BOOK THIS SPACE FOR AD
ARTICLE ADOn June 8, Amazon’s pulling all its devices into a device-to-device wireless mix, inspiring FUD along the way. Now’s the time to opt out if you’re be-FUDdled.
On June 8, Amazon, the Web giant with tentacles reaching into every nook and cranny of our lives, is going to stretch those tentacles out further by turning all its gadgets into little cell towers so they can help each other out with little slices of bandwidth. It’s created a new Wi-Fi protocol with no beta testing to get your gadgets to talk to one another: a recipe for potential security and privacy problems, some experts say.
The initiative is called Amazon Sidewalk. Amazon initially announced Sidewalk in September 2019, describing it as a “new, long-term effort to greatly extend the working range of low-bandwidth, low-power, smart lights, sensors, and other low-cost devices customers install at the edge of their home network.” While Sidewalk has been in the works for a few years, the news of the June 8 deadline for turning it on seems to have caught many by surprise: It gives consumers just a week to learn about the initiative and to opt out if they so choose.
As Amazon describes it, Sidewalk will do things like keep motion alerts from security cameras coming even when the Wi-Fi goes down; will stretch Wi-Fi out to smart lights at the edge of your driveway; and could act like Tile tags to help customers find pets and valuables. In fact, in May, Amazon announced that Tile is going to be joining Sidewalk, along with CareBand, maker of wearable technology for people living with dementia.
What Could Possibly Go Wrong?
A few things, security experts told Threatpost on Monday. It probably should surprise no-one that the impending mesh network turn-on date in seven days has triggered fear, uncertainty and doubt, for a few reasons. First, the initiative involves a brand-new, untested Wi-Fi protocol that’s going live without having been beta tested. Also, it’s being turned on by default, making it opt-out only.
Of course, customers will first have to know about the initiative before they can opt-out. Given that some security experts said that even they were taken by surprise over the weekend by the news of the June 8 go-live date, consumers who don’t work in the security industry will surely be even more oblivious. “They dropped this on us,” said Jon Callas, director of technology projects for the Electronic Frontier Foundation (EFF), in a conversation with Threatpost on Monday. “They gave us seven days to opt out. I hadn’t even seen the privacy and security [white paper published by Amazon] before you sent it to me. They could have stage-managed this better.”
As well, customers will have to take it upon themselves to untangle their gadgets if they so choose, as opposed to knowingly opting in.
Second, security experts, while they do like what they see regarding security and privacy as detailed in the white paper, want to see more details. They anticipate problems, if simply because there are always flaws in new protocols.
Brand-New, Untested Protocol
Amazon is going to be running Sidewalk with its own, new Wi-Fi protocol, which uses the 900 MHz spectrum. The company projects that this will increase devices’ connection range by more than a half mile/one kilometer. If it all works out as planned, Amazon customers will be able to sprinkle Amazon gadgets around their properties like so many lawn ornaments, even in Wi-Fi and Bluetooth dead spots.
But the fact that this is a new, untested protocol is concerning. As pointed out by Ars Technica’s Dan Goodin, history is already littered with wireless technologies that have poor track records when it comes to encryption: First there was the easily cracked Wired Equivalent Privacy (WEP), then came Wi-Fi Protected Access (WPA): both of which were plagued with flaws that allowed easy decryption by eavesdroppers but which were nonetheless pervasive in older Wi-Fi networks. Those insecure Wi-Fi protocols make man-in-the-middle (MiTM) and malware-injection attacks all the more effective.
As Goodin put it, “If industry-standard wireless technologies have such a poor track record, why are we to believe a proprietary wireless scheme will have one that’s any better?”
No Stalking Mitigations
Finally, the white paper contains no details on mitigating stalking: an issue with devices such as Tile tags that can be slipped into purses or taped to the underside of cars in order to enable tracking.
“Stalking:That’s real, and a very bad thing,” Callas said. “If you think about it, if you have something like a Tile or [Apple AirTag] you can use to track anything with, to find out where you lost your keys, you can also drop one in somebody else’s handbag and track them. You can tape one to the bottom of a car. These can be used to stalk people.”
EFF Cybersecurity Director Eva Galperin has detailed the stalking risks of these devices, pointing out that AirTags in particular are a “gift to stalkers”: not only are they tiny and easy to slip into a surveillance target’s purse or onto their car, but Apple’s devices are ubiquitous. “You may go all day without coming within Bluetooth range (approximately 30 feet) of a Tile user, but try getting through the day without coming within 30 feet of an iPhone or iPad,” she wrote in a Wired opinion piece. “Tile measures its users in the tens of thousands. Apple has more than a billion.”
Apple unveiled its AirTag device-tracking tiles in April and then began allowing its Find My app to locate lost items made by third-party companies. About the size of a quarter, AirTags are Bluetooth trackers. Within weeks of their unveiling, a researcher demonstrated that Find My can be exploited to transfer data to and from random passing devices without using the internet. The exploit entails using a microcontroller and a custom MacOS app that can broadcast data from one device to another via Bluetooth Low Energy (BLE). Once connected to the internet, the receiving device can then forward the data to an attacker-controlled Apple iCloud server.
That’s one example of a Bluetooth tracker that can be abused. What might happen when Amazon unleashes Sidewalk, running on signals from its ubiquitous devices?
What Amazon Is Doing Right
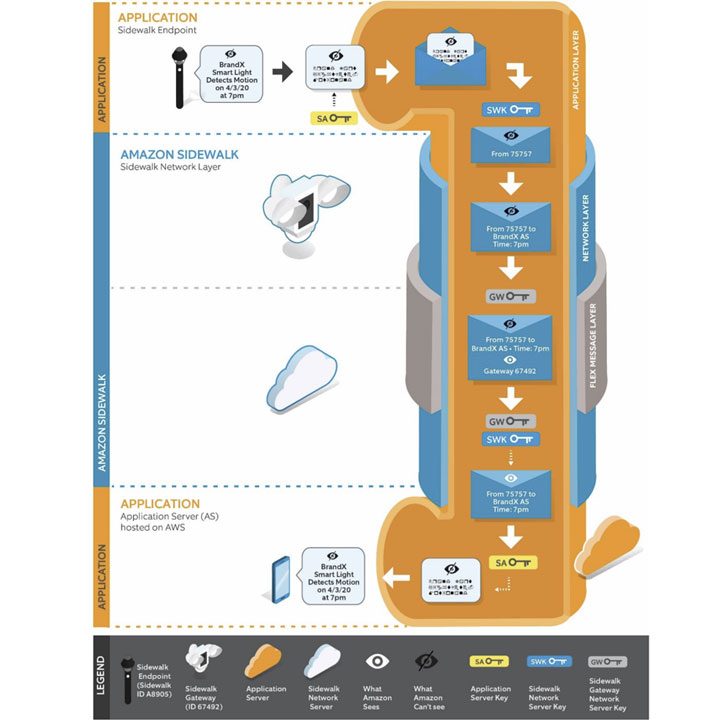
As far as security and privacy go, Amazon’s white paper describes how Sidewalk will secure network packets with these three layers of encryption:
The Sidewalk Application Layer enables secure and private communication between the endpoint and the Application Server. The Sidewalk Network Layer protects the endpoint’s Sidewalk packet over the air. Plain-text data in this layer is accessible only to the endpoint and the Sidewalk Network Server (SNS). The Flex Layer, which is added by the Sidewalk Gateway (GW), provides the SNS with a trusted reference of message-received time and adds an additional layer of packet confidentiality. Plaintext data in this layer is accessible only to the GW and the SNS.“This approach to encryption means that Amazon will not be able to interpret the contents of commands or messages sent through Sidewalk by third party services or endpoints (applications),” according to Amazon’s white paper.
Alex Hudson, a fractional CIO/CTO at Freeman Clarke, approved of Amazon’s security choices.
“I did read their security paper, and the various choices looked very sensible and standard (private certificate authority, use of well-known algorithms like NIST-P256 and ED25519), although it obviously puts a lot of power in the hands of Amazon,” he told Threatpost on Monday via email. “There’s a lot of one-time authentication in there, which is a sign the basic crypto design is probably sound (i.e. it would take someone a lot better than me to see the holes in it).”
Hudson highlighted what he called a “very interesting point” in the white paper, about how Amazon allows devices onto networks. Each device will assign itself a random transmission ID (TX-ID), but initially, those devices can’t communicate at all with the ID. “Amazon has a central database of *all* devices, and once the device tries to communicate with the TX-ID all of its traffic is dropped at the local gateway until the central database clears it. This clearance lasts as long as the random TX-ID does (they roll over every 15 minutes),” he explained. “This feels [like] a real novelty to me. It makes sense – if an [Amazon Fire tablet] or Alexa or whatever gets stolen, you can blacklist it centrally and it can never use Sidewalk again. But they will be able to block-list any device they don’t like the look of – I’m guessing that if anyone attempts to pull Sidewalk certificates out of valid devices to impersonate them, that will be an immediate block-list add. Sidewalk isn’t Amazon’s network – they’re not paying for the local data, etc. – but it’s their rules, and they’ll be able to kick anyone off they like.”
Likewise, the EFF’s Callas approved of Amazon’s choices, with a caveat. “A lot of what I see in that cryptography is, ‘I like what you did, tell me more,'” he said. “Every new one of these [Wi-Fi protocols] that comes out, we end up finding a few bugs.”
What More There Is to Know
Callas wants to see detailed protocol documents. While the level of encryption looks “pretty good,” he has followup questions about “whether there’s linkability in some things they’re doing,” he said. “One thing is that they have an identifier they’re rolling every 15 minutes: at, say, 7 a.m., 7:15. If I know how to go forward from the 7:15 one, then I might be able to link 7:00 to 7:15 if it was some fixed algorithm. If they’re genuinely going to make a random algorithm every 15 minutes, they might not be linkable.”
Multiple layers of encryption and rotating identifiers are sound security approaches, Callas said – ones that have been successfully employed in other Wi-Fi scenarios. Apple’s Find My network uses rotating identifiers, Callas pointed out, while exposure notifications for a COVID tracking system developed by Apple and Google uses similar, multiple layers of encryption and shifting encryption algorithms.
He just wishes that Amazon had communicated better. “The first look looks pretty good, but we want to see details,” he said.
Should We Worry?
Dmitry Kurbatov, CTO at Positive Technologies, said that problems are inevitable, but they aren’t serious enough to stop innovation. “Every time you introduce complexity or new function into the IoT ecosystem, this also creates the possibility for vulnerabilities, threats, exploitations and attacks,” he told Threatpost via email on Monday. “But it shouldn’t stop development. There are multiple ways to mitigate this additional risk, and I believe Amazon has implemented all the right steps. This is not the first usage of a mesh network, look at Apple AirTag – in principle, it uses the same approach and all is fine so far.”
He noted that once 5G is widely available across the US, there will be less need for a wireless mesh service like Sidewalk.
In the meantime, Sidewalk won’t be running with enough juice to cause much damage, Callas said. “80 kilobytes? That’s not enough to do much of anything. It’s not really an internet-sharing system,” he said. “Itt’s a device mesh communication system.”
How to Opt Out
Amazon has published this list of devices that will be pulled into Sidewalk on June 8: Ring Floodlight Cam (2019), Ring Spotlight Cam Wired (2019), Ring Spotlight Cam Mount (2019), Echo (third gen and newer), Echo Dot (third gen and newer), Echo Dot for Kids (third gen and newer), Echo Dot with Clock (third gen and newer), Echo Plus (all generations), Echo Show (all models and generations), Echo Spot, Echo Studio, Echo Input, and Echo Flex.
To opt out, owners of Echo and Ring devices can follow these steps on Alexa or Ring apps:
Alexa app: Open More > select Settings > Account Settings > Amazon Sidewalk, and toggle it on/off Ring app: Tap “three-lined” menu > Control Center > Sidewalk, and tap the slider buttonMake sure that opt-in out sticks: The Verge heard from a reader who said she opted out via the Alexa app. The reader found that when the feature came to the Ring app, she’d been opted back in again. Whether you have both apps or even if you don’t, it’s a good idea to double-check to make sure your opt-out is truly registered.
Threatpost has contacted Amazon for comment.
Download our exclusive FREE Threatpost Insider eBook, “2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·