A now-patched security flaw has been disclosed in the Galaxy Store app for Samsung devices that could potentially trigger remote command execution on affected phones.
The vulnerability, which affects Galaxy Store version 4.5.32.4, relates to a cross-site scripting (XSS) bug that occurs when handling certain deep links. An independent security researcher has been credited with reporting the issue.
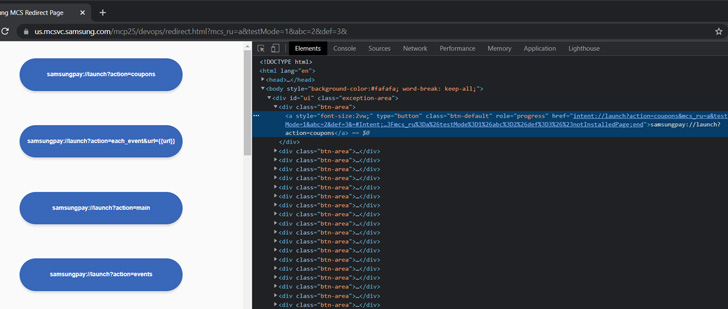
"Here, by not checking the deep link securely, when a user accesses a link from a website containing the deeplink, the attacker can execute JS code in the webview context of the Galaxy Store application," SSD Secure Disclosure said in an advisory posted last week.
XSS attacks allow an adversary to inject and execute malicious JavaScript code when visiting a website from a browser or another application.
The issue identified in the Galaxy Store app has to do with how deep links are configured for Samsung's Marketing & Content Service (MCS), potentially leading to a scenario where arbitrary code injected into the MCS website could lead to its execution.
This could then be leveraged to download and install malware-laced apps on the Samsung device when visiting the link.
"To be able to successfully exploit the victim's server, it is necessary to have HTTPS and CORS bypass of chrome," the researchers noted.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
128
2 years ago
128 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·