The Iranian state-sponsored threat actor tracked under the moniker Lyceum has turned to using a new custom .NET-based backdoor in recent campaigns directed against the Middle East.
"The new malware is a .NET based DNS Backdoor which is a customized version of the open source tool 'DIG.net,'" Zscaler ThreatLabz researchers Niraj Shivtarkar and Avinash Kumar said in a report published last week.
"The malware leverages a DNS attack technique called 'DNS Hijacking' in which an attacker-controlled DNS server manipulates the response of DNS queries and resolves them as per their malicious requirements."
DNS hijacking is a redirection attack in which DNS queries to genuine websites are intercepted to take an unsuspecting user to fraudulent pages under an adversary's control. Unlike cache poisoning, DNS hijacking targets the DNS record of the website on the nameserver, rather than a resolver's cache.
Lyceum, also known as Hexane, Spirlin, or Siamesekitten, is primarily known for its cyber attacks in the Middle East and Africa. Earlier this year, Slovak cybersecurity firm ESET tied its activities to another threat actor called OilRig (aka APT34).
The latest infection chain involves the use of a macro-laced Microsoft Document downloaded from a domain named "news-spot[.]live," impersonating a legitimate news report from Radio Free Europe/Radio Liberty about Iran's drone strikes in December 2021.
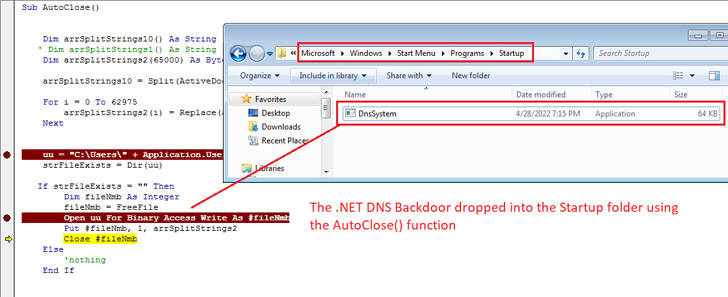
Enabling the macro results in the execution of a malicious code that drops the implant to the Windows Startup folder to establish persistence and ensure it automatically runs every time the system is restarted.
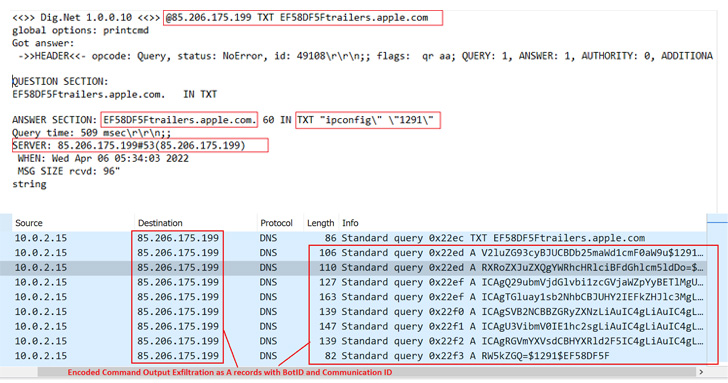
The .NET DNS backdoor, dubbed DnsSystem, is a reworked variant of the open-source DIG.net DNS resolver tool, enabling the Lyceum actor to parse DNS responses issued from the DNS server ("cyberclub[.]one") and carry out its nefarious goals.
In addition to abusing the DNS protocol for command-and-control (C2) communications to evade detection, the malware is equipped to upload and download arbitrary files to and from the remote server as well as execute malicious system commands remotely on the compromised host.
"APT threat actors are continuously evolving their tactics and malware to successfully carry out attacks against their targets," the researchers said. "Attackers continuously embrace new anti-analysis tricks to evade security solutions; re-packaging of malware makes static analysis even more challenging."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
148
2 years ago
148 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·