Cybersecurity researchers have disclosed details of the latest version of the Chaos ransomware line, dubbed Yashma.
"Though Chaos ransomware builder has only been in the wild for a year, Yashma claims to be the sixth version (v6.0) of this malware," BlackBerry research and intelligence team said in a report shared with The Hacker News.
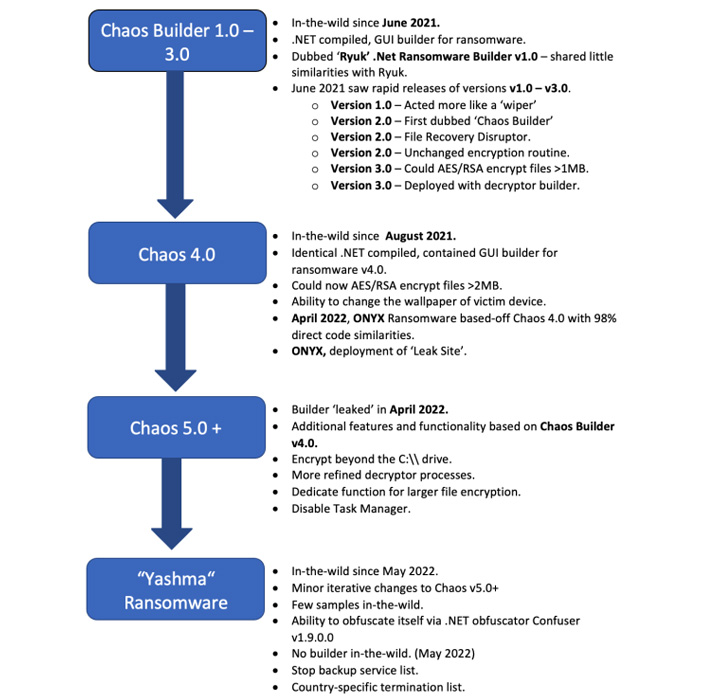
Chaos is a customizable ransomware builder that emerged in underground forums on June 9, 2021, by falsely marketing itself as the .NET version of Ryuk despite sharing no such overlaps with the notorious counterpart.
The fact that it's offered for sale also means that any malicious actor can purchase the builder and develop their own ransomware strains, turning it into a potent threat.
It has since undergone five successive iterations aimed at improving its functionalities: version 2.0 on June 17, version 3.0 on July 5, version 4.0 on August 5, and version 5.0 in early 2022.
While the first three variants of Chaos functioned more like a destructive trojan than traditional ransomware, Chaos 4.0 expanded its encryption process by increasing the upper limit of files that can be encrypted to 2.1MB.
Version 4.0 has also been actively weaponized by a ransomware collective known as Onyx as of April 2022 by making use of an updated ransom note and a refined list of file extensions that can be targeted.
"Chaos 5.0 attempted to resolve the largest problem of previous iterations of the threat, namely that it was unable to encrypt files larger than 2MB without irretrievably corrupting them," the researchers explained.
Yashma is the latest version to join this list, featuring two new improvements, including the ability to stop execution based on a victim's location and terminate various processes associated with antivirus and backup software.
"Chaos started as a relatively basic attempt at a .NET compiled ransomware that instead functioned as a file-destructor or wiper," the researchers said. "Over time it has evolved to become a full-fledged ransomware, adding additional features and functionality with each iteration."
The development comes as a Chaos ransomware variant has been spotted siding with Russia in its ongoing war against Ukraine, with the post-encryption activity leading to an alert containing a link that directs to a website with pro-Russian messages.
"The attacker has no intention of providing a decryption tool or file recovery instructions for its victims to recover their affected files," Fortinet FortiGuard Labs disclosed last week, adding it "makes the malware a file destroyer."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
158
2 years ago
158 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·