BOOK THIS SPACE FOR AD
ARTICLE AD
Attackers used a newly discovered malware to backdoor Microsoft Exchange servers belonging to government and military organizations from Europe, the Middle East, Asia, and Africa.
The malware, dubbed SessionManager by security researchers at Kaspersky, who first spotted it in early 2022, is a malicious native-code module for Microsoft's Internet Information Services (IIS) web server software.
It has been used in the wild without being detected since at least March 2021, right after the start of last year's massive wave of ProxyLogon attacks.
"The SessionManager backdoor enables threat actors to keep persistent, update-resistant and rather stealth access to the IT infrastructure of a targeted organization," Kaspersky revealed on Thursday.
"Once dropped into the victim's system, cybercriminals behind the backdoor can gain access to company emails, update further malicious access by installing other types of malware or clandestinely manage compromised servers, which can be leveraged as malicious infrastructure."
SessionManager's capabilities include, among other features:
dropping and managing arbitrary files on compromised servers remote command execution on backdoored devices connecting to endpoints within the victim's local network and manipulating the network trafficIn late April 2022, while still investigating the attacks, Kaspersky found that most of the malware samples identified earlier were still deployed on 34 servers of 24 organizations (still running as late as June 2022).
Additionally, months after the initial discovery, they were still not flagged as malicious by "a popular online file scanning service."
After deployment, the malicious IIS module allows its operators to harvest credentials from system memory, collect information from the victims' network and infected devices, and deliver additional payloads (such as a PowerSploit-based Mimikatz reflective loader, Mimikatz SSP, ProcDump, and a legitimate Avast memory dump tool).
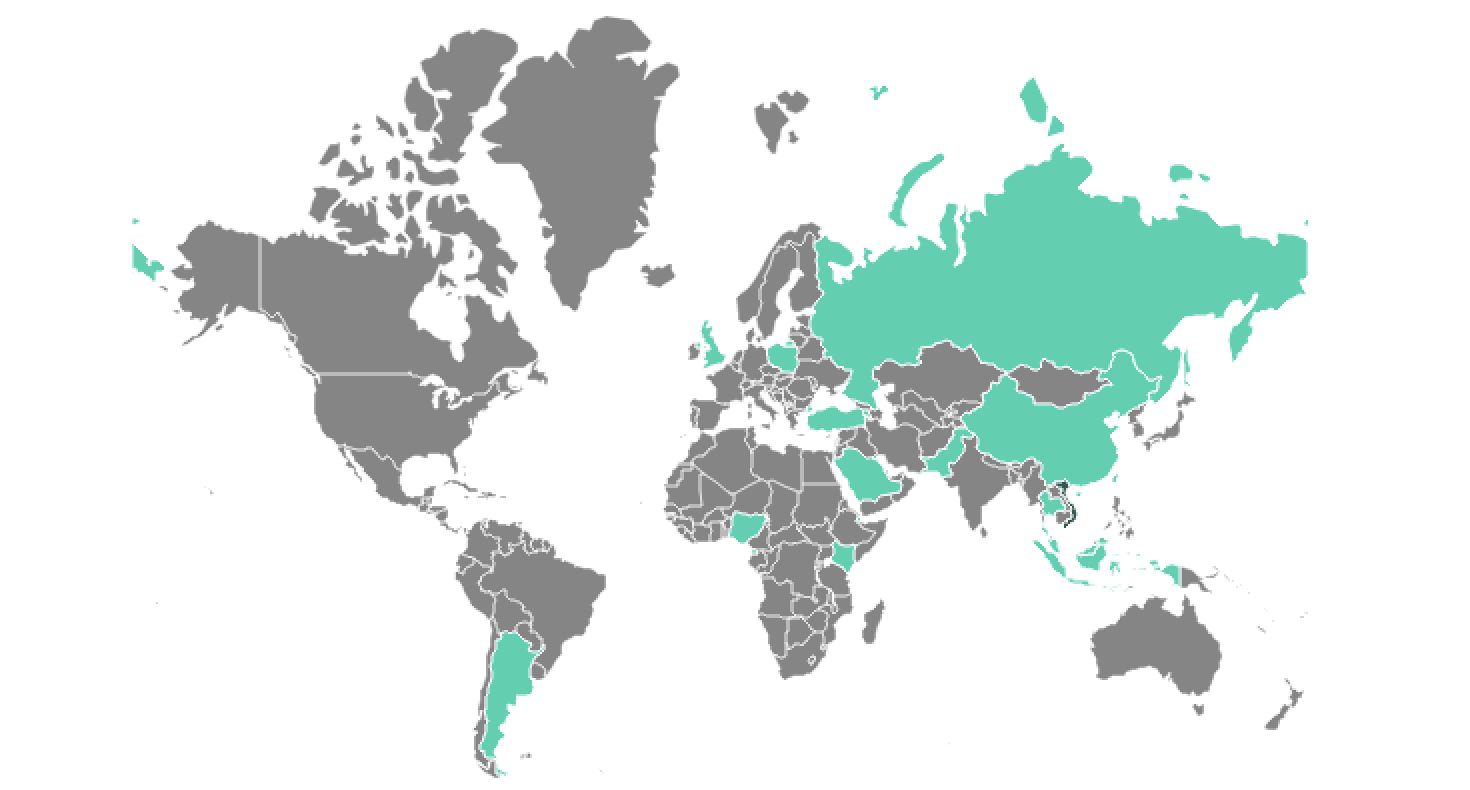 SessionManager targets (Kaspersky)
SessionManager targets (Kaspersky)"The exploitation of exchange server vulnerabilities has been a favorite of cybercriminals looking to get into targeted infrastructure since Q1 2021. The recently discovered SessionManager was poorly detected for a year and is still deployed in the wild," added Pierre Delcher, a Senior Security Researcher at Kaspersky's GReAT.
"In the case of Exchange servers, we cannot stress it enough: the past year's vulnerabilities have made them perfect targets, whatever the malicious intent, so they should be carefully audited and monitored for hidden implants, if they were not already."
Kaspersky uncovered the SessionManager malware while continuing to hunt for IIS backdoors similar to Owowa, another malicious IIS module deployed by attackers on Microsoft Exchange Outlook Web Access servers since late 2020 to steal Exchange credentials.
Gelsemium APT group links
Based on similar victimology and the use of the OwlProxy malware variant, Kaspersky's security experts believe the SessionManager IIS backdoor was leveraged in these attacks by the Gelsemium threat actor as part of a worldwide espionage operation.
This hacking group has been active since at least 2014, when some of its malicious tools were spotted by G DATA's SecurityLabs while investigating the "Operation TooHash" cyber-espionage campaign. In 2016, new Gelsemium indicators of compromise surfaced in a Verint Systems presentation during the HITCON conference.
Two years later, in 2018, VenusTech unveiled malware samples linked to the Operation TooHash and an unknown APT group, later tagged by Slovak internet security firm ESET as early Gelsemium malware versions.
ESET also revealed last year that its researchers linked Gelsemium to Operation NightScout, a supply-chain attack targeting the update system of the NoxPlayer Android emulator for Windows and macOS (with over 150 million users) to infect gamers' systems between September 2020 and January 2021.
Otherwise, the Gelsemium APT group is mainly known for targeting governments, electronics manufacturers, and universities from East Asia and the Middle East and mostly flying under the radar.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·