BOOK THIS SPACE FOR AD
ARTICLE ADThe apps all used an unusual tactic of loading a legitimate Facebook page as part of the data theft.
A set of nine malicious Android apps that steal Facebook credentials were found on Google Play, which racked up a collective 5.9 million installations before Google removed them.
According to Dr. Web’s malware analysts, the applications were fully functional, so that victims remained in the dark about the fact they had downloaded malware to their Android devices. Pop-ups, however, informed users that to access all of the apps’ functions and to disable in-app ads, users would need to log into their Facebook accounts. Once they did, their passwords and user names were harvested.
“The advertisements inside some of the apps were indeed present, and this maneuver was intended to further encourage Android device owners to perform the required actions,” researchers said in a recent posting.
The malicious apps were detected as trojans called Android.PWS.Facebook.13, Android.PWS.Facebook.14, Android.PWS.Facebook.17 or Android.PWS.Facebook.18, according to the firm – all slight variations on the same code.
“While the Android.PWS.Facebook.13 [and] Android.PWS.Facebook.14 … are native Android apps, the Android.PWS.Facebook.17 and Android.PWS.Facebook.18 are utilizing the Flutter framework designed for cross-platform development,” researchers explained. “Despite this, all of them can be considered modifications of the same trojan since they use identical configuration file formats and identical JavaScript scripts to steal user data.”
They are:
PIP Photo, an image editor from the developer “Lillians” (5 million downloads) Processing Photo, a photo-editing software from a developer called “chikumburahamilton” (500,000+ installations) Rubbish Cleaner, a utility to optimize the Android device performance, from the developer “SNT.rbcl” (100,000 installations) Horoscope Daily from the developer “HscopeDaily momo” (100,000+ installations) Inwell Fitness from the developer “Reuben Germaine” (100,000+ installations) App Lock Keep, which enables access limitations for various apps, from the developer “Sheralaw Rence” (50,000+ installations) Lockit Master (yet another access-limiting app) from the developer “Enali mchicolo” (5,000 installations) Horoscope Pi from the developer “Talleyr Shauna” (1,000+ installations) App Lock Manager (another access-limiting app) from the developer “Implummet col” (10 installations)
The apps’ look upon launch. Source: Dr. Web.
“Of course, the main purpose of these activities is to harvest usernames and passwords for subsequent credential stuffing attacks,” David Stewart, CEO at Approov, said via email. “What all enterprises can do to protect themselves and their users against such exploits is to ensure that user credentials are not sufficient by themselves to log in to accounts. Mandating that an independently verified second factor such as a one-time passcode or an app authentication token must be presented alongside user credentials will dramatically shrink the attack surface.”
Legitimate Facebook Login and WebView
The mechanism by which the credential-harvesting was done is interesting, given that it employed a legitimate Facebook page, researchers discovered ((https://www.facebook.com/login.php).
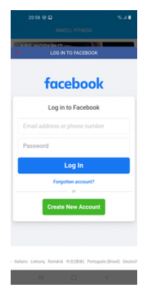
Source: Dr. Web.
“The displayed form was genuine,” according to the posting. “These trojans used a special mechanism to trick their victims. After receiving the necessary settings from one of the command-and-control servers (C2) upon launch, they loaded the legitimate Facebook web page into WebView. Next, they loaded JavaScript received from the C2 server into the same WebView. This script was directly used to highjack the entered login credentials.”
After that, the JavaScript sent the stolen credentials to the applications, which in turn sent them to the attackers’ C2 server.
The trojans also stole cookies from the current authorization session once the user logged into Facebook, analysts added.
Analysis of the malicious programs showed that while they’re built to impact Facebook accounts, the attackers could have gone bigger.
“The attackers could have easily changed the trojans’ settings and commanded them to load the web page of another legitimate service,” the researchers said. “They could have even used a completely fake login form located on a phishing site. Thus, the trojans could have been used to steal logins and passwords from any service.”
To protect themselves, users should pay attention to when and which apps ask them to log into other accounts. They should also check out the reviews for any app they download and vet the developer for legitimacy, according to Dr. Web.
“The reviews cannot provide an absolute guarantee that the apps are harmless, but can still alarm you about potential threats,” the firm recommended.
Malicious Google Play Apps
Users should also remember that the official Google Play store is no stranger to malicious apps. In March, for instance, a never-before-seen malware-dropper, Clast82, was found hidden in Android apps that fetched the AlienBot and MRAT malware in a bid to lift victims’ financial information. The dropper, dubbed Clast82, was disguised in benign apps, which don’t fetch a malicious payload until they have been vetted and cleared by Google Play Protect.
Then there’s the Joker trojan, which continues to creep into Google Play. Joker has been around since 2017 carrying out fleeceware operations: These apps advertise themselves as games, wallpapers, messengers, translators and photo editors, but once installed, they simulate clicks and intercept SMS messages to subscribe victims to unwanted, paid premium services. In September, researchers at Zscaler found 17 different samples of Joker being regularly uploaded to Google Play.
“The uncontrolled proliferation of mobile trojan apps on the Google Play store continues to wreak havoc with credentials and other personally identifiable information (PII) theft of consumers,” said Rajiv Pimplaskar, CRO at Veridium, via email. “While several causes can be identified, a core issue is the software industry’s over dependence on passwords which are at the root of over 80 percent of data breaches and ransomware attacks worldwide.”
Check out our free upcoming live and on-demand webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community.
.png)
















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·