BOOK THIS SPACE FOR AD
ARTICLE ADAn international law enforcement operation, led by the United States, Europol, and the Netherlands, has successfully dismantled the infrastructure behind the notorious RedLine and META infostealer malware. Discover how these cyberattacks steal sensitive information and the impact they have on individuals and businesses worldwide.
An international law enforcement operation has successfully dismantled the infrastructure behind two notorious infostealer malware strains: RedLine and Meta. The operation, codenamed “Operation Magnus,” was led by the Dutch National Police, the U.S. Department of Justice (DOJ) and supported by Europol.
The investigation involved law enforcement agencies from across the globe, including Belgium (Belgian Federal Police, Belgian Federal Prosecutor’s Office), Australia (the Australian Federal Police), Portugal (Polícia Judiciária), and the United Kingdom (National Crime Agency).
Other US agencies involved in this operation include the FBI, Naval Criminal Investigative Service, IRS Criminal Investigation, Defense Criminal Investigative Service, and Army Criminal Investigation Division. These agencies collaborated under a Joint Cybercrime Action Taskforce (“JCAT”) Operation Magnus.
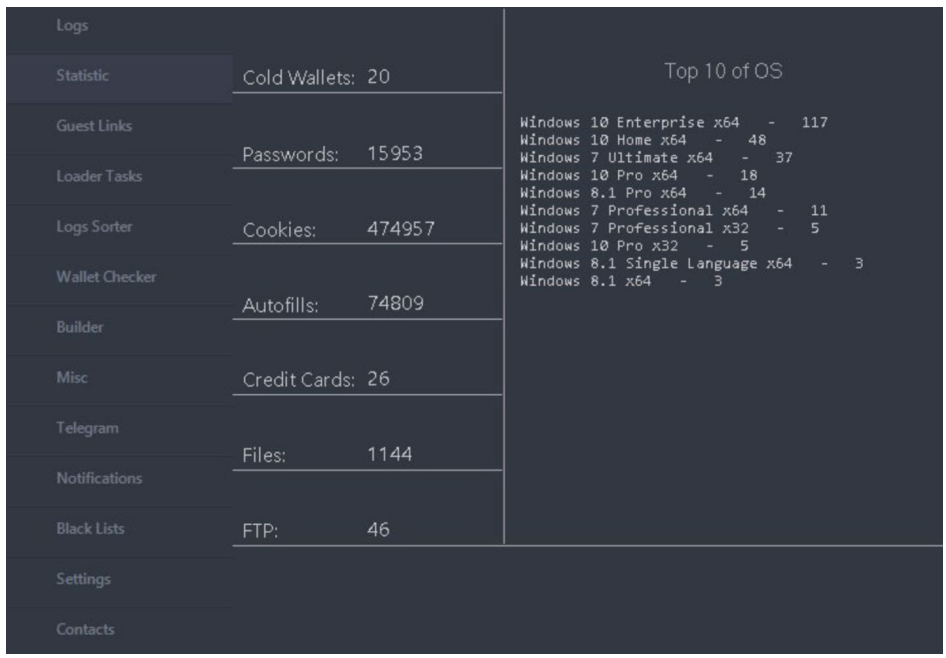
This operation resulted in full access (PDF) to the servers hosting the malware’s infrastructure, including source code, license servers, user data, and seizing domains and Telegram accounts. Authorities have created a dedicated website to provide resources for victims and the public
For your information, Infostealers are a type of malware designed to steal sensitive information from victims’ devices, such as login credentials, passwords, and credit card details. These stolen credentials are often sold on underground markets, enabling further cyberattacks and fraudulent activities.
RedLine and META are designed to infiltrate victim computers and steal sensitive information. This stolen data, often referred to as “logs,” can include usernames, passwords, financial information, and even cryptocurrency wallet details. Criminals use these stolen credentials for a variety of nefarious purposes, including launching further attacks, committing fraud, or bypassing multi-factor authentication (MFA).
Investigations revealed RedLine and META may have infected millions of computers worldwide. Estimates suggest RedLine alone might be one of the most prevalent malware variants globally. Law enforcement has identified millions of unique credentials stolen by the malware, including usernames, passwords, and financial data.
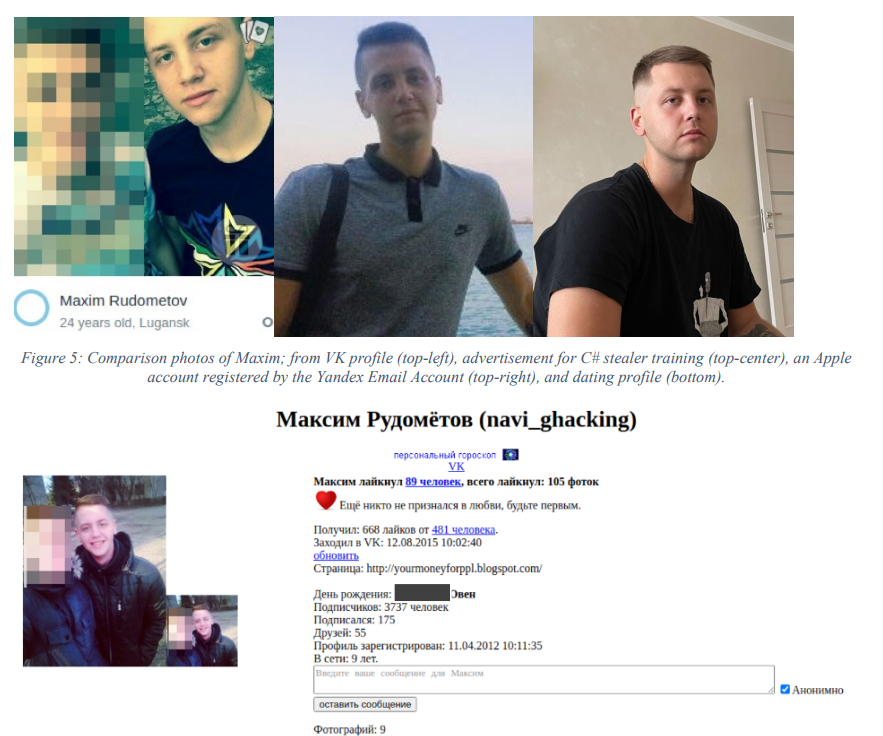
As part of Operation Magnus, authorities unsealed a criminal complaint (PDF) against Maxim Rudometov, believed to be a developer and administrator of RedLine. The complaint accuses Rudometov of managing RedLine’s infrastructure, receiving payments through cryptocurrency accounts, and possessing the malware itself. He faces charges including access device fraud, conspiracy to commit computer intrusion, and money laundering, and if convicted, he could face a maximum sentence of 10 years in prison.
Operation Magnus serves as a powerful example of international cooperation in combating cybercrime. By dismantling the RedLine and META infrastructure, law enforcement has significantly disrupted the activities of cybercriminals who rely on stolen data for their illicit operations. However, the ever-evolving nature of cybercrime necessitates continued vigilance and cooperation between law enforcement and cybersecurity experts.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·