BOOK THIS SPACE FOR AD
ARTICLE ADAnalyst finds ransomware evidence, despite a contractor’s denial of compromise.
A database filled with the medical records of nearly 200,000 U.S. military veterans was exposed online by a vendor working for the Veterans Administration, according to an analyst, who also presented evidence the data might have been exfiltrated by ransomware attackers.
The files were first discovered on April 18 by researcher Jeremiah Fowler, who found the database sitting exposed online without even basic password protection. Fowler said the files made several references to United Valor Solutions. United Valor is a North Carolina-based company which “provides disability evaluation services for the Veterans Administration and other federal and state agencies,” according to its site.
Analyst Found Ransomware Evidence, Contradicting Contractor

The database contained plenty of PII. Click to enlarge. Source: Jeremiah Fowler.
The exposed data included patient names, birth dates, medical information, contact information and even doctor information and appointment times, all of which could be used in socially engineered attacks, Fowler explained. The database also exposed unencrypted passwords and billing details.
“The database was set to open and visible in any browser (publicly accessible) and anyone could edit, download or even delete data without administrative credentials,” Fowler said about his findings.
He added to Threatpost, “This finding is sensitive based on the HIPAA implications and the fact that these are Veterans trying to obtain disability benefits. ”
After disclosing the findings to United Valor, Fowler said he received a reply the next day thanking him and adding, “We communicated your findings to our contractors, and they shut down this public data access immediately.”
It added, “According to their monitoring, the data has only been accessed via our internal IP and yours.”
However, the data told Fowler a different story.
Ransomware Demand Detected In Dataset
“The dataset also contained a ransomware message titled “read_me” that claimed all of the records were downloaded and they would be leaked unless 0.15 Bitcoin ($8,148) was paid,” Fowler explained. “The forensic audit or IP review of outside access conducted by the contractor should have also identified the ransomware intrusion and the multiple internet-of-things (IoT) search-engine spiders that indexed the exposed database. This appears to contradict what the contractors told United Valor.”
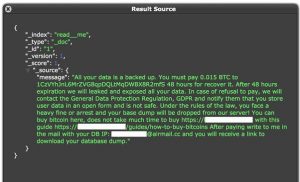
The ransom note. Click to enlarge. Source: Jeremiah Fowler.
Threatpost reached out to both United Valor and the Veterans Administration for additional details or comment but has not yet received a response.
Dirk Schrader with New Net Technologies thinks the breach was likely the result of one of three issues: “Either the contractors had, or still have, only limited monitoring capabilities; the cybercriminal who left the ransom note was able to hide traces, which indicates another, even bigger issue; or they (United Valor Solutions) are trying to avoid consequences.”
Healthcare: A Ransomware Target
Healthcare, even more than other sectors, needs to get protections in place against ransomware attacks, Untangle’s Heather Paunet explained to Threatpost.
Just days ago, Scripps Health, a San Diego-area hospital system was hit with a cyberattack, disrupting services. Last September, Universal Health Services, which operates a national network of hospitals, was hit by Ryuk with a ransomware attack. And an earlier attack on Dusseldorf University hospital in Germany forced the emergency room to divert patients to other facilities, causing patient care to suffer.
“The healthcare industry remains a high-level ransomware target,” Paunet said. “IT departments need to be more aware than ever before about how to protect their network, their employees and their patients.”
The strain that healthcare companies are under dealing with a global pandemic is what makes them even more attractive victims.
“The healthcare industry is in a very challenging situation these days, Mohit Tiwari, CEO at Symmetry Systems, told Threatpost. “They need to prioritize fighting a number of healthcare-related issues every day as well as having to work with software and hardware that takes years to certify for safety.”
She added that the key to fortifying protections of medical data is a robust compute infrastructure.
“Computing failures are, in fact, healthcare failures,” Tiwari explained. “Additionally, computing flaws are highly correlated and can spread rapidly.”
Join Threatpost for “Fortifying Your Business Against Ransomware, DDoS & Cryptojacking Attacks” – a LIVE roundtable event on Wed, May 12 at 2:00 PM EDT. Sponsored by Zoho ManageEngine, Threatpost host Becky Bracken moderates an expert panel discussing best defense strategies for these 2021 threats. Questions and LIVE audience participation encouraged. Join the lively discussion and Register HERE for free.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·