BOOK THIS SPACE FOR AD
ARTICLE ADHello There, My Name is Aryan From Kurdistan, Bug Hunter in Hackerone with Experience 6 Months Also I Student in university, Forgive me for My English That I Used 😂That’s Bad🥲
As You Know That With Xss You Can Run Malicious Code Js , So I don’t further information about xss you could google search about Xss.
So Let’s Start:
First of all i found this bug in the company that give the internet service so i decide to test the website, Let’s called the company to redacted.com, The Company use the php and haven’t big scope thus used my methodology for small scope by this reason first thing that did Using The Nmap for Scan the Ports and i get some information :

As You can see the port 22 are open and the version of the OpenSSH are exploitable to
This Exploit used to Enumeration the user of SSH and immediately Report to company.

I Told Myself , I can find more bug so decide that further recon in my account in website , I used my tool to Gather Urls from Wayback Machine and I got some endpoints:

Have some Endpoints but I Focus on passwd.php and User.php and read many Js files to understand how the website work, You Know That the user.php for login with Credentials so I test for xss blind and stored but I Got NOTHING 😪 Also I Test for Bypass Login with some Payloads and Test for Sql Injection But Nothing Found😓😓 Then My Feelings Towards to Hopeless..
Last Endpoint That I Test is Passwd.php This Page to Recovery Password it means that the request is Post :
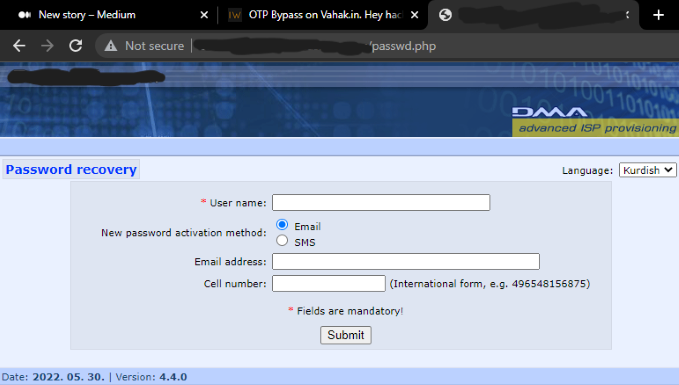
As You Can See The Form To Recovery Password First Thing That did test for XSS:
Now I Got The Rxss Post But How can I Increase Impact?
You Know That In Some Cases XSS Used To Steal Cookies and Sessions, The Rxss Post You can’t Gain Cookies and information about users because if send the link to users Popup Don’t Demonstrate Of webpage ,So I Think How Can I Do It, Thanks For MoSec(Moen) To Advice me and I use The Instruction , Use The CSRF To Redirect The Users To Webpage That Popup Occur And The Report OF Information Users That Click The Submit Button Shows In Xsshunter :
You Have The Cookies of users in xss hunter and At The Time Fire The Burp Suite, You Must Capture The Request of Login and Then Paste the Cookies of Users instead of Your Cookies:
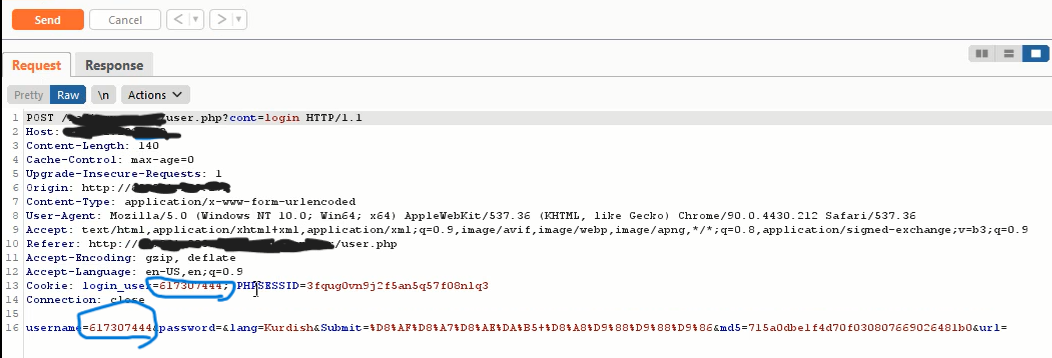





.png)
 1 year ago
104
1 year ago
104 












 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·