BOOK THIS SPACE FOR AD
ARTICLE ADThreat hunters weigh in on how the business of ransomware, the complex relationships between cybercriminals, and how they work together and hawk their wares on the Dark Web.
Ransomware is not just a type of malware – it’s also at the center of a sophisticated, flourishing underground economy that has all the conventions of legitimate commerce.
It’s a community made up of major malware developers, affiliates and channel partners, and those that provide adjacent services, such as selling network access. Operators even have their own publicity arms that put out press releases and maintain their “brands,” and they have customer-service operations.
They found that the general economy of ransomware is well-developed and complex, with “several actors supplying services to one another,” according to research from Kaspersky. For instance, botmasters offer access to already-compromised devices; software developers improve the malware; and initial access brokers specialize in providing network access via backdoors or security vulnerability exploits for things like Remote Desktop Protocol (RDP).
This article is based on a much more in-depth piece, available in the free Threatpost Insider eBook, entitled “2021: The Evolution of Ransomware.” Download it today for much more on the ransomware underground economy!
“This access can be sold in an auction or as a fixed price, starting as low as $50,” Kaspersky researchers said, in a recent posting. “The attackers who create the initial compromise, more often than not, are either botnet owners who work on massive and wide-reaching campaigns and sell access to the victim machines in bulk, or hackers who are constantly on the lookout for publicly disclosed software vulnerabilities to exploit as soon as they are announced and before a patch is applied.”
RaaS Affiliates Are Carefully Vetted
At the center of the scene is the fact that ransomware operators often adopt affiliates, to whom they provide ransomware-as-a-service (RaaS) offerings. Affiliates can be seen as the channel partners of the underground, responsible for ransomware distribution to end victims. They usually pocket between 60 and 80 percent of the ransom, with the rest going into the operators and authors’ coffers.
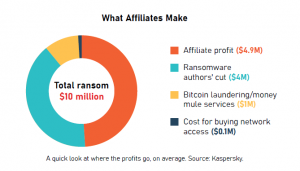
Click to enlarge.
“These gangs run like legitimate businesses: They have customer service and IT support, and will do what they can to boost their brand reputation,” according to experts at Intel 471, in a collaborative interview. “So, your most popular variants are those that result in higher payouts and take care of the criminal’s asks once they are brought into an affiliate program.”
RaaS operations carefully select their affiliate partners, with requirements that vary from technical expertise to the ability to prove they have roots in Russia or the former Soviet states.
“Well-established ransomware gangs are known to be rather picky,” according to Intel 471. “The basic requirement for a candidate willing to enroll into any high-profile RaaS affiliate program is typically to demonstrate availability of compromised accesses or potential sources of such accesses to lucrative corporate networks.”
In a 2020 posting in the Russian-language Exploit forum, MedusaLocker posted its requirements to prospective affiliates. These included “practical experience with ransomware, confident user of Cobalt Strike, able to escalate local administrator and domain administrator privileges, working knowledge of backup systems and understanding of OpSec.”
Meanwhile, in order to prevent infiltration of affiliate programs by western law-enforcement services and by cyber-threat researchers, some RaaS gangs implement additional precautions, which include vouching by existing members, a requirement for a native command of the Russian language, or vetting of local and cultural knowledge pertaining to Russia and ex-USSR countries, Intel researchers added.
Download “The Evolution of Ransomware” to gain valuable insights on emerging trends amidst rapidly growing attack volumes. Click above to hone your defense intelligence!
For example, a posting in the Exploit cybercrime forum by the REvil ransomware gang in fall 2020 noted, “No doubt, in the FBI and other special services, there are people who speak Russian perfectly, but their level is certainly not the one native speakers have. Check these people by asking them questions about the history of Ukraine, Belarus, Kazakhstan or Russia, which cannot be googled. Authentic proverbs, expressions, etc.”
This complicated vetting processes arises from the fact that criminals who make money illegally from online fraud operate within tight-knit circles by necessity, Dustin Warren, senior security researcher at SpyCloud, told Threatpost.
“It is not uncommon for criminals to be vouched into these trusted circles where they work with other criminals participating in various types of fraud,” he said. “Reputation is everything to these criminals, and they work for a very long time to establish this reputation so that they can get into these circles where money is being made.”
Competing for Market Share
In the cybercriminal underground, ransomware samples and builders are going for anywhere between $300 to $4,000, with ransomware-as-a-service rentals costing $120 to $1,900 per year. That’s according to a recent analysis by Kaspersky of the three main underground forums where ransomware is circulated.
In some cases, this has led to a bit of an arms race to develop the most innovative, advanced or stealthiest code for the market.
“Ransomware is often resold, and malware vendors definitely compete for market share,” Warren said. “There are always innovations in the works, especially around evading antivirus protections and other controls that might be in the way, to being able to encrypt files the fastest. They bank on their targets having complicated policies around how they patch their systems and how often.”
Download “The Evolution of Ransomware” to gain valuable insights on emerging trends amidst rapidly growing attack volumes. Click above to hone your defense intelligence!
Some strains and services are unequivocally more popular than others, simply because they work better than others, he added. Yet, the option that a threat actor ultimately decides to purchase and use often depends on other factors as well, such as the reputation of the author of the malware or operator of the RaaS operation, price, geolocation, how easy the seller is to work with or the target victim’s attack landscape.
Backlash against operators can sometimes happen. For instance, it was recently revealed that cybercriminals who have worked as affiliates with ransomware group DarkSide, responsible for the Colonial Pipeline attack, are having a tough time getting paid for their work now that the group has had its operations interrupted; so, they’re turning to admins of the group’s Dark Web criminal forum to sort things out in what researchers call a “shady version of the People’s Court.”
Also, when a criminal software developer builds a new strand of ransomware, the person will often first share the project for free with a select few other trusted community members.
“This free copy of the malware is called a ‘vouched’ copy, and its purpose is to enable reputable actors to provide feedback and validate the new piece of malware,” Warren said. “Then, after the malware has been effectively peer reviewed and tweaked accordingly, the developer will advertise it publicly, on a forum for example.”
Individuals purchase ransomware software based off of price as well as their own use cases, according to Warren: “As such, good ransomware strains ultimately get a following; actors will often keep up with and purchase new versions of the same ransomware project as they are released (AZOrult is a good example of this).”
Business is booming on the cyber-underground. But that could change; a coalition of 60 global entities (including the U.S. Department of Justice) has proposed a sweeping plan to create a ransomware task force, to hunt down and disrupt ransomware gangs by going after their financial operations.
And, in the wake of the Colonial Pipeline hack, underground forums themselves are looking to take some of the heat off by removing RaaS ads and the like.
Philip Reiner, the CEO of IST and the executive director of the Ransomware Task Force, warned that something has to give.
“The cost of ransom paid by organizations has nearly doubled in the past year, and is creating new risks, many that go far beyond monetary damage,” he said. “In the past 12 months alone, we’ve seen ransomware attacks delay lifesaving medical treatment, destabilize critical infrastructure and threaten our national security.”
Download our exclusive FREE Threatpost Insider eBook, “2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·