BOOK THIS SPACE FOR AD
ARTICLE AD
Microsoft is warning that toll fraud malware is one of the most prevalent threats on Android and that it is evolving with features that allow automatic subscription to premium services.
Toll fraud is a subset of billing fraud, where the threat actor tricks victims into calling or sending an SMS to a premium number.
The difference is that toll fraud does not work over WiFi and forces the devices to connect to the mobile operator’s network.
Toll fraud overview
In a report today, Microsoft shares technical details on how toll fraud malware works and how it can be prevented on Android.
Toll fraud works over the Wireless Application Protocol (WAP), which allows consumers to subscribe to paid content and add the charge to their phone bill.
This requires a connection over the mobile network and the customer to click on a subscription button. Some services send a one-time password (OTP) for customers to confirm their choice.
Malware that enables toll fraud does all this automatically by initiating the fraudulent subscription, intercepting OTPs, and suppressing notifications that might alert the victim.
Microsoft identified several steps in the process that typically happens with users being completely unaware:
Disable the Wi-Fi connection or wait for the user to switch to a mobile network Silently navigate to the subscription page Auto-click the subscription button Intercept the OTP (if applicable) Send the OTP to the service provider (if applicable) Cancel the SMS notifications (if applicable)Disabling WiFi connection
The malware starts by collecting data on the subscriber’s country and mobile network, for which Android requires no permission from the user.
A key step is to disable the WiFi connection and force the device to use the operator’s network. On Android 9 (API level 28) or lower, this is possible with a normal protection permission level.
For a higher API level, there is the ‘requestNetwork’ function that falls under the CHANGE_NETWORK_STATE permission, which also comes with a normal protection level.
Microsoft showed this in sample code from Joker malware that has constantly found its way into Google’s Play Store for more than half a decade.
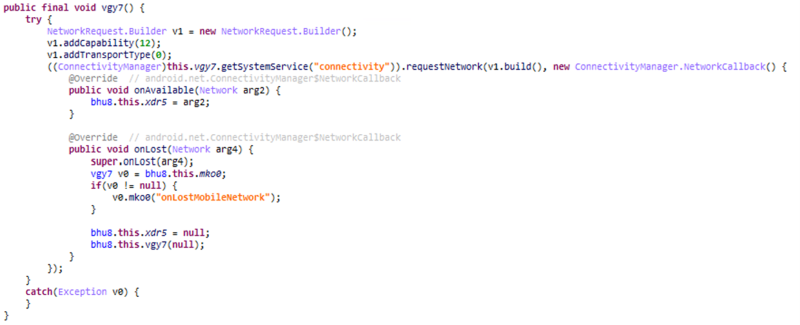 requestNetwork function abused by Joker malware source: Microsoft
requestNetwork function abused by Joker malware source: MicrosoftToll fraud malware then uses the ‘NetworkCallbak’ to monitor the network status and get the ‘networktype’ variable to bind the process to a specific network, thus forcing the device to ignore an available WiFi connection and use the mobile operator’s.
The only way for the user to avoid this is to manually disable mobile data.
If the victim’s mobile carrier is on the target list, the malware proceeds to fetch a list of websites that provide premium services and tries to subscribe to them automatically.
While there are multiple subscription scenarios, users normally click on an HTML element and then send a verification code to the server.
“For the malware to do this automatically, it observes the page loading progress and injects JavaScript code designed to click HTML elements that initiate the subscription. As the user can only subscribe once to one service, the code also marks the HTML page using a cookie to avoid duplicate subscriptions” - Microsoft
Microsoft notes that sometimes additional verification may be required. Toll fraud malware samples the company analyzed have methods to achieve that, too.
Some operators finish the subscription only after checking that the user authorized it via an OTP code delivered over SMS, HTTP, or USSD (Unstructured Supplementary Service Data), with the first two being the more popular.
Android malware stealing SMS data is nothing special and collecting messages received over the HTML protocol the code needs to be parsed for strings that indicate a verification token.
Once the threat actor obtains the authorization code, they are free to complete the subscription to the selected premium service.
This is not enough, though, since victims could get notifications about the subscription, so these need to be suppressed.
“Since API level 18, an application that extends the NotificationListenerService is authorized to suppress notifications triggered from other applications” - Microsoft
Malware developers have a subset of three API calls they can abuse to silence SMS notifications from other applications:
cancelAllNotifications() to inform the notification manager to dismiss all notifications cancelNotification(String key) to inform the notification manager to dismiss a single notification cancelNotifications(String [] keys) to inform the notification manager to dismiss multiple notifications at onceDevelopers of toll fraud malware also implement mechanisms to keep the malicious behavior as discreet as possible. One way is to keep the malware inert if the mobile network of the infected device is not on the list.
Another method is to use dynamic code loading, which allows certain code to load only if specific conditions are met. This makes spotting the malware more difficult, especially on static analysis.
Keeping toll fraud malware off your device comes down to checking that the source for downloading your Android source is trustworthy, such as Google’s Play Store/
Additionally, looking at the permissions requested upon installation is a good way to reduce the risk of malware running rampant on your device as well as protect your privacy.
Microsoft also recommends users avoid allowing apps to read or send SMS, access to notifications, or accessibility unless these permissions are needed for normal functioning.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·