BOOK THIS SPACE FOR AD
ARTICLE ADStay alert against Temu phishing scams: Cybersecurity experts warn of scammers using fake giveaways to steal credentials. Over 800 new ‘Temu’ domains registered in the past 3 months.
Temu is the latest brand chosen by scammers for their phishing scams. Checkpoint’s Harmony Email’s cybersecurity researcher Jeremy Fuchs, has noted that hackers are using Temu’s giveaway rewards to entice users to give away their credentials, with over 800 new domains registered as “Temu” in the last three months.
For your information, Temu is an international e-commerce store having 40% of its user base in the USA. It offers discounted goods shipped directly to consumers. Temu was launched in 2022 and is available in 48 countries, including Europe, the Middle East, Southeast Asia, and Australia.
As of February 7, 2024, it is the number one shopping app on Google Play Store and second on the Apple App Store. The app’s most frequent shoppers are senior citizens, mostly 59 and above.
The sample phishing email identified by researchers claims to be from Temu Rewards. However, if you look closely, it is sent by an unrelated email address- onmicrosoft.com. The email contains a blank image and a link to a credential harvesting page. The threat actors try to attract recipients by informing them that they have won.
According to Checkpoint’s blog post, the email has Temu’s name as the sender. However, if the user realizes the sender address isn’t related to Temu or the links don’t lead to a Temu page, they’ll stay away from this scam. The email should raise suspicion as it is sent from a generic address on onmicrosoft (.) com, and the image does not load.
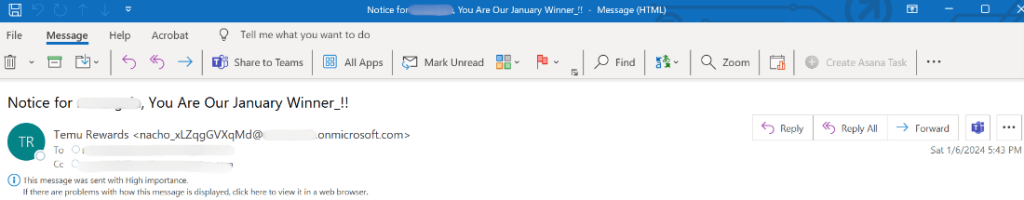 One of the phishing emails used in the scam (Check Point)
One of the phishing emails used in the scam (Check Point)
Brand Names and Phishing
This isn’t the first time threat actors have exploited brand names and the latest trends to steal credentials or other sensitive information from innocent users.
In November 2022, Hackread reported that Cyjax researchers discovered a sophisticated phishing campaign targeting over 400 brands across various sectors. The scammers, likely having Chinese affiliations, used 42,000 domains to distribute malware and generate ad revenue with at least 24,000 survey/landing domains used to promote the scam.
Cybersecurity researchers at Bloster AI recently discovered a USPS Delivery phishing campaign utilizing advanced techniques to target victims in the US. Bolster’s CheckPhish detected over 3,000 phishing domains mimicking Walmart. The campaign tricked consumers into thinking they had failed deliveries and late payments. Threat actors have improved their attack tactics, transitioning from deceptive messages to luring victims into downloading financial or banking data-stealing apps.
A phishing scam targeting Meta Platforms, Inc. business owners to steal their email addresses and passwords, leading to the takeover of their Facebook page, profile, and financial information was discovered in January 2024. The scam used Meta Platforms’ authority to create urgency and legitimacy.
Temu and Cybersecurity
Temu itself has faced several cybersecurity-related issues, including allegations of collecting user and device data such as text messages and banking information.
In November 2023, a class-action lawsuit was filed in the United States, alleging that the company had unlawfully collected its customers’ data. Furthermore, another report surfaced, implicating Temu in the unauthorized disclosure of customer data, particularly in connection with data purportedly appearing for sale on the dark web after customers make purchases through the app.
Nevertheless, it’s crucial to emphasize basic security measures with users and ensure that all threats can be stopped, both simple and sophisticated, especially scams like these, which exploit users’ trust in big brands.
Additionally, to protect against phishing attacks, security professionals must implement AI-based security, robust URL protection, and full-suite security to scan documents and files.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·