BOOK THIS SPACE FOR AD
ARTICLE AD
Advance Auto Parts has confirmed it suffered a data breach after a threat actor attempted to sell stolen data on a hacking forum earlier this month.
Advance operates 4,777 stores and 320 Worldpac branches and serves 1,152 independently owned Carquest stores in the United States, Canada, Puerto Rico, the U.S. Virgin Islands, Mexico, and various Caribbean islands.
Earlier this month, BleepingComputer reported that a threat actor named 'Sp1d3r' began selling data they claimed was stolen during the recent Snowflake data-theft attacks.
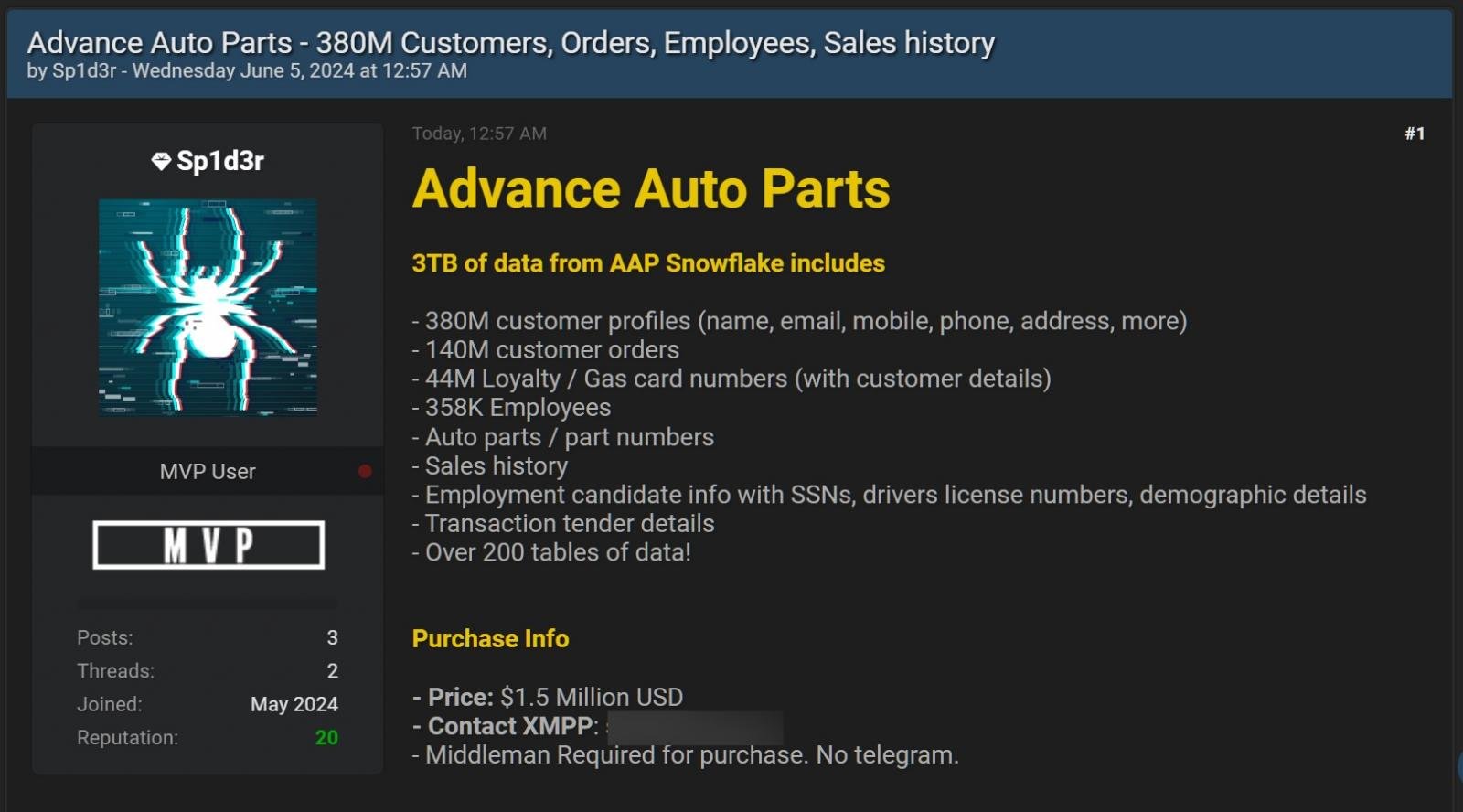 Advance Auto Parts data for sale on a hacking forum
Advance Auto Parts data for sale on a hacking forumSource: BleepingComputer
BleepingComputer contacted Advance multiple times about the alleged data breach, but they never responded to our emails.
However, in an SEC filing first spotted by security researcher pancak3, Advance Auto Parts confirmed that their data was stolen from a third-party cloud database environment.
"On May 23, 2024, Advance Auto Parts, Inc. (the "Company") identified unauthorized activity within a third-party cloud database environment containing Company data and launched an investigation with industry-leading experts," reads Form 8-K filing released on Friday.
"On June 4, 2024, a criminal threat actor offered what it alleged to be Company data for sale. The Company has notified law enforcement."
After investigating the stolen files, Advance says they believe they contain personal information for current and former employees and job applicants, including social security numbers and other government identification numbers.
Sample data leaked by the threat actor and seen by BleepingComputer also included employees' full names and email addresses. The data also included what is believed to be customer information, including email addresses and names.
Advance says they will send data breach notifications to those impacted and offer free credit monitoring and identity restoration services as necessary. It is unclear if this will be only for employees at this time or for exposed customers as well.
The company states that they have incurred $3 million in expenses due to the incident.
.png)















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·