A new research undertaken by a group of academics from the University of California San Diego has revealed for the first time that Bluetooth signals can be fingerprinted to track smartphones (and therefore, individuals).
The identification, at its core, hinges on imperfections in the Bluetooth chipset hardware introduced during the manufacturing process, resulting in a "unique physical-layer fingerprint."
"To perform a physical-layer fingerprinting attack, the attacker must be equipped with a Software Defined Radio sniffer: a radio receiver capable of recording raw IQ radio signals," the researchers said in a new paper titled "Evaluating Physical-Layer BLE Location Tracking Attacks on Mobile Devices."
The attack is made possible due to the ubiquitous nature of Bluetooth Low Energy (BLE) beacons that are continuously transmitted by modern devices to enable crucial functions such as contact tracing during public health emergencies.
The hardware defects, on the other hand, stem from the fact that both Wi-Fi and BLE components are often integrated together into a specialized "combo chip," effectively subjecting Bluetooth to the same set of metrics that can be used to uniquely fingerprint Wi-Fi devices: carrier frequency offset and IQ imbalance.
Fingerprinting and tracking a device then entails extracting CFO and I/Q imperfections for each packet by computing the Mahalanobis distance to determine "how close the features of the new packet" are to its previously recorded hardware imperfection fingerprint.
"Also, since BLE devices have temporarily stable identifiers in their packets [i.e., MAC address], we can identify a device based on the average over multiple packets, increasing identification accuracy," the researchers said.
That said, there are several challenges to pulling off such an attack in an adversarial setting, chief among them being that the ability to uniquely identify a device depends on the BLE chipset used as well as the chipsets of other devices that are in close physical proximity to the target.
Other critical factors that could affect the readings include device temperature, differences in BLE transmit power between iPhone and Android devices, and the quality of the sniffer radio used by the malicious actor to execute the fingerprinting attacks.
"By evaluating the practicality of this attack in the field, particularly in busy settings such as coffee shops, we found that certain devices have unique fingerprints, and therefore are particularly vulnerable to tracking attacks, others have common fingerprints, they will often be misidentified," the researchers concluded.
"BLE does present a location tracking threat for mobile devices. However an attacker's ability to track a particular target is essentially a matter of luck."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
127
2 years ago
127 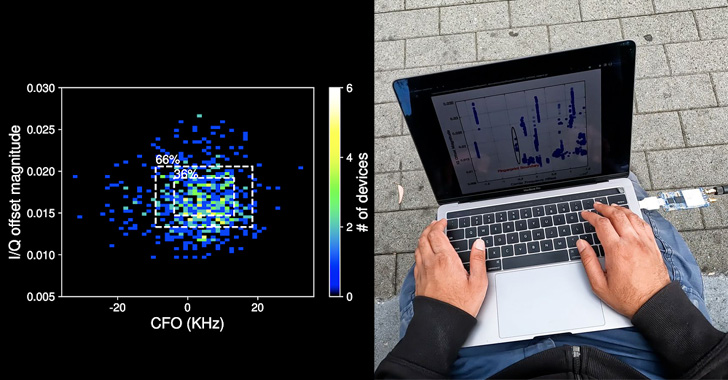

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·