BOOK THIS SPACE FOR AD
ARTICLE ADHijacked accounts, hollow promises: Stream-jacked channels lure viewers with fake Bitcoin giveaways by utilizing deepfakes of popular celebrities, including Elon Musk, Ripple’s CEO Brad Garlinghouse, and Michael J. Saylor, former managing director of MicroStrategy, among many others.
Cybersecurity researchers at Bitdefender have published their latest research, highlighting a growing trend of YouTube stream-jacking campaigns using deepfake videos for cryptocurrency theft. The latest report continues the company’s research on YouTube-related malicious scams published in October 2023.
Despite companies like McAfee launching tools such as MockingBird, designed to detect 90% of deepfake content, scammers persist in employing malicious techniques to execute crypto scams. In some instances, they have managed to successfully bypass facial recognition systems, highlighting the ongoing challenges in combating these deceptive practices.
Stream-Jacking
For your information, YouTube stream-jacking is a cybercrime where criminals steal accounts from popular channels using livestream pop-ups, QR codes, and malicious links. Crypto-doubling scams lure viewers into depositing their cryptocurrency into platforms, promising quick returns. Victims are lured into depositing their funds, only to find their funds disappear without a trace.
As of the first week of January 2024, there were 2.70 billion active users on YouTube. These staggering stats make the video hosting platform a lucrative target for cybercriminals and scammers.
According to Bitdefender’s research, cybercriminals are enhancing their stream-jacking attacks by creating content that mimics legitimate cryptocurrency news or announcements.
Stream-jacking 2.0 scams target popular channels for account takeover or lure followers to mimic channels with rewards. During their research, the researchers discovered that the top three highjacked accounts to carry these scams have over 31 million subscribers, with Tesla, MicroStrategy, and SpaceX being the top brands used. Bitdefender estimates that cyber criminals have netted over $600K so far.
Fake YouTube Channels, Real Verification!
Bitdefender’s blog post suggests that scammers use multiple announcements and high-profile news headlines to make their scams appear credible. For instance, attackers used the “SpaceX Starship integrated flight test 2” official event to launch fake livestreams under “SpaceX Launch Starship Flight Test! Elon Musk gives update on Starship!” on compromised channels.
Deepfake content helps scammers spread fraudulent schemes on compromised channels, using cryptocurrency-related videos of famous personalities, popular conference talks, and recordings. They encourage viewers to scan a QR code and send a certain amount of crypto to be doubled. Some deep fakes are of decent quality, but the live chat section is disabled unless a selected member or subscriber has been a long-term subscriber.
There is also a rising trend of using Deepfakes in YouTube ads rather than livestreams, providing more opportunities for cybercriminals to spread scams. Account takeovers are usually enabled by compromising YouTube access tokens with stealers.
Malicious actors revamp the channel to impersonate the entity they want to impersonate, likely through automated processes. The revamping process involves changes to the channel name, handle, visibility, avatar, banner, description, links, featured channels, and anything that can help identify the original channel.
Bitdefender researchers have identified signs of artificial boosting of viewers in most livestreams. In December 2023, malicious actors began broadcasting scams targeting the Bitcoin ETF, focusing on MicroStrategy and Michael Saylor.
One such example is scammers broadcasting using looped deepfakes relying on MicroStrategy’s former CEO to participate in giveaways by scanning QR codes and following instructions. Compromised channels use variations of the official MicroStrategy logo, official banners, and playlists to boost credibility.
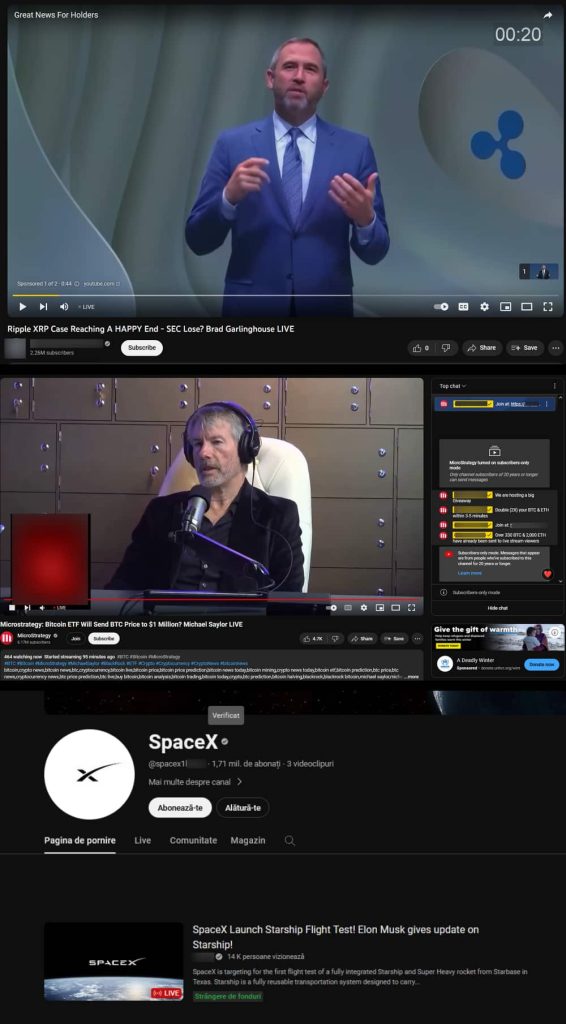 Deepfake YouTube ad featuring Ripple’s CEO Brad Garlinghouse – Deepfake powered livestream featuring Michael J. Saylor, former managing director of MicroStrategy giving away Bitcoin – Fake and verified SpaceX YouTube account with millions of subscribers.
Deepfake YouTube ad featuring Ripple’s CEO Brad Garlinghouse – Deepfake powered livestream featuring Michael J. Saylor, former managing director of MicroStrategy giving away Bitcoin – Fake and verified SpaceX YouTube account with millions of subscribers.The most common names after the takeover are MicroStrategy US, MicroStrategy, Microstrategy, Microstrategy US, Microstrategy Live, and Micro Strategy. Subsequently, deceptive websites began to surface, hosted on domains mimicking the company’s name or its former CEO, often incorporating symbols associated with cryptocurrencies and multipliers.
These fraudulent sites featured animated presentations showcasing multiple transactions, designed to create the illusion of live activity. It’s important to note that these animations were randomly generated and did not reflect actual transactions, serving as a misleading tactic to convey a false sense of legitimacy.
Protect Yourself from YouTube Crytp Scams!
Crypto scams on YouTube are a serious issue. In 2020, Apple co-founder Steve Wozniak sued YouTube over Bitcoin scams using his name. Wozniak accused YouTube and Google of enabling Bitcoin giveaway scams by failing to take action against them.
To avoid becoming a victim of stream-Jacking 2.0, be cautious of unexpected changes in content, double-check links, avoid investing based on online endorsements, and thoroughly research investment opportunities.
Additionally, Enable two-factor authentication (2FA) on YouTube accounts to prevent unauthorized access. Remember that if something seems too good to be true, it could be a scam. Don’t let a deepfake fool you into losing your crypto.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·