BOOK THIS SPACE FOR AD
ARTICLE ADThe latest revelation from law enforcement authorities in relation to this week's LockBit leaks is that the ransomware group had registered nearly 200 "affiliates" over the past two years.
Affiliates are those people who buy into the gang's ransomware-as-a-service model, and happily use LockBit's wares in exchange for a cut of the loot from the extorted victims.
New information about the group is being disseminated daily by the National Crime Agency (NCA), which has control of LockBit's site and transformed it yesterday, announcing the successful takedown of the world's leading ransomware gang.
Today's LockBit leak led to the sharing of information from inside the group's affiliate portal, showing 187 different affiliates registered between January 31, 2022, and February 5, 2024.
The FBI first started investigating LockBit in 2020, and the group has since developed new variants of its ransomware, the latest of which was released in mid-2022, so the data shared today likely shows all the affiliates that have ever deployed the most recent version of LockBit.
The data that's been gathered by compromising LockBit's backend will be used to investigate those involved in the deployment of the ransomware and paid money to be a part of the LockBit affiliate program.
"A large amount of data has been exfiltrated from LockBit's platform before it was all corrupted," reads LockBit's website, which is now under the control of the NCA.
"With this data, the NCA and partners will be coordinating further enquiries to identify the hackers who pay to be a LockBit affiliate. Some basic details published here for the first time."
When covering the story yesterday, we likened the transformation of LockBit's site into what is essentially a troll page to the NCA showing the middle finger to the criminals – a finger it further extended today.
Not only did the authorities expose the aliases of LockBit's affiliates, but they also defaced the affiliate portal with a message directed to them all, seen after logging in.
The UK, US, France, Germany, Switzerland, Australia, Finland, and the Netherlands were all involved in the multinational efforts to bring down the affiliate infrastructure, the website states.
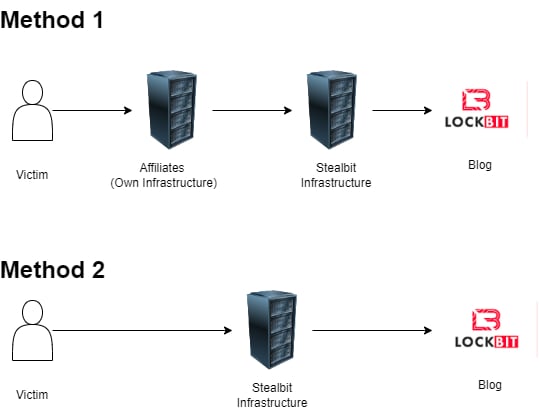
"These servers enabled both the initial cyberattacks by affiliates and supported the stealing of victim data and processing to 'StealBit' servers."
StealBit's demise
Details of StealBit – the LockBit operation's bespoke data exfiltration tool offered to affiliates – were teased in yesterday's announcement and published today as the second major revelation.
Much has been said over the years about LockBit's various ransomware payloads and its double extortion model, but StealBit is the lesser-known malware that was first deployed with LockBit 2.0 attacks dating back to 2021.
The NCA published its analysis of StealBit today, highlighting the importance of the tool in LockBit attacks and for the affiliates that deploy it.
Cops turn LockBit ransomware gang's countdown timers against them LockBit ransomware gang disrupted by global operation Infosys subsidiary named as source of Bank of America data leak LockBit shows no remorse for ransomware attack on children's hospitalThe data is stolen from victims by the affiliates before the ransomware payload is dropped, and before organizations are locked out of their systems, using StealBit, which is password-protected.
Once the exfiltration tool is deployed, it allows affiliates to select files from a specific folder or the entire computer, the authorities said.
The selected files are then sent back to LockBit via one of six proxy servers using a WebDAV header, which contains a new file name 33 characters long, beginning with a 0 or 1, the file path, computer name, and unique identifier.
The unique identifier is what allows affiliates to be attributed for each data theft and is what LockBit leadership uses to see who should be paid for any given job.
If StealBit can't connect to its hardcoded IP address used for sending the stolen data back to HQ, it will shut down and uninstall itself to evade detection.
The most common method of exfiltrating data is to run the data through the affiliate's own infrastructure before StealBit's, which authorities say is to prevent incident responders from locating the malware's servers.
In a final warning to LockBit sympathizers, the NCA said that all six of StealBit's proxy servers have been located and "destroyed" and that anyone "misguided enough" to try to bring them back online would be located.
"StealBit is an example of LockBit's attempt to offer a full 'one-stop shop' service to its affiliates, encryption, exfiltration, negotiation, publishing," the seized website reads.
"In essence, we have fully analyzed and understand how this malware and its associated infrastructure operates. We have located and destroyed the servers, and can locate them again should anyone be misguided enough to attempt its use." ®
.png)
 9 months ago
59
9 months ago
59 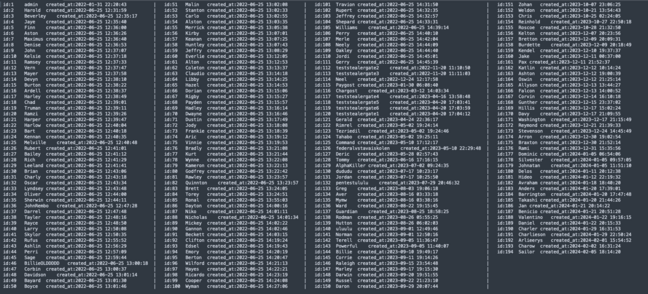















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·