A new advanced persistent threat (APT) has been behind a string of attacks against hotels across the world, along with governments, international organizations, engineering companies, and law firms.
Slovak cybersecurity firm ESET codenamed the cyber espionage group FamousSparrow, which it said has been active since at least August 2019, with victims located across Africa, Asia, Europe, the Middle East, and the Americas, spanning several countries such as Burkina Faso, Taiwan, France, Lithuania, the U.K., Israel, Saudi Arabia, Brazil, Canada, and Guatemala.
Attacks mounted by the group involve exploiting known vulnerabilities in server applications such as SharePoint and Oracle Opera, in addition to the ProxyLogon remote code execution vulnerability in Microsoft Exchange Server that came to light in March 2021, making it the latest threat actor to have had access to the exploit before details of the flaw became public.
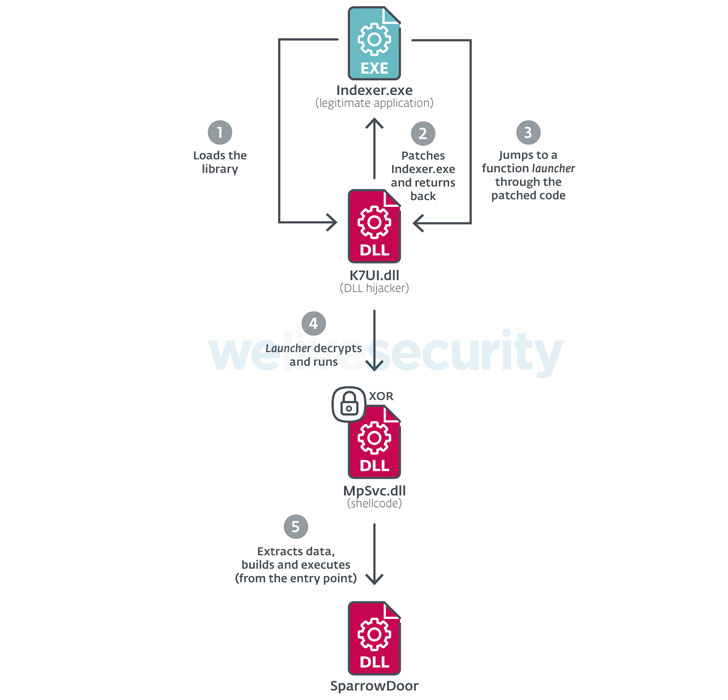
According to ESET, intrusion exploiting the flaws commenced on March 3, resulting in the deployment of several malicious artifacts, including two bespoke versions of Mimikatz credential stealer, a NetBIOS scanner named Nbtscan, and a loader for a custom implant dubbed SparrowDoor.
Installed by leveraging a technique called DLL search order hijacking, SparrowDoor functions as a utility to burrow into new corners of the target's internal network that hackers also gained access to execute arbitrary commands as well as amass and exfiltrate sensitive information to a remote command-and-control (C2) server under their control.
While ESET didn't attribute the FamousSparrow group to a specific country, it did find similarities between its techniques and those of SparklingGoblin, an offshoot of the China-linked Winnti Group, and DRBControl, which also overlaps with malware previously identified with Winnti and Emissary Panda campaigns.
"This is another reminder that it is critical to patch internet-facing applications quickly, or, if quick patching is not possible, to not expose them to the internet at all," ESET researchers Tahseen Bin Taj and Matthieu Faou said.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
239
3 years ago
239 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·