An unknown threat actor has been observed leveraging a malicious Windows kernel driver in attacks likely targeting the Middle East since at least May 2020.
Fortinet Fortiguard Labs, which dubbed the artifact WINTAPIX (WinTapix.sys), attributed the malware with low confidence to an Iranian threat actor.
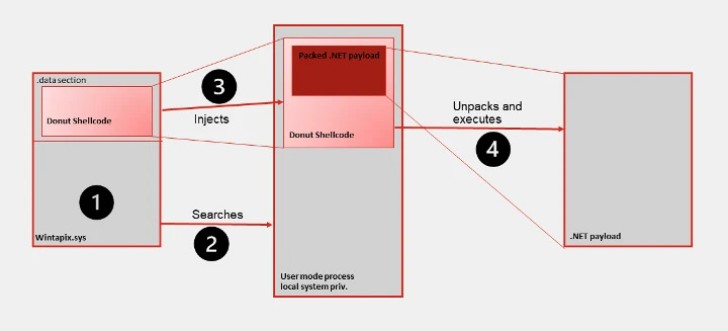
"WinTapix.sys is essentially a loader," security researchers Geri Revay and Hossein Jazi said in a report published on Monday. "Thus, its primary purpose is to produce and execute the next stage of the attack. This is done using a shellcode."
Samples and telemetry data analyzed by Fortinet show that the campaign's primary focus is on Saudi Arabia, Jordan, Qatar, and the United Arab Emirates. The activity has not been tied to a known threat actor or group.
By using a malicious kernel mode driver, the idea is to subvert or disable security mechanisms and gain entrenched access to the targeted host.
Such drivers run within the kernel memory and can, therefore, perform any operation, including altering critical security mechanisms and running arbitrary code with the highest privileges.
In other words, it offers a stealthy way to infiltrate deeper into the targeted system, maintain persistence, and execute additional payloads or commands as part of the threat actor's multi-stage attack.
A key security measure to mitigate against malicious drivers is Driver Signature Enforcement, which ensures that only drivers signed by Microsoft can be loaded on the system. The tech giant also maintains driver block rules to protect against known vulnerable drivers.
WinTapix.sys, on the other hand, comes with an invalid signature, indicating that the threat actor will have to first load a legitimate but vulnerable driver in order to launch WINTAPIX.
UPCOMING WEBINAR
Zero Trust + Deception: Learn How to Outsmart Attackers!
Discover how Deception can detect advanced threats, stop lateral movement, and enhance your Zero Trust strategy. Join our insightful webinar!
But once it's loaded in the kernel, WinTapix.sys is configured to inject an embedded shellcode into an appropriate user mode process that, in turn, executes an encrypted .NET payload.
WINTAPIX, besides embedding the shellcode created using the open source Donut project, establishes persistence by means of Windows Registry modifications that allows it to be loaded even when the machine is booted in Safe Mode.
For its part, the .NET malware is equipped with backdoor and proxy features to execute commands, carry out file download and upload, and function as a proxy to pass data between two communication endpoints.
"Since Iranian threat actors are known to exploit Exchange servers to deploy additional malware, it is also possible that this driver has been employed alongside Exchange attacks," the researchers said.
"To that point, the compilation time of the drivers is also aligned with times when Iranian threat actors were exploiting Exchange server vulnerabilities."
The development comes as the ALPHV (aka BlackCat or Noberus) ransomware group has been observed taking advantage of a malicious signed driver to impair security defenses and escape detection for extended periods of time.
The driver in question, ktgn.sys, is an updated version of POORTRY that's signed using a stolen or leaked cross-signing certificate, cybersecurity firm Trend Micro said in a report.
POORTRY is the name assigned to a Windows kernel driver that comes with capabilities to terminate security software. Late last year, it was disclosed as used by ransomware gangs and a threat actor known as UNC3944 (aka Roasted 0ktapus and Scattered Spider).
"Malicious actors that are actively seeking high-privilege access to the Windows operating system use techniques that attempt to combat the increased protection on users and processes via endpoint protection platform (EPP) and endpoint detection and response (EDR) technologies," Trend Micro said.
"These malicious actors also tend to possess enough financial resources to either purchase rootkits from underground sources or to buy code-signing certificates to build a rootkit."
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
.png)
 1 year ago
113
1 year ago
113 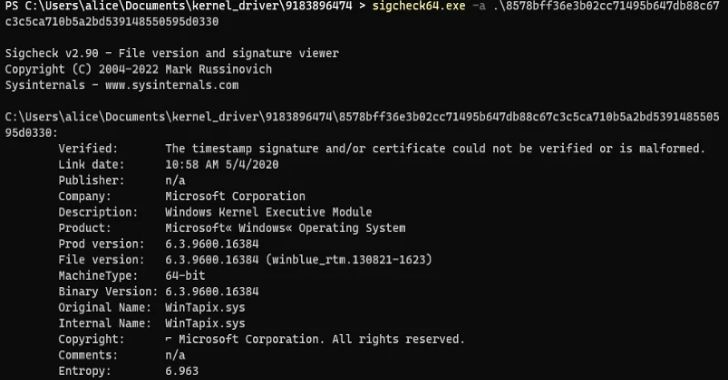
.jpg)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·