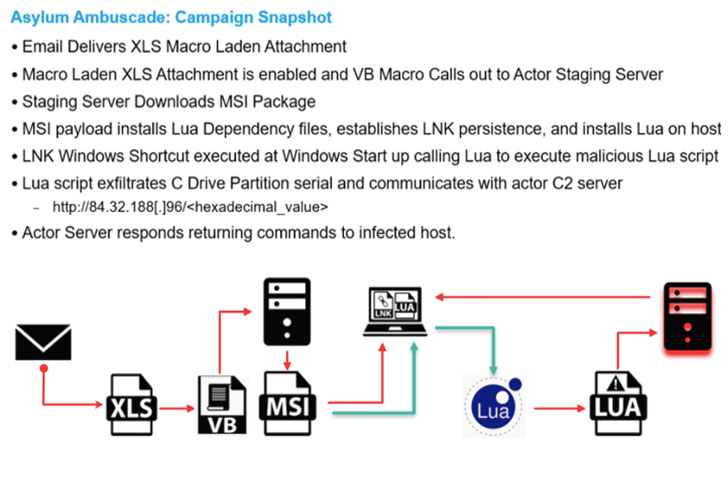
"The email included a malicious macro attachment which utilized social engineering themes pertaining to the Emergency Meeting of the NATO Security Council held on February 23, 2022," researchers Michael Raggi and Zydeca Cass said in a report published Tuesday.
"The email also contained a malicious attachment which attempted to download malicious Lua malware named SunSeed and targeted European government personnel tasked with managing transportation and population movement in Europe."
The findings build on an advisory issued by the State Service of Special Communication and Information Protection of Ukraine (DSSZZI), which warned last week of phishing messages targeting its military personnel with ZIP file attachments with the goal of stealing sensitive personal information.
Proofpoint declined to attribute the newly observed campaign to a specific threat actor, but noted that the overlaps in the timeline of the two sets of attacks, the phishing lures used, and the victimology patterns aligns with that of a Belarusian nation-state group called UNC1151 (aka TA445 or Ghostwriter).
One of the notable aspects of Asylum Ambuscade is the likely use of a compromised Ukrainian armed service member's email account to broadcast malware-laced email messages containing a macro-enabled XLS file that delivers SunSeed onto infected hosts, implying that the latest campaign may be a continuation of these attacks.
"The social engineering lures utilized in this phishing campaign were very timely, following a NATO Security Council meeting on February 23, 2022 and a news story about a Russian government 'kill list' targeting Ukrainians that began circulating in Western media outlets on February 21, 2022," the researchers noted.
SunSeed, for its part, functions as a downloader that establishes communications with an actor-controlled server to retrieve next-stage payloads for execution.
The Sunnyvale-based cybersecurity company noted that the attacks specifically singled out individuals who were tasked with responsibilities related to transportation, financial and budget allocation, administration, and population movement within Europe.
The disclosure comes as Russia's intensifying military invasion of Ukraine has polarized cyberspace, with hacktivists, cybercriminals, white hat researchers, and technology companies picking a side in the conflict.
In a separate update posted earlier today, Ukraine's Computer Emergency Response Team (CERT-UA) described the ongoing developments as an "information and psychological war," urging people in the country to carefully monitor their accounts for unrecognized devices, turn on two-factor authentication, and use end-to-end encrypted messaging apps.
What's more, email security company Avanan said it witnessed an eightfold increase in email-borne attacks originating from Russia starting on February 27, at least some of them targeting manufacturing, international shipping, and transportation companies located in the U.S. and Europe.
"In light of the ongoing Russia-Ukraine war, actions by proxy actors like TA445 will continue to target European governments to gather intelligence around the movement of refugees from Ukraine and on issues of importance to the Russian government," the researchers said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
162
2 years ago
162 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·