Threat hunting is the process of looking for malicious activity and its artifacts in a computer system or network. Threat hunting is carried out intermittently in an environment regardless of whether or not threats have been discovered by automated security solutions. Some threat actors may stay dormant in an organization's infrastructure, extending their access while waiting for the right opportunity to exploit discovered weaknesses.
Therefore it is important to perform threat hunting to identify malicious actors in an environment and stop them before they achieve their ultimate goal.
To effectively perform threat hunting, the threat hunter must have a systematic approach to emulating possible adversary behavior. This adversarial behavior determines what artifacts can be searched for that indicate ongoing or past malicious activity.
MITRE ATT&CK
Over the years, the security community has observed that threat actors have commonly used many tactics, techniques, and procedures (TTPs) to infiltrate and pivot across networks, elevate privileges, and exfiltrate confidential data. This has led to the development of various frameworks for mapping the activities and methods of threat actors. One example is the MITRE ATT&CK framework.
MITRE ATT&CK is an acronym that stands for MITRE Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK). It is a well-documented knowledge base of real-world threat actor actions and behaviors. MITRE ATT&CK framework has 14 tactics and many techniques that identify or indicate an attack in progress. MITRE uses IDs to reference the tactic or technique employed by an adversary.
The Wazuh unified XDR and SIEM platform
Wazuh is an open source unified XDR and SIEM platform. The Wazuh solution is made up of a single universal agent that is deployed on monitored endpoints for threat detection and automated response. It also has central components (Wazuh server, indexer, and dashboard) that analyze and visualize the security events data collected by the Wazuh agent. It protects on-premises and cloud workloads.
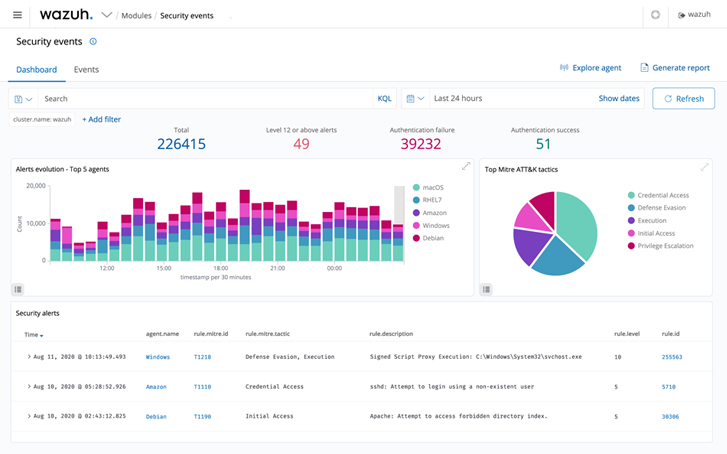 |
| Figure 1: Wazuh security event dashboard |
Threat hunting with Wazuh
Threat hunters use various tools, processes, and methods to search for malicious artifacts in an environment. These include but are not limited to using tools for security monitoring, file integrity monitoring, and endpoint configuration assessment.
Wazuh offers robust capabilities like file integrity monitoring, security configuration assessment, threat detection, automated response to threats, and integration with solutions that provide threat intelligence feeds.
Wazuh MITRE ATT&CK module
Wazuh comes with the MITRE ATT&CK module out-of-the-box and threat detection rules mapped against their corresponding MITRE technique IDs. This module has four components which are:
a. The intelligence component of the Wazuh MITRE ATT&CK module: Contains detailed information about threat groups, mitigation, software, tactics, and techniques used in cyber attacks. This component helps threat hunters to identify and classify different TTPs that adversaries use.
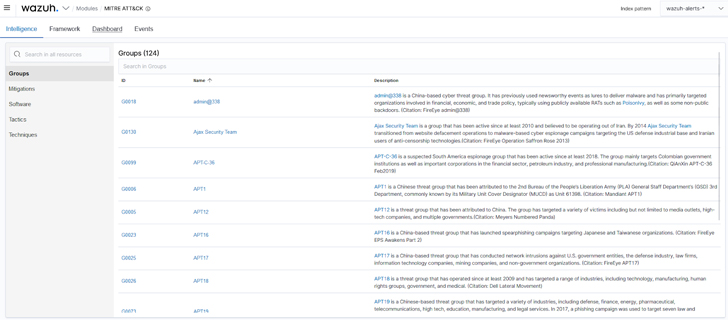 |
| Figure 2: Wazuh MITRE ATT&CK Intelligence |
b. The framework component of the Wazuh MITRE ATT&CK module: Helps threat hunters narrow down threats or compromised endpoints. This component uses specific techniques to see all the events related to that technique and the endpoints where these events happened.
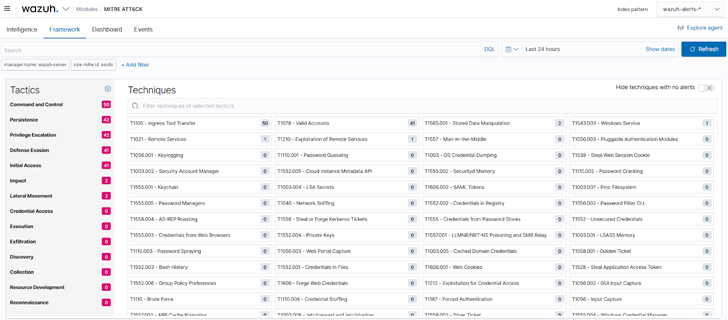 |
| Figure 3: Wazuh MITRE ATT&CK framework |
c. The dashboard component of the MITRE ATT&CK module: Helps to summarize all events into charts to assist threat hunters in having a quick overview of MITRE related activities in an infrastructure.
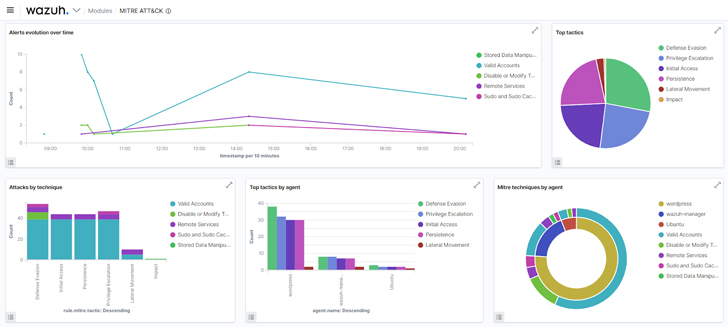 |
| Figure 4: Wazuh MITRE ATT&CK dashboard |
d. The Wazuh MITRE ATT&CK events component: Displays events in real-time, with their respective MITRE IDs, to better understand each reported alert.
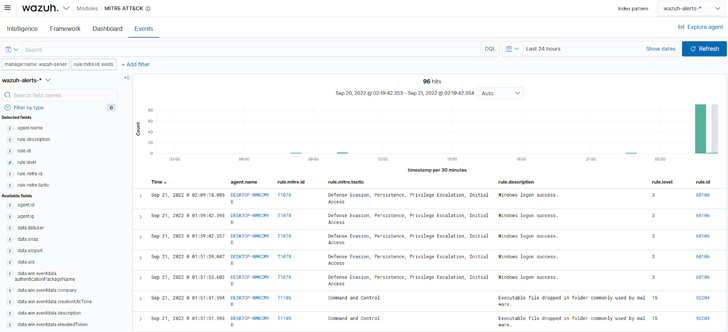 |
| Figure 5: Wazuh MITRE ATT&CK events |
Wazuh rules and decoders
Wazuh has out-of-the-box rules and decoders to parse security and runtime data generated from different sources. Wazuh supports rules for different technologies (e.g., Docker, CISCO, Microsoft Exchange), which have been mapped to their appropriate MITRE IDs. Users can also create custom rules and decoders and map each rule with its appropriate MITRE tactic or technique. This blog post shows an example of leveraging MITRE ATT&CK and Wazuh custom rules to detect an adversary.
Security Configuration Assessment (SCA) module
The Wazuh SCA module performs periodic scans in endpoints to detect system and application misconfigurations. It can also be used to scan for indicators of compromise, like malicious files and folders that have been created by malware. Analyzing software inventories, services, misconfigurations, and changes in the configuration on an endpoint can help threat hunters detect attacks underway.
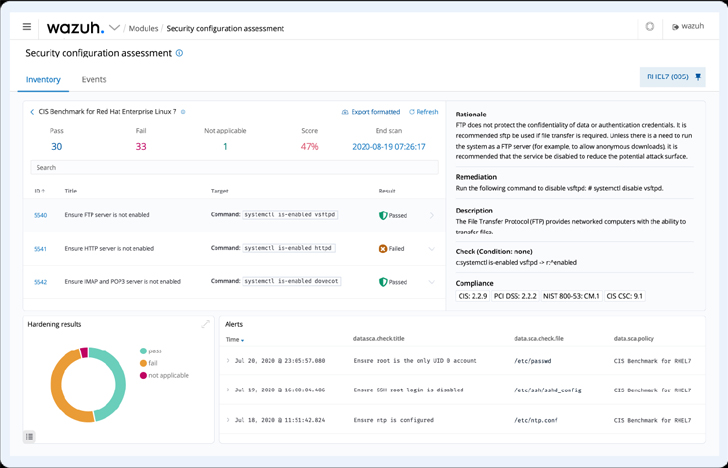 |
| Figure 6: Wazuh SCA dashboard |
Integration with threat intelligence solutions
Due to its open source nature, Wazuh provides an opportunity to integrate with threat intelligence APIs and other security solutions. Wazuh integrates with open source threat intelligence platforms like Virustotal, URLHaus, MISP, and AbuseIPDB to name a few. Depending on the integration, relevant alerts appear in the Wazuh dashboard. Specific information, such as IP addresses, file hashes, and URLs, can be queried using filters on the Wazuh dashboard.
File integrity monitoring
File integrity monitoring (FIM) is used to monitor and audit sensitive files and folders on endpoints. Wazuh provides an FIM module that monitors and detects changes in specified directories or files on an endpoint's filesystem. The FIM module can also detect when files introduced to endpoints match hashes of known malware.
Wazuh archives
Wazuh archives can be enabled to collect and store all security events ingested from monitored endpoints. This feature assists threat hunters by providing them with data that can be used to create detection rules and stay ahead of threat actors. Wazuh archives are also helpful in meeting regulatory compliance where audit log history is required.
Conclusion
The MITRE ATT&CK framework helps to properly classify and identify threats according to discovered TTPs. Wazuh uses its dedicated MITRE ATT&CK components to display information about how security data from endpoints correspond to TTPs. The threat hunting capabilities of Wazuh help cybersecurity analysts to detect apparent cyber attacks as well as underlying compromises to infrastructure.
Wazuh is a free and open source platform that can be used by organizations with cloud and on-premises infrastructure. Wazuh has one of the fastest-growing open source community in the world, where learning, discussions, and support is offered at zero cost. Check out this documentation to get started with Wazuh.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 2 years ago
168
2 years ago
168 















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·