Google intervened to remove nine Android apps downloaded more than 5.8 million times from the company's Play Store after the apps were caught furtively stealing users' Facebook login credentials.
"The applications were fully functional, which was supposed to weaken the vigilance of potential victims. With that, to access all of the apps' functions and, allegedly, to disable in-app ads, users were prompted to log into their Facebook accounts," researchers from Dr. Web said. "The advertisements inside some of the apps were indeed present, and this maneuver was intended to further encourage Android device owners to perform the required actions."
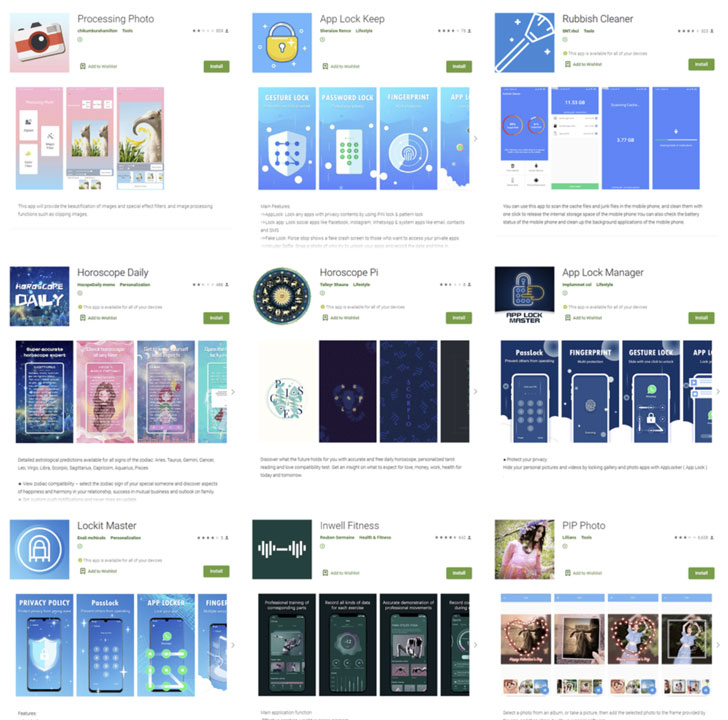
The offending apps masked their malicious intent by disguising as photo-editing, rubbish cleaner, fitness, and astrology programs, only to trick victims into logging into their Facebook account and hijack the entered credentials via a piece of JavaScript code received from an adversary-controlled server.
The list of apps are as follows -
PIP Photo (>5,000,000 installs) Processing Photo (>500,000 installs) Rubbish Cleaner (>100,000 installs) Horoscope Daily (>100,000 installs) Inwell Fitness (>100,000 installs) App Lock Keep (50,000 installs) Lockit Master (5,000 installs) Horoscope Pi (>1,000 installs) App Lock Manager (10 installs)In the last link of the attack, the stolen information was exfiltrated to the server using the trojanized applications.
While this specific campaign appears to have set its sights on Facebook accounts, Dr. Web researchers cautioned that this attack could have been easily expanded to load the login page of any legitimate web service with the goal of stealing logins and passwords from any platform.
The latest disclosure comes days after Google announced new measures for the Play Store, including requiring developer accounts to turn on 2-Step Verification (2SV), provide an address, and verify their contact details as part of its ongoing efforts to combat scams and fraudulent developer accounts.
If anything, the development is yet another reminder that users are better off served by installing apps from known and trusted developers, watch out for permissions requested by the apps, as well as to pay attention to other user reviews prior to installation.
Found this article interesting? Follow THN on Facebook, Twitter and LinkedIn to read more exclusive content we post.
.png)
 3 years ago
181
3 years ago
181 

















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·