BOOK THIS SPACE FOR AD
ARTICLE ADSome issues found in an undisclosed engagement (Let’s call it redacted.gov.lol)
Hello All,
I’m Youssef A. Mohamed aka GeneralEG
Information Security Analyst @Zinad & Bounty Hunter @HackerOne

As you may already know, I’m full-time bug bounty hunter and earlier this year I had signed a contract as an “Information Security Analyst” in one of the security services providers in our MENA region.
So, today I’m going to share with you a very exciting story about some findings I had found in my latest engagement with the mentioned company.
Note: These issues were found in an undisclosed engagement so let’s call it redacted.gov.lol
I started my working day as usual by opening my mail, to only find that I will be responsible of doing a “Black Box Web Application Pentest” for a critical foreign client.
After the kick off meetings and usual routine before every engagement. I had received the scope which was only one URL, thought I might find a registration function, reset password function or something else to make it easier to reach the application to perform my pen-testing.
In fact, it was only a login page with Captcha on the authenticating process and there’re no functions but login functionality.

Also, you won’t be able to brute force accounts due to the captcha which popups after clicking on “Log in” (tried to bypass it and failed) and also due to the lack of knowledge about how are the usernames looks like (is there’s a special pattern? numbers only, alphabets only…etc).
I tried to brute force the directories to check if there’s something else to test!
Fortunately, I found tomcat directories.

First thing to come to my mind is to try to login in “/html/manager/” but unfortunately it was protected with basic authentication.
Well, I grabbed the most-known wordlist for (users/passwords) for Tomcat and tried to brute force with Metasploit Module “tomcat_mgr_login” but with no luck also.

After further investigation, I found an “Improper Error Handling” disclosing the Tomcat’s Version and I tried to exploit some CVEs for this version but sadly no luck in that too.

So, my next approach was trying to login with a wrong credentials to investigate more how they are handling that too and from the cookies of that response I was able to figure out that they’re using F5 BigIP.
With no doubt I started to play with their BigIP with the newly disclosed Remote Code Execution (RCE).
But it wasn’t vulnerable. (Bad Luck huh, think again?)
After some researching about the F5 BigIP and its popular misconfigurations…
I tried some of those BigIP known misconfiguration but all what I found some Internal Information Disclosure (Pool name, Load balancing cookies, Backend IPs).

So, at this moment I was very disappointed. I turned my laptop off and went to play some VALORANT matches with my fellas.
Next day, I had my coffee and decided to take another look with fresh mind.
I repeated my reconnaissance steps again and started to brute force the directories all over again but with a bigger wordlist and this time I found 3 new HTML pages.
The first one was blank page.the second page was as infinite redirecting loop to itself, Ouch!The third one was a duplicated login page.I started to read the whole source code for all of these pages which impressively leaded me to a clue in the third page because it had more lines than the original login page.
Consequently, I started to carefully look into both code lines, surprisingly there were a few additional JS Files in the latter.
The HTML, JS files contained several endpoints, which needs authentication to access, and information such as (Request Method, Endpoint, Content-Type…etc).
So, I extracted them and build a full request from this information for every endpoint and saved them for later. (keep that in your mind)

My lucky star started to shine upon me, when I found a JS file with a valuable data more than the others…
It was containing a link to a HTML page, so I viewed the source code and I found one more request similar to the early discovered requests.
on this request’s data there’s a parameter called “User-Token” the value was sitting there!

At that moment, I was almost sure that I will own this application very soon.

I tried to add precious “User-Token” and its value to every request I saved earlier…

Then I executed them and Voilà! I’m in.

However, I couldn’t surf the whole application because there was no GUI, only API calls.
I grabbed our saved requests list to execute them with our token added to each request then I checked every response of them and grabbed more JS files and extract more [endpoints & parameters]
(repeated this operation for like +20 times)
Eventually… I found a weird request with a HTML response and it was designed to add an Icon on a kind of a menus bar (I don’t know what it is for…tbh)
So, I started to go with that flow.
Chose an Icon from a provided list, and then clicked on “continue” and chose a menu to be edited and then finished the whole flow and reached the final page with a button “Back to the main page”.
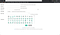
So, I clicked on it and it redirected me to the login page (forgot to add the user-token lol).
I repeated the move and added the token this time.
And Weeee!!
I reached a page contains a customized “Command Execution” function belongs to the Application. Good? I think so.
I tried all the commands that I know but it was blocked road so I figured out that it’s not a bug it’s a feature.
I tried the command “tree” (noticed the word earlier on a JS file).
And Voilà x2!

The application printed the whole endpoints on the application with its description.
So, I took a look at some of them but it wasn’t useful at all, so I decided to search more for juicy endpoints only.
After some diving, I collected some new endpoints with the description: “Admin Console”.
I tried to access to them with the token but faced the “Access Denied” sign…at that point I figured out that I’m not admin yet… so Looked back into the whole endpoints again.
I found an endpoint allows you to see an Information about your profile such as (Name, Role, Creation Date…etc) to only discover that I’m a user with low privileges.

So, I tried to navigate all the Admin’s Endpoints hopefully to find a Broken Access Control (BAC) or something juicy.
And Yaaay!! I found one endpoint out of the whole list allows me to enter without validating my sessions if belongs to an administrator or not.
And it was a special gift for me (Alhamdulillah) it was “Duplicating Users” Page.
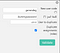
So, I Tried to discover all the page’s parameters and its values, and I found that I have the ability to duplicate an existing user on the database into a new user and it’s awesome!
We don’t know any usernames yet but for sure I tried admin at first and failed. then I tried Administrator and succeed and Duplicated the Administrator’s “roles” into a new username called GeneralEG.

So, I logged into the application with my new credentials and finally we have some UI to see.
I checked the “Admin Console” again and I was able to surf it and its secondary endpoints such as “Creating User”.
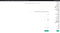
I navigated the latter endpoint and I had the ability to create a user from scratch with any role I want…but surprisingly I was able to choose the user’s application, so I expanded the list and I found that I can insert my “Evil Admin” into any one of +7000 Governmental Applications belongs to this country including (Presidential Election Board, Secret State Office, The Presidential Administration Board…etc) literally I was able to do whatever I want on this country…
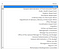
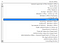
So, After I landed on what I demanded and much more.
I decided to stop testing at that point and not dive through these “Highly Confidential Areas”.
(I don’t like prisons that much LOL)

They told me later that this application is the head of a governmental E-Systems chain and its main role is to create users for the other applications.

For the record, the internal application had a lot of Penetration Testing Engagements before, so it was having a little amount of vulnerabilities but I could catch a nice “Remote Command Execution” due to some weaknesses I’ve escalated later such as (Executing SQL Command) directly to the backend and gain access into this “Holy Server” but I preferred to stay out of this confidential area!


I’m sure that my curiosity would put me in prison for a long time in this country lol!
Finally, I wrote my detailed report for this engagement and delivered it to the client and all parties were happy at the end. Also, I waited them to resolve all the discovered issues to publish this article publicly to the InfoSec community.
Takeaways:
Don’t get disappointed too early.Define your scope very carefully.Take notes by everything you found while testing even if it was useless.Try everything possible to gain access to your target, don’t miss a one!If you’re lost, take a rest.Do your Recon, Improve it and repeat!
.png)
 4 years ago
206
4 years ago
206 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·