BOOK THIS SPACE FOR AD
ARTICLE ADHello everyone, I’m “the injector ”, I’m a network administrator and a bug bounty hunter, today i will show you how im hack a panel of php Material_wallpaper & Viaviweb Wallpaper in 2020
About this app:“Material Wallpaper is a mobile image gallery and wallpaper system which run under Android platform that used for your own gallery and wallpaper application. Support with responsive admin panel can manage unlimited category and image gallery easily. Run under Android platform which is the most popular operating system in the world. Using this application you can save your money and time in creating application for your own image gallery and wallpaper application.”
default user and password is :’admin: admin’.
Firstly I downloaded this source code and I’m running this code on my localhost to make a short analysis of files. This PHP panel is protected with a License key 😀, after the analysis, I made a reverse engineering of this source code to remove the function of the License key.
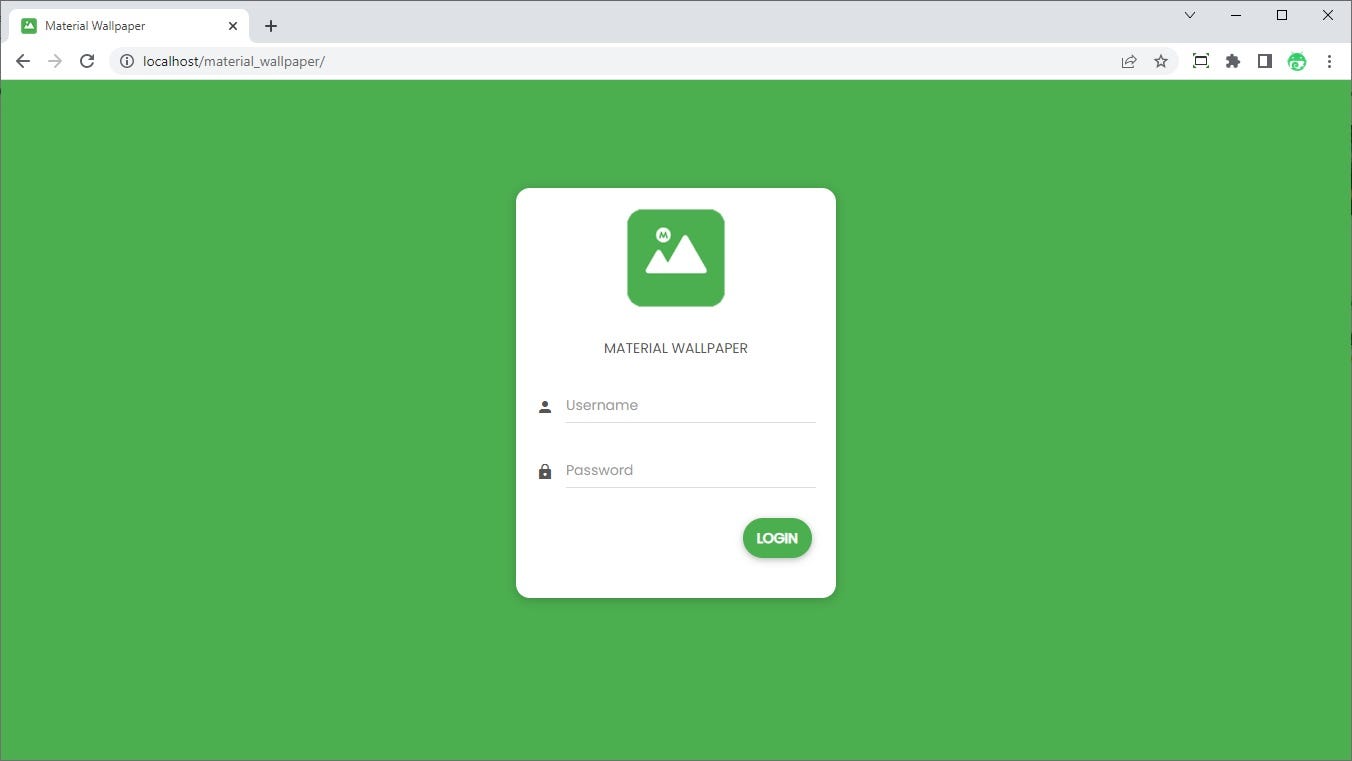

then I found a vulnerability in this panel to bypass firstly the login page without a username or password.
(i will not show you the method for security reasons)

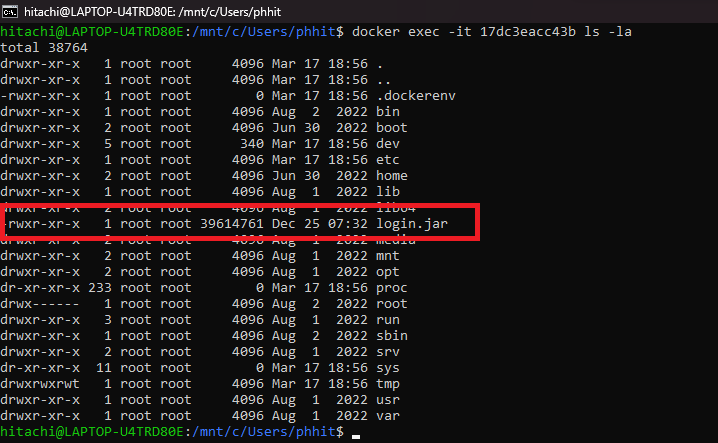
Secondly, I bypassed the restrictions upload of not allowed file extensions and now I have permission to upload any file with any extension, then I’m uploading a reverse shell PHP. I reported this vulnerability to the owner of this application, and his answer was unacceptable that I am a bad person, and the link is that I am a highly-skilled person and I used it against him. Rather, my intention was to report it to correct this vulnerability, because a lot of developers using this source code and placing Admob ads, Facebook Network audience (ads), StartApp, Unity Ads… Whoever discovered this vulnerability can place his own ads or delete databases.

Reverse Shell after Bypass
Host Used:MyLocalhost)

I hope this developer makes an update for this vulnerability is not yet patched from 2020 to 2022
NB: more than +1000 apps use this source code. (the same method for Viaviweb source code )
Thanks!
.png)
 1 year ago
80
1 year ago
80 












 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·