BOOK THIS SPACE FOR AD
ARTICLE AD
A 7-Zip vulnerability allowing attackers to bypass the Mark of the Web (MotW) Windows security feature was exploited by Russian hackers as a zero-day since September 2024.
According to Trend Micro researchers, the flaw was used in SmokeLoader malware campaigns targeting the Ukrainian government and private organizations in the country.
The Mark of the Web is a Windows security feature designed to warn users that the file they're about to execute comes from untrusted sources, requesting a confirmation step via an additional prompt. Bypassing MoTW allows malicious files to run on the victim's machine without a warning.
When downloading documents and executables from the web or received as an email attachment, Windows adds a special 'Zone.Id' alternate data stream called the Mark-of-the-Web (MoTW) to the file.
When attempting to open a downloaded file, Windows will check if a MoTW exists and, if so, display additional warnings to the user, asking if they are sure they wish to run the file. Similarly, when opening a document in Word or Excel with a MoTW flag, Microsoft Office will generate additional warnings and turn off macros.
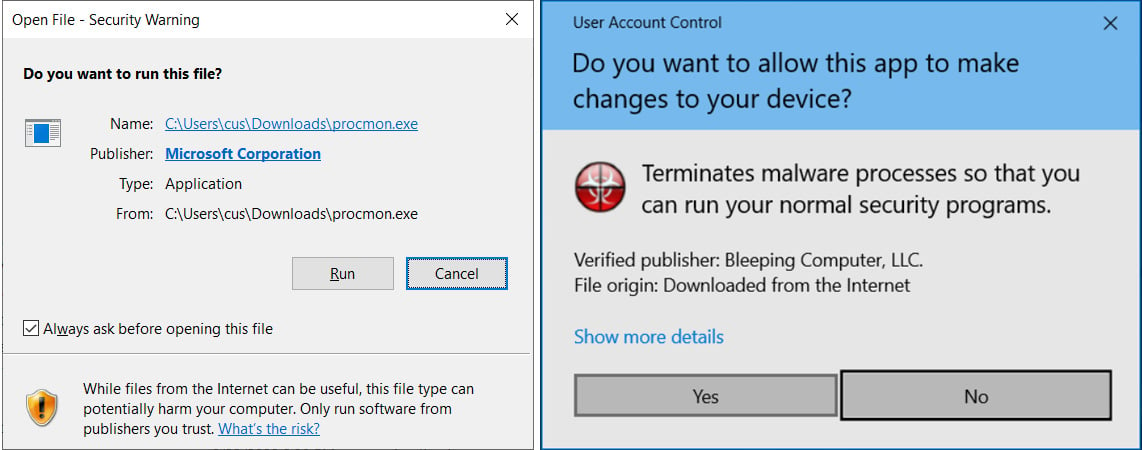 MoTW warnings in Windows
MoTW warnings in WindowsSource: BleepingComputer
As the Mark of the Web security features prevent dangerous files from automatically running, threat actors commonly attempt to find MoTW bypasses so their files automatically run and execute.
For years, cybersecurity researchers requested 7-Zip add support for the Mark of the Web, but it was only in 2022 that support for the feature was finally added.
MoTW bypasses exploited in attacks
Trend Micro's Zero Day Initiative (ZDI) team first discovered the flaw, now tracked as CVE-2025-0411, on September 25, 2024, observing it in attacks carried out by Russian threat actors.
Hackers leveraged CVE-2025-0411 using double archived files (an archive within an archive) to exploit a lack of inheritance of the MoTW flag, resulting in malicious file execution without triggering warnings.
The specially crafted archive files were sent to targets via phishing emails from compromised Ukrainian government accounts to bypass security filters and appear legitimate.
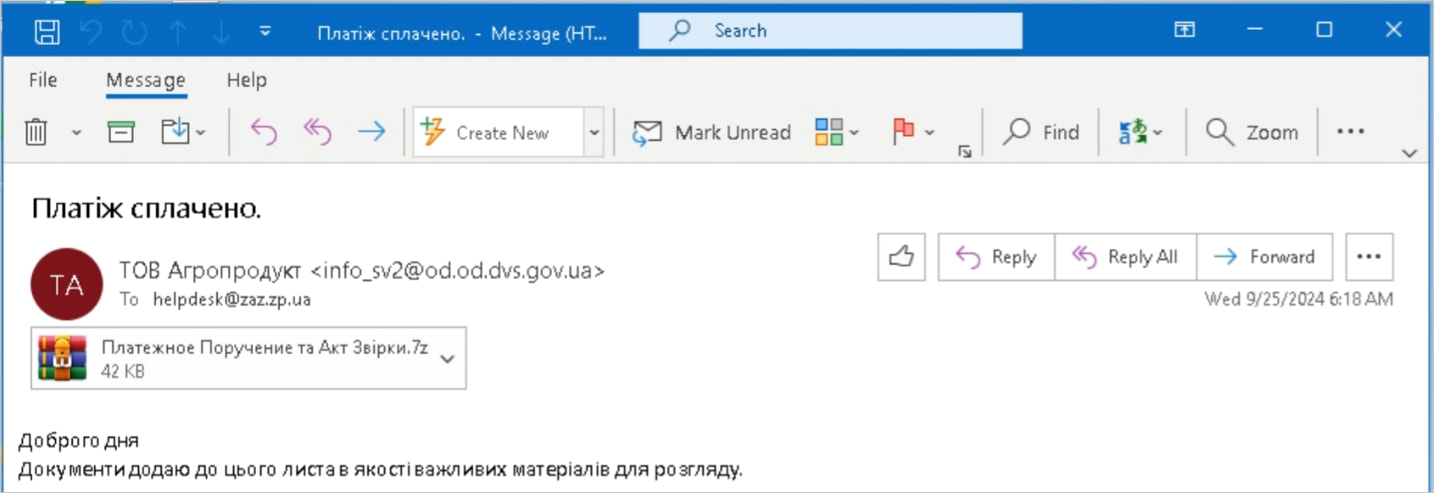 Sample phishing email used in the campaign
Sample phishing email used in the campaignSource: Trend Micro
Utilizing homoglyph techniques, the attackers hid their payloads within the 7-Zip files, making them appear harmless Word or PDF documents.
Although opening the parent archive does propagate the MoTW flag, the CVE-2025-0411 flaw caused the flag not to propagate to the contents of the inner archive, allowing malicious scripts and executables to launch directly.
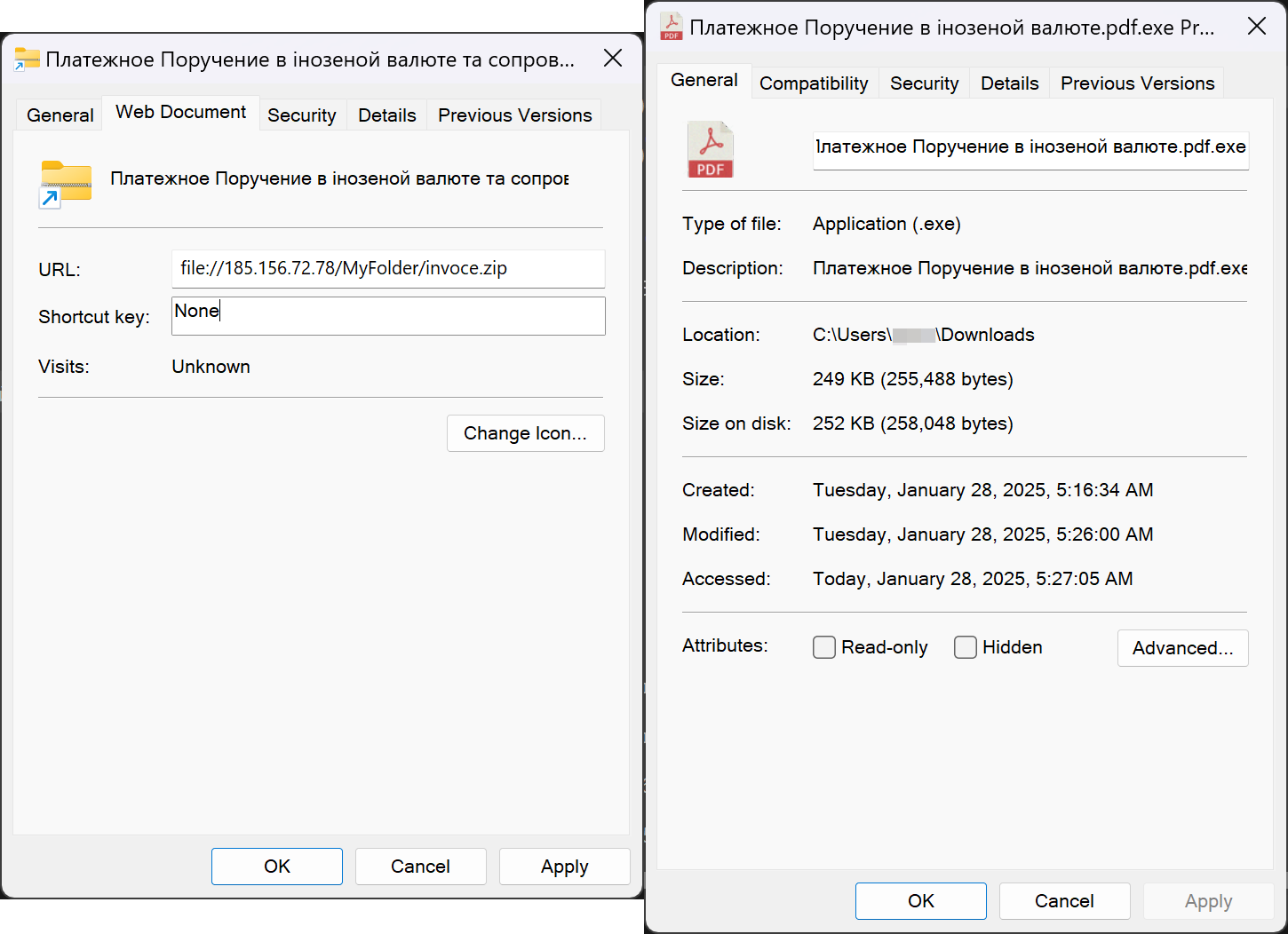 The real contents of the masked files
The real contents of the masked filesSource: Trend Micro
This last step triggers the SmokeLoader payload, a malware dropper used in the past to install info-stealers, trojans, ransomware, or creating backdoors for persistent access.
Trend Micro says these attacks impacted the following organizations:
State Executive Service of Ukraine (SES) – Ministry of Justice Zaporizhzhia Automobile Building Plant (PrJSC ZAZ) – Automobile, bus, and truck manufacturer Kyivpastrans – Kyiv Public Transportation Service SEA Company – Appliances, electrical equipment, and electronics manufacturer Verkhovyna District State Administration – Ivano-Frankivsk oblast administration VUSA – Insurance company Dnipro City Regional Pharmacy – Regional pharmacy Kyivvodokanal – Kyiv Water Supply Company Zalishchyky City Council – City councilUpdate 7-Zip
Although the discovery of the zero-day came in September, it took Trend Micro until October 1, 2024, to share a working proof-of-concept (PoC) exploit with the developers of 7-Zip.
The latter addressed the risks via a patch implemented in version 24.09, released on November 30, 2024. However, as 7-Zip does not include an auto-update feature, it is common for 7-Zip users to run outdated versions.
Therefore, it is strongly recommended that users download the latest version to make sure they are protected from this vulnerability.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·