BOOK THIS SPACE FOR AD
ARTICLE AD
Azure Active Directory (Azure AD) now allows admins to issue time-limited passcodes that can be used to register new passwordless authentication methods, during Windows onboarding, or to recover accounts easier when losing credentials or FIDO2 keys.
Described by Microsoft as a Temporary Access Pass (TAP), they can be utilized to register authentication details (while signing for the first time or setting up a device) after enabling TAP in the Azure AD authentication method policy via the Azure portal.
TAPs can be created and deleted only by specific roles, including Global, Privileged Authentication, and Authentication administrators.
When updating the auth method policy to toggle on time-limited access pass, admins can configure their lifetime range between 10 minutes and 30 days, set the default lifetime, choose to issue one-time passcodes, and select the passcode length.
Detailed information on how to create, use, and delete temporary passcodes for Azure AD can be found in this Microsoft Docs support article.
"Temporary access pass can be used to securely register passwordless methods such as phone sign-in, phishing resistant methods like FIDO2, and can even assist in Windows onboarding (Azure AD Join and Windows Hello for Business)," Microsoft said.
"Temporary access pass makes recovery easier when you have lost or forgotten your strong authentication methods and need to sign in to register new authentication methods."
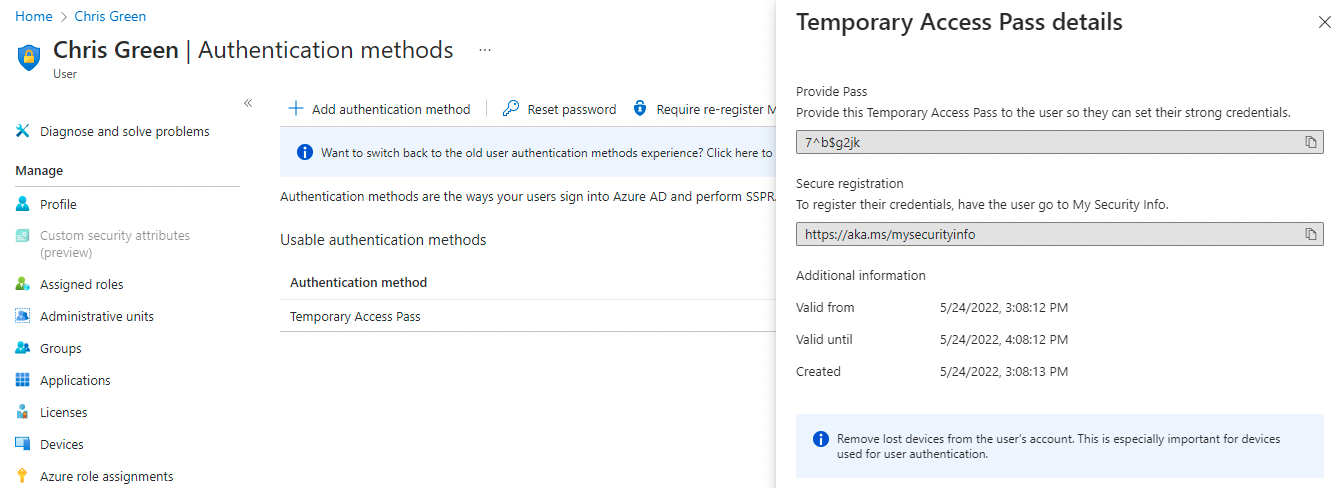 Azure AD TAP details (Microsoft)
Azure AD TAP details (Microsoft)Two months ago, Redmond announced it would enforce stricter secure default settings on all existing Azure Active Directory (Azure AD) tenants in June.
The announcement came after enabling security defaults for 60,000 new tenants in January 2020. Two years later, Microsoft says that over 30 million organizations worldwide are now protected by security defaults that enforce modern authentication requirements (including passwordless sign-ins) and multifactor authentication (MFA).
"When complete, this rollout will protect an additional 60 million accounts (roughly the population of the United Kingdom!) from the most common identity attacks," explained Alex Weinert, Director of Identity Security at Microsoft.
Those who don't want security defaults enabled for their orgs can disable them easily on the Microsoft 365 admin center or through the Azure Active Directory properties.
However, this might be a bad idea given that organizations with security defaults experience 80 percent fewer breaches and MFA prevents over 99.9% of account compromise attacks, according to Weinert.
To put things into perspective, Microsoft also revealed in February that Office 365 and Azure AD customers had been targeted by billions of phishing emails and brute force attacks, attempts made significantly more challenging when MFA and passwordless authentication are enabled.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·