BOOK THIS SPACE FOR AD
ARTICLE ADCoupon codes for Netlifx or Google AdWords? Voting for the best football team? Beware: Malicious apps offering such come-ons could inflict a new trojan.
Researchers have uncovered a new Android trojan, dubbed FlyTrap, that’s spread to more than 10,000 victims via rigged apps on third-party app stores, sideloaded apps and hijacked Facebook accounts.
In a report posted on Monday, Zimperium’s zLabs mobile threat research teams wrote that FlyTrap has spread to at least 144 countries since March, via malicious apps distributed through Google Play store and third-party app marketplaces. The malware, which researchers have traced to operators working out of Vietnam, is part of a family of trojans that use social engineering to take over Facebook accounts, the researchers said.
The session-hijacking campaign was initially distributed via Google Play as well as third-party app stores. For its part, Google Play removed the malicious apps after Zimperium zLabs gave it the heads-up.
They are, however, still being distributed on third-party, unsecured app stores, “highlighting the risk of sideloaded applications to mobile endpoints and user data,” Zimperium pointed out.
These are the nine bad apps:
GG Voucher (com.luxcarad.cardid) Vote European Football (com.gardenguides.plantingfree) GG Coupon Ads (com.free_coupon.gg_free_coupon) GG Voucher Ads (com.m_application.app_moi_6) GG Voucher (com.free.voucher) Chatfuel (com.ynsuper.chatfuel) Net Coupon (com.free_coupon.net_coupon) Net Coupon (com.movie.net_coupon) EURO 2021 Official (com.euro2021)How You Get Stuck in FlyTrap
The threat actors use a variety of come-ons: Free Netflix coupon codes, Google AdWords coupon codes, and voting for the best football/soccer team or player. They’re not only enticing; they’re slick, too, with high-quality graphics – all the better to hide what they’re doing behind the scenes.
“Just like any user manipulation, the high-quality graphics and official-looking login screens are common tactics to have users take action that could reveal sensitive information,” zLabs researchers explained. “In this case, while the user is logging into their official account, the FlyTrap Trojan is hijacking the session information for malicious intent.”
The bad apps purport to offer Netflix and Google AdWords coupon codes, or to let users vote for their favorite teams and players at UEFA EURO 2020: The quadrennial European soccer championship that wrapped up on July 11 (delayed a year by COVID-19). But first, before the malware apps dish out the promised goodies, targeted users are told to log in with their Facebook accounts to cast their vote or collect the coupon code or credits.
There are, of course, no free Netflix or AdWords coupons or codes, and there’s no fav-football voting to be had. Rather, the malicious apps are just after Facebook credentials. They make a last-stab attempt to look legitimate by tossing up a message saying that the coupon or code expired “after redemption and before spending,” as shown in the screen captures below.
FlyTrap Gets Busy
After a bamboozled Android user forks over their Facebook credentials, the apps get busy slurping up details that include:
Facebook ID Location Email address IP address Cookies and tokens associated with the Facebook accountThen, the trojan uses victimized accounts to spread its tentacles, making it look like the rightful owners are sharing legitimate posts, zLabs researchers said: “These hijacked Facebook sessions can be used to spread the malware by abusing the victim’s social credibility through personal messaging with links to the Trojan, as well as propagating propaganda or disinformation campaigns using the victim’s geolocation details,” they wrote. “These social-engineering techniques are highly effective in the digitally connected world and are used often by cybercriminals to spread malware from one victim to another.”
True that: Similar campaigns include SilentFade: a malware campaign linked to Chinese actors that targeted Facebook’s ad platform for years and siphoned $4 million from users’ advertising accounts, using the compromised accounts to promote malicious ads, steal browser cookies and more. More recently, a similar malware – a password- and cookie-stealer named CopperStealer – was found to have been compromising Amazon, Apple, Google and Facebook accounts since 2019, then using them for additional cybercriminal activity.
How FlyTrap Snaps
FlyTrap uses JavaScript injection to hijack sessions by logging into the original and legitimate domain. Its bad apps open the legit domain inside a WebView, and then it injects malicious JavaScript code that enables the extraction of targeted information – i.e., cookies, user account details, location and IP address.
FlyTrap’s command-and-control (C2) server uses the pilfered login credentials to authorize access to the harvested data. But it gets worse: zLabs found that the C2 server has a misconfiguration that could be exploited to expose the entire database of stolen session cookies “to anyone on the internet,” which would further endanger victims, the researchers said.
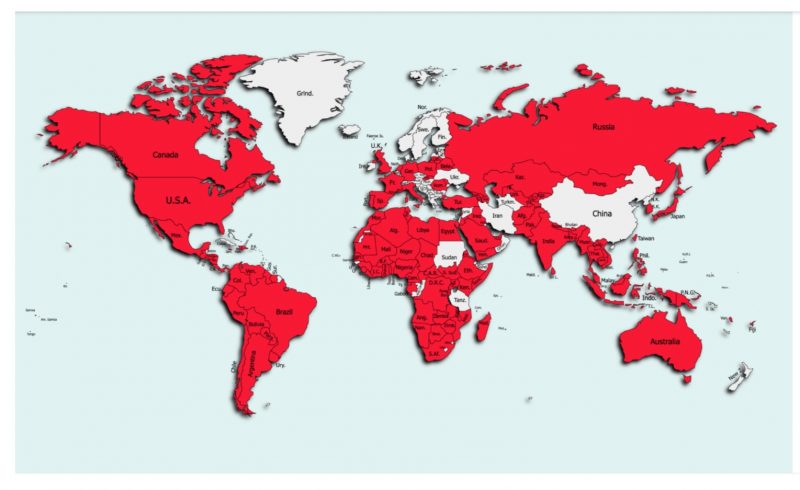
zLabs provided the map below, which illustrates the 144 countries in which FlyTrap has snared thousands of victims.
There’s nothing new about credential-stealing from mobile devices, the researchers noted: After all, mobile endpoints “are often treasure troves of unprotected login information to social media accounts, banking applications, enterprise tools and more.”
In fact, FlyTrap’s tools and techniques are so effective, don’t be surprised if some malicious actor picks it up and retrofits it – or “any other trojan” – to go after even more critical information, they said.
How to Shield Your Android
Richard Melick, Zimperum’s director of product marketing for endpoint security, told Threatpost on Monday that Android users can immediately decrease their chance of infection by ensuring that they’re disallowing installation of any app from an untrusted source to be installed.
While the setting is turned off by default on most Android devices, social-engineering techniques are “highly effective at tricking users into allowing it,” he said in an email.
To disable unknown sources on Android, go to settings, choose “security,” and make sure that the “unknown sources” option isn’t selected.
Melick also recommended that users enable multi-factor authentication (MFA) for all social-media accounts and any other accounts with access to sensitive and private data.
“While this will not stop this kind of hack, it adds additional security layers such as geo-based alerts” to the user’s profile, he advised – i.e., “This account is trying to log in from Vietnam.”
If an Android user suspects that a Facebook account has been connected to a malicious party, Melick said to follow Facebook instructions to log out of all accounts on all devices, immediately change their passwords and enable MFA if not already in use.
In general, be suspicious about grabby apps, Melick advised. “Overall, it is about being aware of what an application is asking for,” he observed. “If you need to connect your social media accounts to get access to the coupon or deal, pause and ask why. What could that site/coupon company now use that data for? What will they be able to do with your account? Do they really need that to give you a deal? Once the connection is established, your data can be easily taken and used without your consent.”![]() Worried about where the next attack is coming from? We’ve got your back. REGISTER NOW for our upcoming live webinar, How to Think Like a Threat Actor, in partnership with Uptycs on Aug. 17 at 11 AM EST and find out precisely where attackers are targeting you and how to get there first. Join host Becky Bracken and Uptycs researchers Amit Malik and Ashwin Vamshi on Aug. 17 at 11AM EST for this LIVE discussion.
Worried about where the next attack is coming from? We’ve got your back. REGISTER NOW for our upcoming live webinar, How to Think Like a Threat Actor, in partnership with Uptycs on Aug. 17 at 11 AM EST and find out precisely where attackers are targeting you and how to get there first. Join host Becky Bracken and Uptycs researchers Amit Malik and Ashwin Vamshi on Aug. 17 at 11AM EST for this LIVE discussion.
.png)


















 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·