BOOK THIS SPACE FOR AD
ARTICLE ADHello Hackers, Aditya here I am a cyber security student and bug bounty hunter.
This is my first bug hunting write-up. This program doesn’t allow disclosure so we are assuming as an example.com.
so, it all started 5 months ago when I was doing way back URL recon on example.com after spending 10minutes I found an interesting endpoint (token=) That discloses 100+ clients Payment information, phone no, email names.
Here are the steps on how I found the bug and how you can find it too.
Go to the way back URL https://web.archive.org/cdx/search/cdx?url=*.target.com/*&collapse=urlkey&output=text&fl=originaland in place of *.target.com enter your target domain for eg- *.google.com3. Then just simply press ctrl+f and start looking for interesting endpoints
4. Here are the list of some endpoints that you can search
Search for =http, =/, =%2F, api, access, token, .json, admin, aws, .js, config, /v1, /v2, /v3, dashboard, oauth, url, uri, .target.com (For getting some subdomains), ey (for jwt), auth, internal, dev
5. i have search for token=

6. and found the URL which leaked high priority pii.
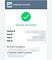
Timeline:-
Reported Bug on — Aug 23, 2021
Got a reply of closing the report on — Aug 30, 2021
Reopening of Report and Bounty — Jan 10, 2021
Bounty Amount — Rs. 10,000
Thank You For Reading, have a great day.
Social media handles:-
LinkedIn — https://www.linkedin.com/in/aditya-singh-b78111169/
Instagram — https://www.instagram.com/aditya_singh.exe/
.png)
 2 years ago
129
2 years ago
129 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·