BOOK THIS SPACE FOR AD
ARTICLE ADA new report reveals how inexpensive cybercrime can compromise even the most secure organizations. According to Hudson Rock, employees at key US defence entities, including the Pentagon, major contractors like Lockheed Martin and Honeywell, military branches, and federal agencies like the FBI, have fallen victim to Infostealer malware.
These infections expose highly sensitive data, sometimes for as little as $10, without the need for advanced hacking techniques due to the most persistent security weakness: human error.
How Did It Get Here?
Infostealer doesn’t rely on flashy exploits or brute force. It plays the long game, waiting for unsuspecting users to click on a malicious link or download something they shouldn’t; perhaps a game mod, pirated software, or a booby-trapped PDF. Once triggered, the malware settles in, harvesting credentials, session cookies, and sensitive files without raising any suspicion.
The result? Cybercriminals can now buy this stolen data for as little as $10 per infected computer on dark web marketplaces. Need access to a military VPN? There’s a log for that. Curious about someone’s email inbox? Easy. Want to hijack a session and bypass two-factor authentication? Consider it done.
And the scope? According to Hudson Rock’s report, over 30 million computers worldwide have been hit, with one in five holding corporate credentials. For defence employees, the consequences couldn’t be more alarming. Many of these individuals work on mission-critical projects involving advanced technologies like fighter jets, nuclear submarines, and AI systems. Their compromised devices open the door to large-scale data breaches and cyber espionage, not just for their employers but for the national security of the country they are based.
Honeywell and the US Navy: Case Studies in Compromise
The report offers specific examples of the damage already done. At Honeywell, a major defence contractor, nearly 400 employees were infected. This breach exposed access to internal systems, development tools, and, critically, credentials for third-party partners like Microsoft and Cisco.
The U.S. Navy is also affected, with 30 personnel having their credentials stolen. Leaked data includes access to email systems, file-sharing platforms, and military training resources. These credentials could allow attackers to move laterally through military networks, accessing sensitive training platforms or even classified systems.
This creates an opportunity for attackers to launch supply chain attacks. The interconnected nature of global supply chains means a single weak link can lead to widespread damage as described by the ethical hacker duo last week when they discovered a vulnerability in a software supply chain firm that could have had far-reaching consequences if it fell into the wrong hands.
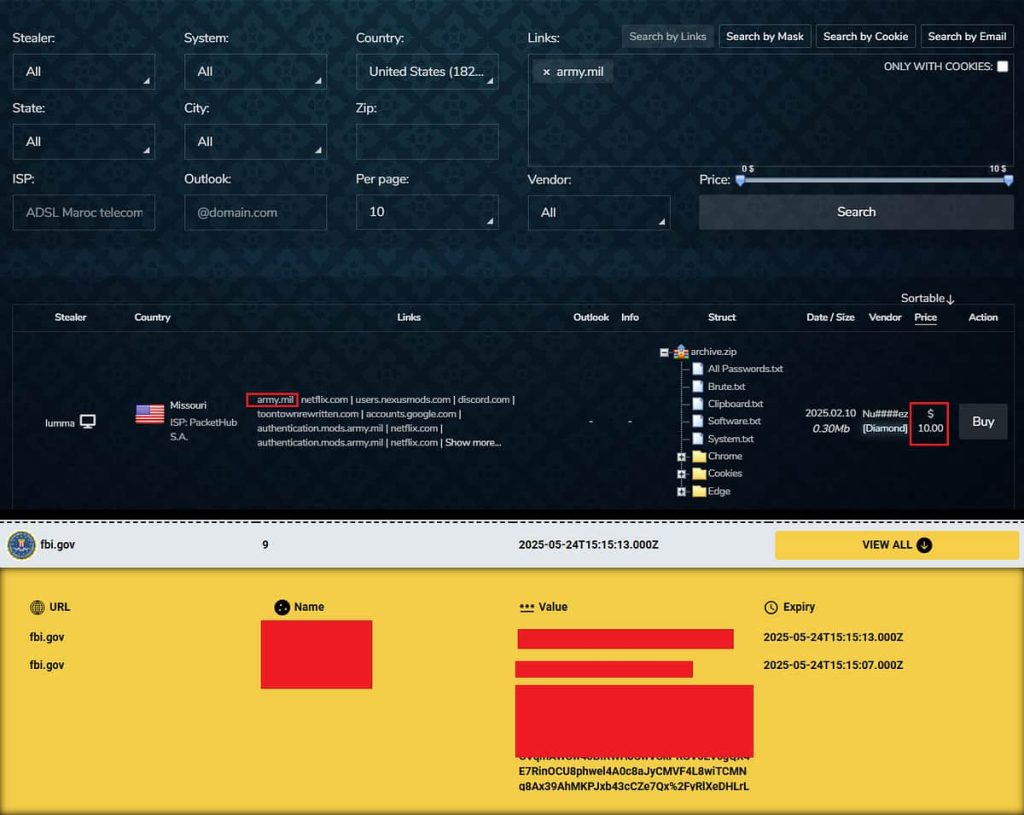 A screenshot reveals a computer with army.mil credentials being sold for just $10 on a cybercrime marketplace. Another shows live FBI.gov cookies from an infected device belonging to an FBI employee, exposing serious security risks. (Credit: Hudson Rock)
A screenshot reveals a computer with army.mil credentials being sold for just $10 on a cybercrime marketplace. Another shows live FBI.gov cookies from an infected device belonging to an FBI employee, exposing serious security risks. (Credit: Hudson Rock)
A Wake-Up Call for National Security
These findings are not just limited to the United States. The National Security of any country can be jeopardised if infostealers continue to breach critical infrastructure. With infostealers like Redline, Vidar and Formbook, Fortune 500 companies to small subcontractors, everyone is a potential target.
Thomas Richards, Director of Network and Red Team Practices at Black Duck, puts it bluntly: “The latest report from Hudson Rock is incredibly concerning. The stolen data could allow an adversary to infiltrate critical networks and compromise additional systems. Immediate action, including password resets and forensic investigations, is essential to mitigate these risks.”
So what’s next? Hudson Rock’s report proves that cybersecurity is not just about firewalls and advanced technology, it is also about the human element demanding a change in focus towards employee cybersecurity training.
The extremely low cost of these Infostealers makes it clear why law enforcement agencies worldwide are determined to shut down the dark web and clearnet cybercrime markets. Nevertheless, cybersecurity isn’t a checkbox; it is a mindset. And if there’s one thing this report makes clear, it is that the time to act is now.
.png)











 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·