Misconfigurations in multiple Android apps leaked sensitive data of more than 100 million users, potentially making them a lucrative target for malicious actors.
"By not following best-practices when configuring and integrating third-party cloud-services into applications, millions of users' private data was exposed," Check Point researchers said in an analysis published today and shared with The Hacker News.
"In some cases, this type of misuse only affects the users, however, the developers were also left vulnerable. The misconfigurations put users' personal data and developer's internal resources, such as access to update mechanisms, storage, and more at risk."
The findings come from a study of 23 Android applications available in the official Google Play Store, some of which have downloads ranging from 10,000 to 10 million, such as Astro Guru, iFax, Logo Maker, Screen Recorder, and T'Leva.
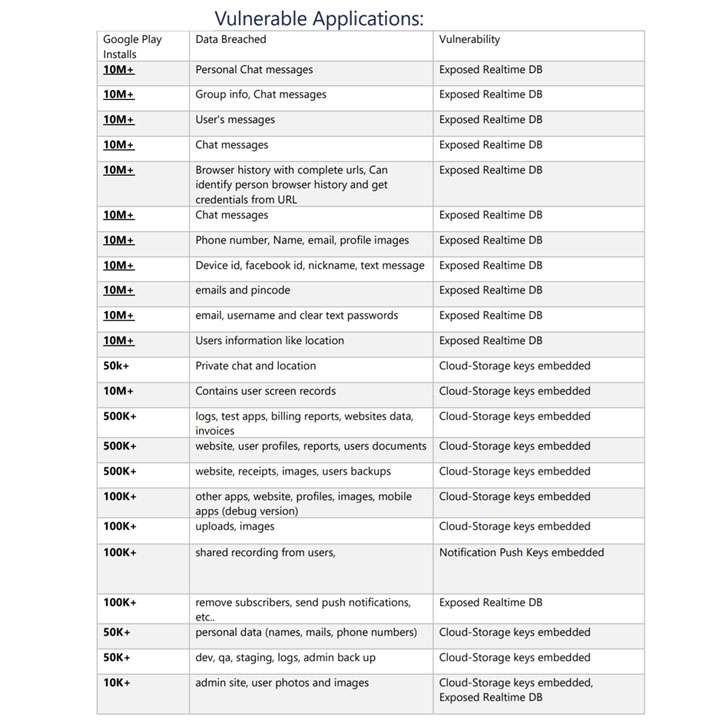
According to Check Point, the issues stem from misconfiguring real-time databases, push notification, and cloud storage keys, resulting in spillage of emails, phone numbers, chat messages, location, passwords, backups, browser histories, and photos.
By not securing the database behind authentication barriers, the researchers said they were able to obtain data belonging to users of Angolan taxi app T'Leva, including messages exchanged between drivers and passengers as well as riders' full names, phone numbers and destination and pick-up locations.
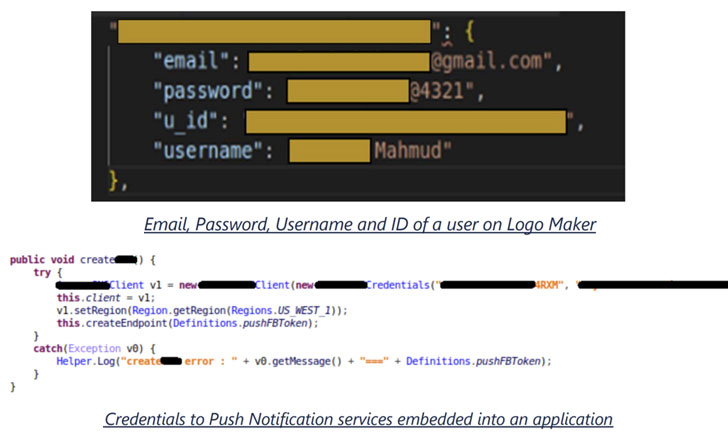
What's more, the researchers found that app developers embedded keys required for sending push notifications and accessing cloud storage services straight into the apps. This could not only make it easier for bad actors to send a rogue notification to all users on behalf of the developer, but could also be exploited even to direct unsuspecting users to a phishing page, thus becoming an entry point for more sophisticated threats.
Embedding cloud storage access keys into the apps, likewise, opens the door to other attacks wherein an adversary could get hold of all data stored in the cloud — a behavior that was observed in two apps, Screen Recorder and iFax, thereby giving the researchers the ability to access screen recordings and faxed documents.
Check Point notes that only a few of the apps changed their configuration in response to responsible disclosure, implying users of other apps continue to remain susceptible to possible threats like fraud and identity theft, not to mention leverage the stolen passwords to gain access to other accounts fraudulently.
"Ultimately, victims become vulnerable to many different attack vectors, such as impersonations, identify theft, phishing and service swipes," said Aviran Hazum, Check Point's manager of mobile research, adding the study "sheds light on a disturbing reality where application developers place not only their data, but their private users' data at risk."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
186
3 years ago
186 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·