BOOK THIS SPACE FOR AD
ARTICLE ADHow to Perform good Recon
Hello.Iam a Ethical Hacker,Mini Programmer,Mini App Developer,Osint Noob,Student,Article Writer,Instructor,seasonal Free time Bug hunter.Today, Iam writing about Recon.
Performing a successful reconnaissance (recon) is a crucial step in bug bounty hunting. It helps you gather valuable information about the target system, identify potential vulnerabilities, and plan your testing approach. Here are some guidelines for conducting effective recon in bug bounty hunting:
Understand the scope: Start by thoroughly reviewing the bug bounty program’s scope and rules. Pay close attention to the assets in scope, target domains, and any specific testing guidelines or restrictions. This helps you focus your recon efforts on the authorized areas.
Gather information passively: Begin by conducting passive reconnaissance to gather information without directly interacting with the target. Use tools like search engines, public databases, and social media platforms to find publicly available information related to the target organization, its infrastructure, employees, technologies used, and any previous vulnerabilities or incidents.
Enumerate target domains and subdomains: Identify the target organization’s domain(s) and enumerate its subdomains. Tools like Sublist3r, Amass, or Subfinder can help automate the process. Subdomains sometimes offer additional attack surfaces and may be more prone to vulnerabilities.
Port scanning and service enumeration: Use tools like Nmap or Masscan to scan for open ports on the target’s IP addresses or domains. Once open ports are identified, perform service enumeration to determine the versions and configurations of the services running on those ports. This information can be valuable for identifying known vulnerabilities or misconfigurations.
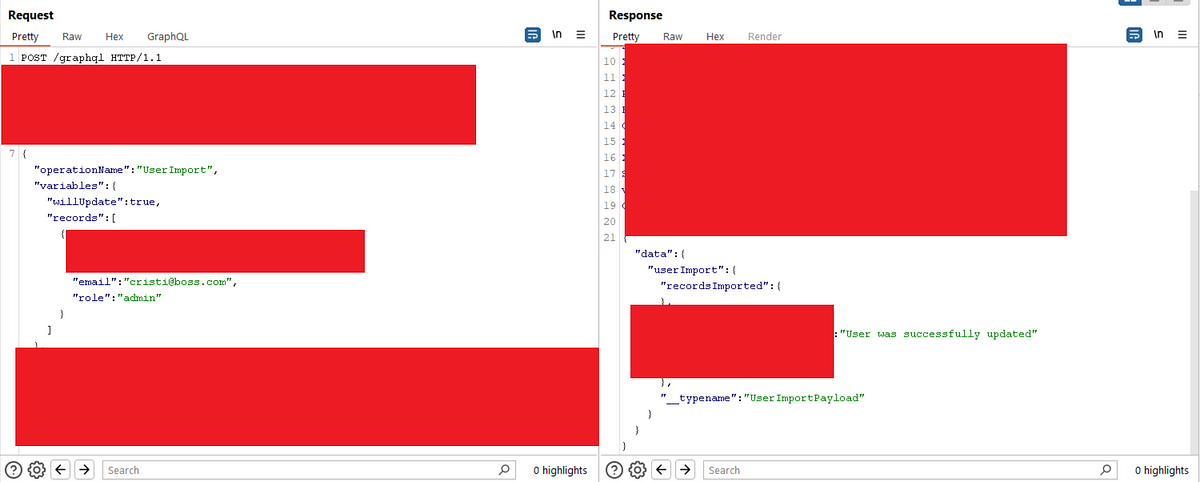
Conduct web application scanning: Utilize web application scanners like Burp Suite, OWASP ZAP, or Nikto to automatically identify potential vulnerabilities in the target’s web applications. These tools can detect common issues like SQL injection, cross-site scripting (XSS), and insecure server configurations.
Monitor public bug bounty forums and reports: Stay updated on public bug bounty forums, platforms, and security advisories related to the target organization. Analyze previously reported vulnerabilities and researcher disclosures to gain insights into potential attack vectors or weak points.
Check for misconfigurations and data exposures: Look for misconfigured cloud storage (e.g., Amazon S3 buckets) or publicly accessible files or directories. Tools like Gobuster, Dirsearch, or AWSBucketDump can aid in discovering hidden or exposed resources.
Analyze mobile applications (if applicable): If the target has mobile applications, use tools like MobSF, Frida, or jadx to decompile and analyze the app for potential vulnerabilities, insecure API endpoints, or insecure data storage.
Monitor DNS records and certificate transparency logs: Keep an eye on changes in DNS records and monitor certificate transparency logs for new domain registrations or SSL certificates issued for the target organization. This can help identify potentially overlooked assets or related infrastructure.
Document findings and report responsibly: Throughout the recon process, maintain detailed documentation of your findings, including screenshots, logs, and relevant URLs. When reporting vulnerabilities, ensure you follow the bug bounty program’s responsible disclosure guidelines and provide clear and actionable information.
Remember to always adhere to ethical guidelines and the specific rules set forth by the bug bounty program you are participating in. Act responsibly, obtain proper authorization, and respect the target’s boundaries to ensure a positive bug bounty experience.
.png)
 10 months ago
50
10 months ago
50 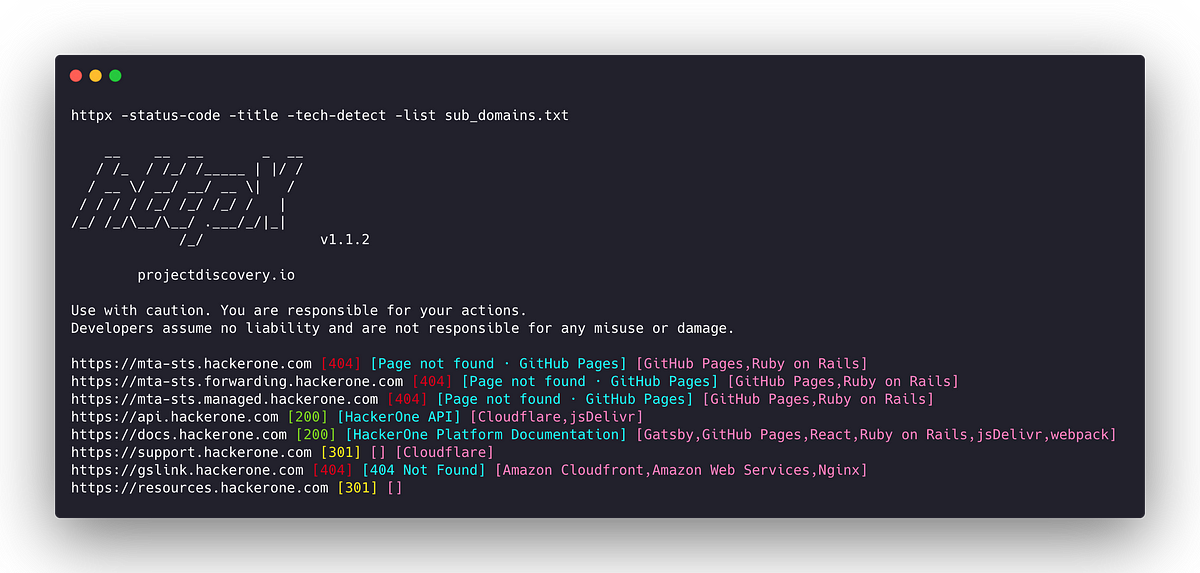













 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·