"Dozens" of organizations across the world have been targeted as part of a broad business email compromise (BEC) campaign that involved the use of adversary-in-the-middle (AitM) techniques to carry out the attacks.
"Following a successful phishing attempt, the threat actor gained initial access to one of the victim employee's account and executed an 'adversary-in-the-middle' attack to bypass Office365 authentication and gain persistence access to that account," Sygnia researchers said in a report shared with The Hacker News.
"Once gaining persistence, the threat actor exfiltrated data from the compromised account and used his access to spread the phishing attacks against other victim's employees along with several external targeted organizations."
The findings come less than a week after Microsoft detailed a similar combination of an AitM phishing and a BEC attack aimed at banking and financial services organizations.
BEC scams typically entail tricking a target over email into sending money or divulging confidential company information. Besides personalizing the emails to the intended victim, the attacker can also impersonate a trusted figure to achieve their goals.
This, in turn, can be achieved by seizing control of the account through an elaborate social engineering scheme, following which the scammer emails the company's clients or suppliers fake invoices that request payment to a fraudulent bank account.
In the attack chain documented by Sygnia, the attacker was observed sending a phishing email containing a link to a purported "shared document" that ultimately redirected the victim to an AitM phishing page designed to harvest the entered credentials and one-time passwords.
UPCOMING WEBINAR
🔐 Mastering API Security: Understanding Your True Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and take proactive steps towards ironclad security. Join our insightful webinar!
What's more, the threat actors are said to have abused the temporary access to the compromised account to register a new multi-factor authentication (MFA) device in order to gain a persistent remote foothold from a different IP address located in Australia.
"In addition to exfiltration of sensitive data from the victim's account, the threat actor used this access to send new phishing emails containing the new malicious link to dozens of the client's employees as well as additional targeted organizations," Sygnia researchers said.
The Israeli cybersecurity company further said the phishing mails spread in a "worm-like fashion" from one targeted firm to the other and among employees within the same company. The exact scale of the campaign is currently unknown.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.
.png)
 1 year ago
130
1 year ago
130 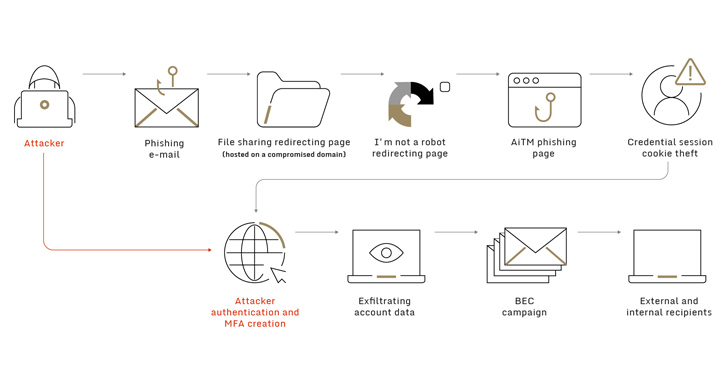
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·