BOOK THIS SPACE FOR AD
ARTICLE ADIvanti has released patches for vulnerabilities found in its enterprise VPN appliances, including two flagged as exploited zero-days in early January 2024.
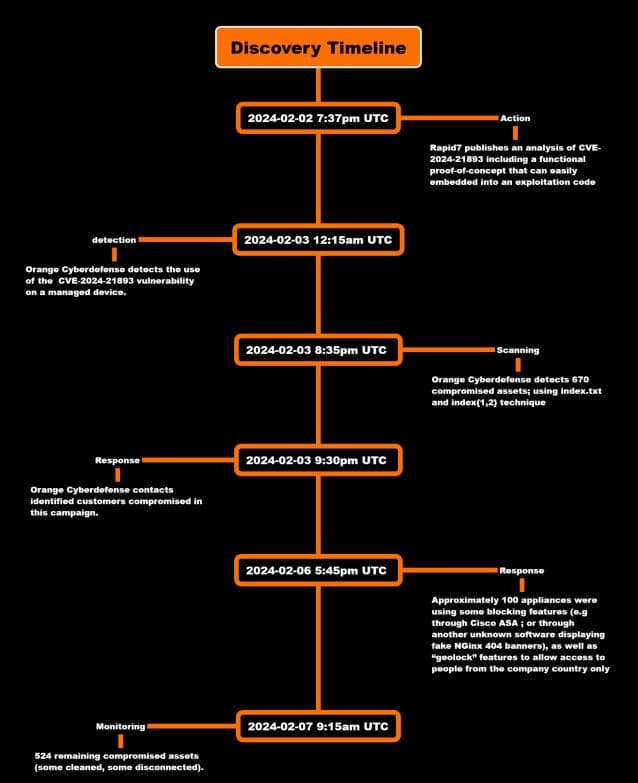
On January 31, 2024, Ivanti released fixes to address four vulnerabilities, including CVE-2023-46805, CVE-2024-21887, CVE-2024-21888, and CVE-2024-21893. The last two vulnerabilities were disclosed the same day when the patch was released, along with a second set of mitigations as substitutes for the fixes. Within hours, Orange Cyberdefense CERT identified attacks targeting this vulnerability, allowing attackers to inject a backdoor into the Ivanti application.
In its report (PDF), Orange Cyberdefense noted discovering attackers exploiting the vulnerability to ensure persistent remote access. They injected a backdoor into a component using the SAML vulnerability, controlling access to the backdoor. Orange identified a compromised appliance on 3 February 2024, with initial mitigations applied but no patch. The attackers conducted reconnaissance to determine root access and deployed a new backdoor, DSLog, indicating they had root access to the device.
A backdoor on a compromised device enables attackers to execute commands and log all web requests, including authenticated ones, and system logs. Orange identified 700 compromised appliances, with over a hundred compromised in attacks targeting CVE-2023-46805 and CVE-2024-21887. The remaining ones had initial XML mitigation applied, preventing direct detection. The backdoor uses a unique hash per appliance.
Hackread has been following the exploitation of zero-day vulnerabilities in Ivanti VPN devices. Hackers have exploited them to deploy KrustyLoader malware and cryptocurrency miners. For your information, CVE-2023-46805 and CVE-2024-21887 were found in Ivanti Connect Secure (ICS) and Ivanti Policy Secure Gateway appliances.
CVE-2023-46805, an Authentication Bypass flaw, allows remote attackers to bypass control checks, while CVE-2024-21887 is a Command Injection flaw that lets an authenticated administrator exploit Ivanti appliances by sending crafted requests and executing arbitrary commands. CVE-2024-21888 is a Privilege Escalation vulnerability in Ivanti Connect Secure and Ivanti Policy Secure, allowing a user to gain administrative privileges.
CVE-2024-21893 is a server-side request forgery bug in the SAML component of Ivanti Connect Secure, Policy Secure, and Neurons for ZTA. The issue could be exploited without authentication to leak sensitive information. In its latest advisory, Ivanti noted that a “limited” number of customers were affected by CVE-2024-21893.
The findings were also shared by Shadowserver Foundation, which reported in early February that a zero-day vulnerability, CVE-2024-21893, discovered by Ivanti in January 2024, is being exploited in the wild. Rapid7 reported a surge in attacks since February, with over 170 discrete IP addresses involved.
Organizations are advised to install Ivanti’s patches released on January 31 and February 1, which replace initial mitigations prevent zero-day exploitation, and factory reset their devices. Additionally, they should install security updates released on February 8 to address a vulnerability in the SAML component of VPN appliances, tracked as CVE-2024-22024.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·