BOOK THIS SPACE FOR AD
ARTICLE ADThe FBI and Australian law enforcement set up the encrypted chat service and ran it for over 3 years, seizing weapons, drugs and over $48m in cash.
Law enforcement agencies have been selling encrypted phones to organized crime gangs for years, monitoring their conversations in what’s being called the biggest law enforcement sting ever.
Since 2018, agencies have been overseeing the distribution of hardened, encrypted devices that have enabled them to eavesdrop on crooks. The monitoring of the devices, which are called Anøm, Anom or An0m, has led to a dizzying array of actions.
On Monday, law enforcement agencies from the U.S., Australia and Europe announced that the massive global operation – called Operation Ironside by Australian Federal Police (AFP) and Trojan Shield by the FBI and Europol – resulted in these moves, carried out in 16 countries over the preceding few days:
700+ house searches 800+ arrests Seizure of 8+ tons of cocaine, 22 tons of cannabis & cannabis resin Seizure of 2 tons of amphetamine & methamphetamine, 6 tons of synthetic drugs precursors Seizure of 250 firearms, 55 luxury vehicles & over $48 million in various worldwide currencies and cryptocurrenciesShedding Light on the Criminal Underground
As the AFP outlined in the video below, for more than a decade, many organized crime syndicates have been dark. They’ve been using end-to-end encryption platforms enabled by customized phones that scramble sent messages which are then unscrambled when a recipient opens them.
But in 2018, the FBI seized Phantom Secure: A chat service that sold encrypted phones to drug traffickers, murderers-for-hire and other organized crime leaders. The Canada-based enterprise purchased smartphones and stripped the devices’ GPS, calling, texting and internet access. Then, Phantom Secure installed an encrypted email system, thereby placing the phones in closed-loop communication where they could only talk with each other. You couldn’t even begin a conversation to get one of the customized phones unless you had a connection to a distributor, as described in court documents (PDF) filed on Monday.
As FBI Special Agent Nicholas I. Cheviron wrote in the affidavit in support of a search warrant, while the FBI might have dented the supply of encrypted messaging devices, the demand didn’t go away. “The continued for these encrypted device platforms by criminals is significant,” he wrote. “[Transnational criminal organizations, or TCOs] are the target market for this technology because the entire success of their illicit activity is premised on avoiding law enforcement detection.”
Following the Phantom Secure takedown, the FBI got its hooks into the developer of a next-generation hardened device – one used only for encrypted messaging, having been stripped of its texting, calling, GPS, and internet functions. The app that the insider developed was called Anom. Next, the insider – the bureau referred to the person as its Confidential Human Resource (CHS) – basically handed the FBI a company that had a next-generation encrypted device under development.
The insider not only handed Anom over to the FBI: The CHS also agreed to distribute the devices within the existing network of distributors of encrypted chat devices, all of them linked to organized crime. Thus began more than three years of the distribution of encrypted devices that law enforcement agencies across the globe were listening to.
Officials Built a Decryption Key
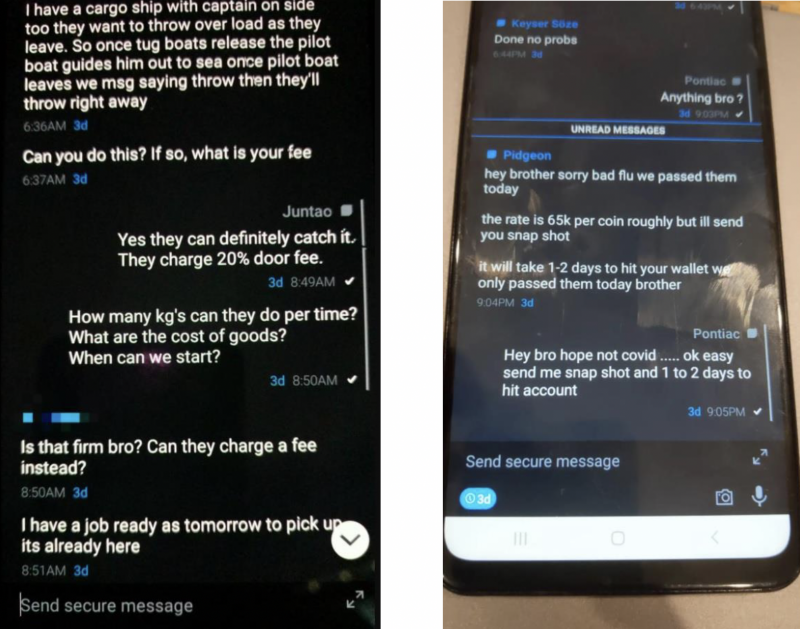
Before the Anom device was distributed, the CHS, the FBI, and the AFP built a master key into its encryption system: One that surreptitiously attached to each message and enabled law enforcement to decrypt and store the message as it was transmitted. Anom devices located outside the U.S. sent blind carbon copies (BCCs) of the messages to a third-party XMPP bot, which the FBI refers to as an “iBot” server located outside of the country. That’s where the bot would decrypt the messages and then re-encrypt them using keys that the bureau managed.
That enabled the FBI to intercept the communication of gangs, including details of drug movements or murder plots, photos of bulk cash proceeds of illegal transactions, GPS locations of narcotics shipments, and more.
Due to jurisdiction issues, the bulk of messages were reviewed by Australian authorities, who passed the information to the U.S. three times a week. Initial uptake of the Anom devices was slow in the world of organized crime, but it picked up speed by 2019. In fact, a third, unnamed country wound up hosting another iBot server and helping to pore over more than 26 million encrypted messages.
By 2020, demand had grown so strong that officials didn’t need to rely on undercover agents to promote the Anom devices anymore. The supply of hardened, encrypted devices had shrunken further after the Phantom Secure closure, with subsequent takedowns of competing platforms including EncroChat and Sky ECC. Those takedowns led to a massive demand for Anom devices. Before Sky’s dismantling, Anom had about 3,000 active users. Since March 12, 2021, in what officials called a direct result of the Sky Global takedown, there were close to 9,000 active Anom users.
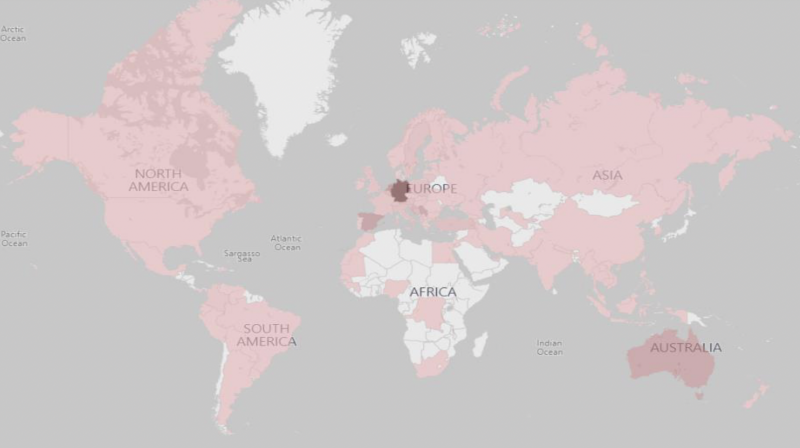
The graphic below shows the locations of Anom users located in more than 90 countries::
As the affidavit details, the FBI, along with a task force at Europol, identified more than 300 distinct TCOs using Anom. Those organized crime gangs included Italian organized crime; outlaw motorcycle gangs; and international narcotics source, transportation, and distribution cells.
Why Stop Now?
Officials shut down the sting operation when the search warrant expired yesterday, on Monday, June 7. But as The Record reported, some criminal groups apparently figured out that the An0m app was leaking their conversations to third-party XMPP servers a few months ago, in March.
On 21st March 2021, a (now deleted) blog post correctly identified that Anøm @anomsecure was in fact sending all the user messages to US-based LE. Criminals had caught onto the game as the arrests began. It can be viewed here in Google's cache. https://t.co/ck7bxun7la
— Hacker Fantastic (@hackerfantastic) June 7, 2021
First Hardware Man-in-the-Middle Scheme?
Rick Holland, chief information security officer and vice president of strategy at digital risk protection firm Digital Shadows, noted that this isn’t the first time we’ve seen law enforcement agencies run this type of deception. He pointed to Operation Bayonet: In July 2017, Europol and the U.S. Department of Justice seized the most popular English language dark web market, AlphaBay.
“Cybercriminal buyers and sellers flocked to an alternative market: Hansa,” Holland pointed out to Threatpost in an email on Tuesday. “These criminals didn’t know that the Dutch police had taken over the market, and for the next month, they collected intelligence and evidence on the criminal activities. International law enforcement was able to disrupt cybercrime.
But as is always the case after law enforcement actions, he observed, “Cybercrime finds a way. Other criminals and services rise from the ashes.”
But while it’s not the first man-in-the-middle sting, it’s unique in incorporating purpose-built encryption devices. Tyler Shields, CMO at JupiterOne, provider of cyber asset management and governance solution, stressed that this is the first we’ve seen hardware devices having been distributed and used to facilitate a man-in-the middle attack against more than 300 criminal organizations. “Typically, software-based attacks targeting a specific person or group of people are used,” he told Threatpost via email on Tuesday. “The fact that this targeted literally the entire underworld is of huge importance. This was a really big deal.”
Christoph Hebeisen, director of security intelligence research at mobile security provider Lookout, said that Anom enabled law enforcement to surveil criminal activity on a network that the criminals themselves assumed to be completely secure – at least, up until a few months ago. That makes the operation a “seemingly very successful campaign,” he told Threatpost in an email on Tuesday. So what comes next? It’s going to be something, he said: “As we have seen in the past, the end of one encrypted chat service popular with criminals usually leads to a shift to a new one,” he wrote.
That, in turn, could teach the crooks a valuable lesson that law enforcement probably don’t want them to learn, Hebelsen observed: “Since there has now been a string of such takedowns, each leading to a large number of arrests, criminals might become more careful,” he said. “This could lead them to use legitimate end-to-end encrypted chat services where they can hide among innocent users.”
Download our exclusive FREE Threatpost Insider eBook, “2021: The Evolution of Ransomware,” to help hone your cyber-defense strategies against this growing scourge. We go beyond the status quo to uncover what’s next for ransomware and the related emerging risks. Get the whole story and DOWNLOAD the eBook now – on us!
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·