BOOK THIS SPACE FOR AD
ARTICLE ADMillions of iOS and Android users are at risk after Symantec discovered that popular apps contain hardcoded, unencrypted cloud keys. This security flaw could lead to unauthorized access, data breaches, and service disruptions.
Research conducted by cybersecurity experts at Symantec has revealed that popular apps on both Android and iOS platforms contain hardcoded, unencrypted cloud service credentials, putting millions of users’ sensitive data and backend services at risk of unauthorized access and potential data breaches.
The issue comes from developers embedding access and secret keys directly in the app’s code instead of using secure storage methods. This makes it easy for attackers to access sensitive data, steal user information, or disrupt services.
Among the affected Android apps, Pic Stitch: Collage Maker, with over 5 million downloads, and Meru Cabs, Sulekha Business, and ReSound Tinnitus Relief, each with hundreds of thousands of downloads, were found to contain hardcoded AWS and Azure credentials, respectively. These credentials grant access to critical cloud storage and other backend services.
On the iOS side, popular apps like Crumbl (over 3.9 million ratings), Eureka: Earn Money for Surveys (402.1K ratings), and Videoshop – Video Editor (357.9K ratings) were also found to have hardcoded AWS credentials, including access keys and even WebSocket Secure (WSS) endpoints, further simplifying potential attacks.
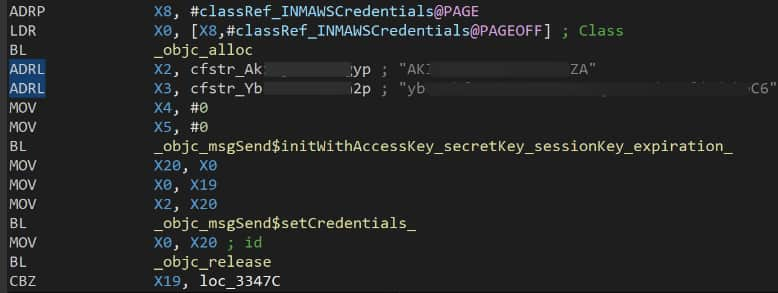 Eureka IDA code with hardcoded AWS credentials (Via Symantec)
Eureka IDA code with hardcoded AWS credentials (Via Symantec)
Full list of impacted apps on iOS and Android
Crumbl (over 3.9 million ratings) Meru Cabs (over 5 million downloads) Sulekha Business (over 500,000 downloads) Videoshop – Video Editor (over 357,000 ratings) ReSound Tinnitus Relief (over 500,000 downloads) Pic Stitch: Collage Maker (over 5 million downloads) Eureka: Earn Money for Surveys (over 402,000 ratings)This issue, found on both Android and iOS, is a serious concern. It could lead to anything from individual data breaches to major service disruptions. Symantec’s findings show the urgent need for developers to follow security best practices.
To mitigate these risks, developers are advised to follow best practices for managing sensitive information within their applications. These include using environment variables, implementing secrets management, encrypting sensitive data, conducting regular code reviews and audits, and automating security scanning.
“This repeated pattern of insecure credential management across multiple apps underscores the critical need for developers to prioritize security in the mobile app development lifecycle,” said a Symantec spokesperson.
For users, Symantec advises installing reputable security software, downloading apps only from trusted sources, keeping software updated, carefully reviewing app permissions, and regularly backing up important data. These precautions can help mitigate the risks associated with insecure apps while developers work to address these critical vulnerabilities.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·