BOOK THIS SPACE FOR AD
ARTICLE ADBest bug bounty research tools
Bug bounty research involves finding and reporting security issues in software systems, and there are tools available to help with this process. Here are some user-friendly tools commonly used in bug bounty research:
1. Burp Suite: This tool helps you test the security of web applications. It looks for vulnerabilities like malicious code injections and helps you understand how attackers might exploit those weaknesses.
2. OWASP ZAP: ZAP is another tool for testing web applications. It helps you find vulnerabilities such as cross-site scripting (XSS) or insecure configurations that could lead to unauthorized access.
3. Nmap: Nmap is a tool that scans networks to find open ports, services, and potential vulnerabilities. It helps you gather information about the target system, like what's running and how it's set up.
4. Metasploit Framework: This powerful tool is like a Swiss Army knife for security testing. It helps you discover and exploit vulnerabilities in different systems and applications to understand how they can be compromised.
5. Nikto: Nikto is a user-friendly tool that scans web servers to find known vulnerabilities and misconfigurations. It's helpful for identifying common security issues in web applications.
6. Nessus: Nessus is a user-friendly vulnerability scanner that can detect weaknesses in systems and applications. It scans for vulnerabilities and generates detailed reports to help you understand and fix the issues.
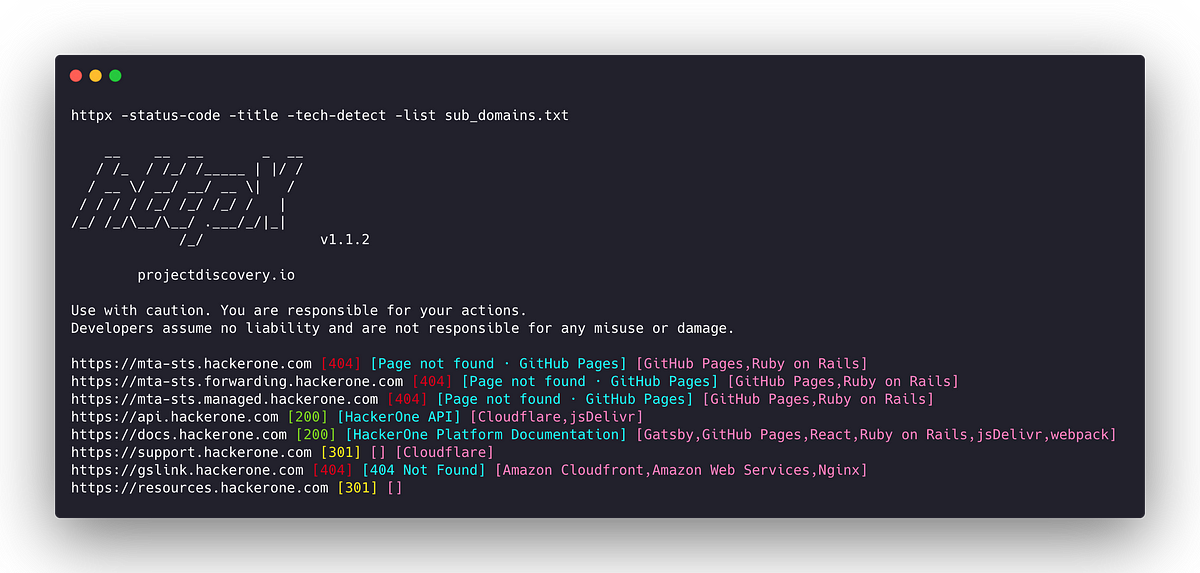
7. Sublist3r: This tool helps you find subdomains of a target domain. It can be useful for discovering additional entry points to a system that might have vulnerabilities.
8. Dirb: Dirb is a tool that helps you find hidden directories and files on web servers. It can uncover sensitive files or configurations that might be vulnerable to attacks.
9. GitTools: GitTools is a set of tools for finding security issues in Git repositories. It helps you identify exposed passwords, leaked source code, and other sensitive information that shouldn't be publicly accessible.
10. Shodan: Shodan is a search engine for connected devices. It can help you find systems with open ports or misconfigurations that could be exploited.
Remember to use these tools responsibly and follow the rules and guidelines of bug bounty programs. Always get proper authorization before conducting any security testing.
.png)
 10 months ago
59
10 months ago
59 











 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·