Adobe has released Patch Tuesday updates for the month of May with fixes for multiple vulnerabilities spanning 12 different products, including a zero-day flaw affecting Adobe Reader that's actively exploited in the wild.
The list of updated applications includes Adobe Experience Manager, Adobe InDesign, Adobe Illustrator, Adobe InCopy, Adobe Genuine Service, Adobe Acrobat and Reader, Magento, Adobe Creative Cloud Desktop Application, Adobe Media Encoder, Adobe After Effects, Adobe Medium, and Adobe Animate.
In a security bulletin, the company acknowledged it received reports that the flaw "has been exploited in the wild in limited attacks targeting Adobe Reader users on Windows." Tracked as CVE-2021-28550, the zero-day flaw concerns an arbitrary code execution flaw that could allow adversaries to execute virtually any command on target systems.
While the targeted attacks took aim at Windows users of Adobe Reader, the issue affects both Windows and macOS versions of Acrobat DC, Acrobat Reader DC, Acrobat 2020, Acrobat Reader 2020, Acrobat 2017, and Acrobat Reader 2017. An anonymous researcher has been credited with reporting the vulnerability.
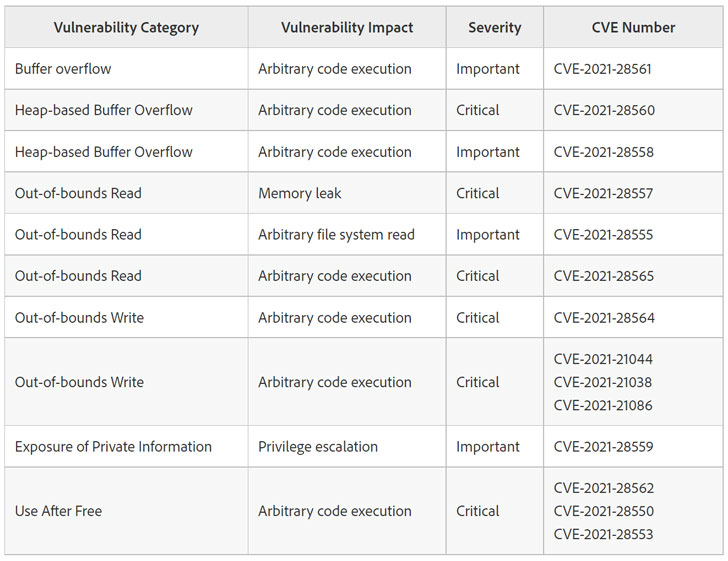
10 critical and four important vulnerabilities were addressed in Adobe Acrobat and Reader, followed by remediation for five critical flaws (CVE-2021-21101-CVE-2021-21105) in Adobe Illustrator that could lead to arbitrary code execution in the context of the current user. Adobe credited Kushal Arvind Shah of Fortinet's FortiGuard Labs with reporting three of the five vulnerabilities.
In all, a total of 43 security weaknesses have been resolved in Tuesday's update. Users are advised to update their software installations to the latest versions to mitigate the risk associated with the flaws.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
241
3 years ago
241 
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·