BOOK THIS SPACE FOR AD
ARTICLE ADHi People, Yesterday I was hunting on one application and got 5 different ATO’S and even without user interaction in a single application and yeah I was also shocked as you are so I thought of writing a write-up. Also this is my first write up so please ignore any mistakes.
The website didn’t allow public disclosure so let’s take it as target.com and let’s head straight to the bugs.
ATO 1-Through JWT Misconfiguration
So the first thing I look for whenever I hunt for bugs is for ATO so I registered an account and the application was JWT tokens for authentication so I quickly copied my JWT and went to jwt.io for decoding the jwt and it looked like this-

After looking into this I was 50% sure that there might be any flaw and the next thing which I needed was to get any way through which I can get user id of other people.
So I thought that maybe it leaked in response when we requested a reset password but unfortunately it was not leaking the user id but it was leaking something more juicy and that will be discussed later.
Then I tried to login with wrong password and checked the response of the request and it was leaking the user id

Then I quickly registered a 2 account and got it’s user id and went to jwt.io and replaced it and got the JWT Token, then I logged in with my 1 account but I replaced the JWT and guess what I was logged into my 2 account.
Here is a quick JWT meme

ATO 2-Through OAUTH Misconfiguration
After this I quickly reported this and then I thought of testing for OAUTH bugs usually I only test for facebook OAUTH and I did the same for this target too but it’s FB OAUTH was not working and I never test google sign in because I never got any bug but I thought of giving it a try and I did intercept on and tried to sign in with google account and I saw this-

At this moment I was sure that boy you have got one more ATO and I quickly changed my email and forwarded the request and I was logged in into another account.
After 2 ATO’S I was like this and come’on who will be not happy, right?

I reported this one too and usually as soon as I get 1 or 2 bugs in a target then I usually stop hunting and watch any web series, currently I am watching “The Office” and I am in love with it but this time I thought of looking for some more bugs and let’s move to the 3 ATO.
ATO 3- No Rate Limit on OTP Verification
I went to the reset password function and the application was using 4 digit OTP code for verification and whenever you see a OTP then I know

Yes you are right I quickly fired burp and entered 1000 payloads to verify there was Rate limiting or not and there was no RL and OTP could be brute forced & with this I got my 3 ATO in a single application and reported that but the journey didn’t stopped here.
ATO 4-OTP Bypass Through Response Manipulation
There is one more way to bypass OTP and i.e by response manipulation.In Response Manipulation one just have to check the response and have to play with the response and I went to inruder and checked what was the response when one correct OTP was being supplied and it was-

There was no access token also the OTP was only being verified at first end and when we entered a new password at that stage OTP was not being verified so I tried for response manipulation by entering the wrong OTP and then changing the response to the response that I got on entering the correct OTP.

AT0 5-IDOR on Reset Password
The last one was also an Basic IDOR, When I requested for reset password then the request response looks like this
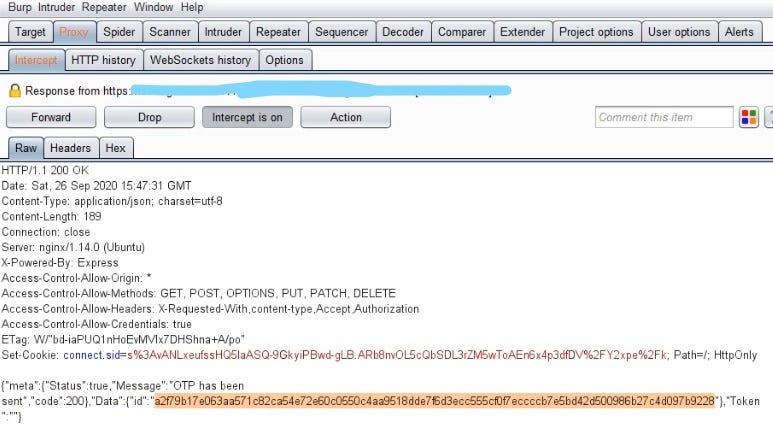
Then OTP came to my email and I entered the OTP but when I entered new password and captured that request
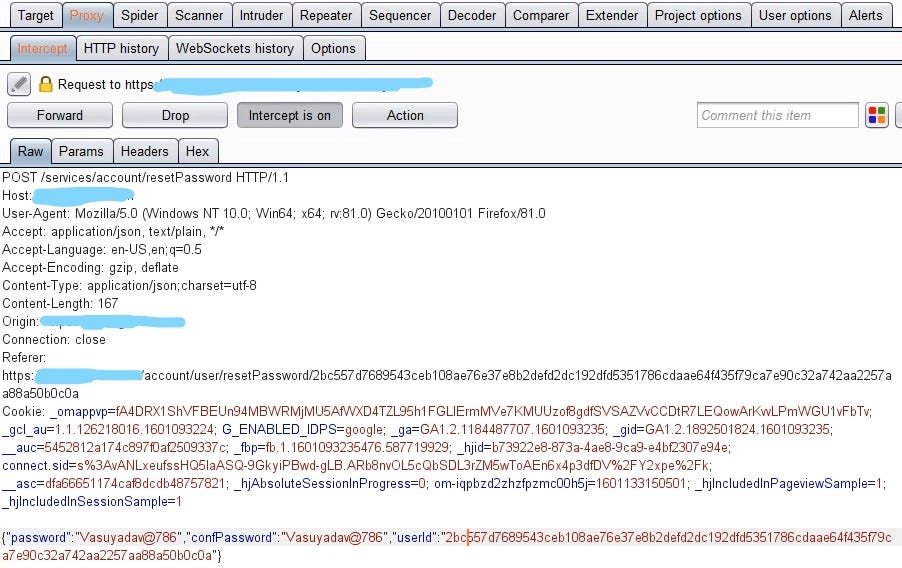
Then I saw there is no OTP field and also there is user id and it is encrypted but it was being leaked in the response so I just simply changed it with the user id of my another account and boom the password of my another account was changed.
In total I got 5 ATO’S and Note -These are the one’s which didn’t require user interaction, there were a lot more like csrf and all but in this I wanted to only focus on these ones only.
If you liked the write up then please share it with your friends and let’s connect on Twitter and Linkedin & if you are a complete beginner like I was a few months back then don’t hesitate to contact me on the below handles with your doubts and I will be more than happy to clear them.
Have a great day ahead and keep hunting and sharing your findings with the community.
Twitter-”https://twitter.com/VasuYadaav”
Linkedin-”https://www.linkedin.com/in/vasu-yadav-82ba701a0/”
Thanks to John-”https://twitter.com/johnjhacking” for the memes and for always helping me out do follow him if you don’t yet.
.png)
 4 years ago
200
4 years ago
200 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·