Siemens on Friday shipped firmed updates to address a severe vulnerability in SIMATIC S7-1200 and S7-1500 programmable logic controllers (PLCs) that could be exploited by a malicious actor to remotely gain access to protected areas of the memory and achieve unrestricted and undetected code execution, in what the researchers describe as an attacker's "holy grail."
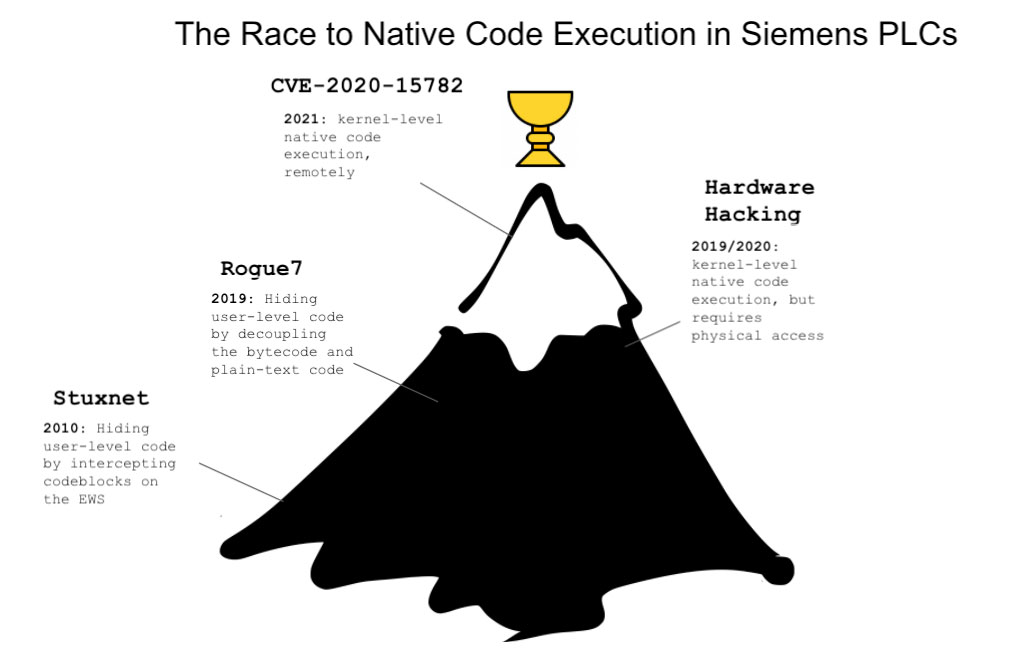
The memory protection bypass vulnerability, tracked as CVE-2020-15782 (CVSS score: 8.1), was discovered by operational technology security company Claroty by reverse-engineering the MC7 / MC7+ bytecode language used to execute PLC programs in the microprocessor. There's no evidence that the weakness was abused in the wild.
In an advisory issued by Siemens, the German industrial automation firm said an unauthenticated, remote attacker with network access to TCP port 102 could potentially write arbitrary data and code to protected memory areas or read sensitive data to launch further attacks.
"Achieving native code execution on an industrial control system such as a programmable logic controller is an end-goal relatively few advanced attackers have achieved," Claroty researcher Tal Keren said. "These complex systems have numerous in-memory protections that would have to be hurdled in order for an attacker to not only run code of their choice, but also remain undetected."
Not only does the new flaw allow an adversary to gain native code execution on Siemens S7 PLCs, but the sophisticated remote attack also avoids detection by the underlying operating system or any diagnostic software by escaping the user sandbox to write arbitrary data and code directly into protected memory regions.
Claroty, however, noted that the attack would require network access to the PLC as well as "PLC download rights." In jailbreaking the PLC's native sandbox, the company said it was able to inject a malicious kernel-level program into the operating system in such a way that it would grant remote code execution.
This is far from the first time unauthorized code execution has been achieved on Siemens PLCs. In 2010, the infamous Stuxnet worm leveraged multiple flaws in Windows to reprogram industrial control systems by modifying code on Siemens PLCs for cyber espionage and covert sabotage.
Then in 2019, researchers demonstrated a new class of attacks called "Rogue7" that exploited vulnerabilities in its proprietary S7 communication protocol to "create a rogue engineering station which can masquerade as the TIA to the PLC and inject any messages favourable to the attacker."
Siemens is "strongly" recommending users to update to the latest versions to reduce the risk. The company said it's also putting together further updates and is urging customers to apply countermeasures and workarounds for products where updates are not yet available.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
238
3 years ago
238 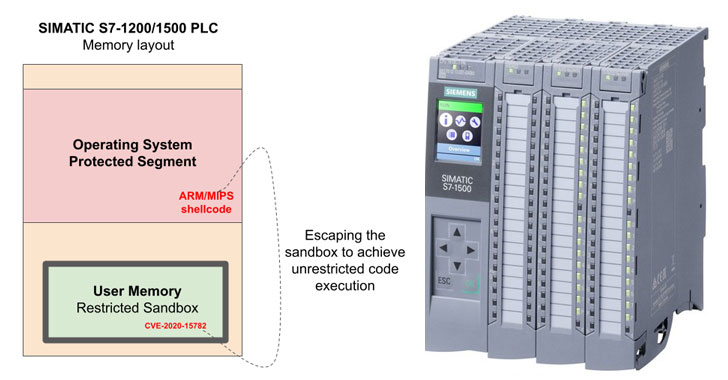
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·