BOOK THIS SPACE FOR AD
ARTICLE ADStep by Step guide for beginners!

As a pentester developing new skills in different areas is very important as you might miss something crucial from one approach. Android pentesting is one of them, but it requires a dedicated environment and I will explain how to setup an easy one. So let’s begin!
Table of contents:
Setup android emulator (Genymotion)Configure Burp Suite CA certificate on deviceFrida to bypass SSL pinningBytecode Viewer (for static analysis)Before installing emulator, I would recommend to install any Linux based distro or Santoku, which is especially designed for mobile pentesting. Installing Santoku is out of scope in this write-up, but you can follow up this guide to setup.
When starting out learning, android emulators are the great way to get experience with a variety of devices having different API levels without costing much and free version of Genymotion provides exactly that with great User Experience and easy to configure nature.
Note: VirtualBox is used as a core by genymotion to virtualize Android operating systems. So please install VirtualBox in your system in order to proceed: link
Genymotion requires user registration to use its dashboard and for that first you need to create an account: link
After completing your registration process download its installer from here and install it in your host computer.
# Make it executable$- chmod +x genymotion-<version>-linux_x64.bin# Specify your path, here i am installing in user's home directory
$- ./genymotion-<version>-linux_x64.bin -d ~/
Once Genymotion get install now you can sign in using your credentials specified in the registration process and use its dashboard which looks like shown in Figure 1.
Here I’ve installed two devices already, but you can install a new device by clicking on plus icon at the top right corner and selecting your desired template and for this example I will install Samsung Galaxy S9 (8.0 — API 26)
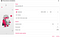
Configuring Genymotion
After initiating the device, there are a couple of things to consider:
ARM translator:If some app contains ARM native code, then Genymotion will not be able to run the app as it consists of x86 (32-bit) architecture and will throw an error. You can avoid this problem by installing ARM translation library into emulated device: link
Note: At this point of time this library only supports up to android version 8.0 so download right package according to your emulated device’s specifications.
Saving APK (Android Package):Installing target apps into the emulated device becomes much easier by the Open Gapps widget present in a toolbar which you can access like shown in Figure 3.

After its installation you can download your target apps directly from Play Store. But saving this apk into host system would be beneficial for main two reasons:
No need to download the same version of app into different emulated devices having same specifications.Required for a decompiler in order to review the source code for static analysis.So how we can save them?
Usually you have two ways to get apk either download it from sites like evozi or pull it using adb (Android debug bridge)
Note: Genymotion have pre-installed this tool in its installation directory and mine is located in ~/genymotion/tools/
For this demonstration purpose I will use the Twitter Lite app:
# Call package manager (pm) and filter out twitter's package name$- ./adb shell pm list packages | grep twitter# Check the absolute path
$- ./adb shell pm path com.twitter.android.lite# Pull apk and rename to twitter_lite.apk
$- ./adb pull /data/app/com.twitter.android.lite-somevalue.apk twitter_lite.apk

Now just drag & drop these APKs into emulated devices.
I assume the reader already have installed burp suite if not then simply download its community version: link
Here I will show you only how to configure with android emulated device.
Android Nougat and above (API >= 24) only trusts system level CA (certificate authority) certificates for secure communications especially for WebView. You can read more from here: link
So the easiest method to bypass this restriction is installing Burp CA’s certificate as the system trusted certificate and this method will also prevent us from setting a Lock screen PIN 😎
Steps:
1. Export burp CA into der format
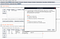
2. Use Openssl to convert DER to PEM and rename to <cert-hash>.0
# Convert certificate format from DER to PEM$- openssl x509 -inform DER -in cacert.der -out cacert.pem# Display the "hash" of the certificate subject name
$- openssl x509 -inform PEM -subject_hash_old -in cacert.pem | head -1# Move cert.pem and rename to <hash>.0
$- mv cacert.pem 9a5ba575.0

Note: Use -subject_hash if your openssl <1.0
3. Move certificate in emulated device using adb
# Change /system partition into writable mode with remount$- ./adb remount# Transfer certificate
$- ./adb push 9a5ba575.0 /system/etc/security/cacerts/# Change its permissions
$- ./adb shell chmod 644 /system/etc/security/cacerts/9a5ba575.0# Reboot to let changes occur
$- ./adb shell reboot
Now your certificate should be installed as a system-trusted CA certificate which you can confirm by navigating:
Settings →Security & Location → Encryption & credentials → Trusted Credentials
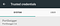
4. Configure burp suite’s proxy
Navigate to Proxy → Options → Proxy Listeners → Add
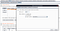
Here I’ve bound port 8082 to my VirtualBox’s interface IP
5. On emulated device, configure WiFi settings.
Navigate to WiFi → Long press WiFi name → Modify Network → Advanced Options → Change proxy None to Manual
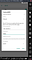
After this you can see network traffic in burp’s history
Basically Frida is a dynamic code instrumentation toolkit which lets you dynamically inject snippets of code into running processes of the app in order to change its behavior and this is exactly what we need to bypass SSL pinning but now you might be wondering what’s that?
Well, SSL pinning is a technique used in applications as an additional security layer for application traffic in order to prevent attacks like MitM (man-in-the-middle) and this will not allow burp to intercept the traffic unless we use tools like Frida to hook our specific code which bypass this functionality.
Installation
Install frida-tools with pip3 in host computer using cli$- pip3 install frida-tools2. Download only x86 version of Frida server because virtual devices by Genymotion are x86-based which you can verify like shown in Figure 12.

Download link
# Downloading using wget as an example$- wget https://github.com/frida/frida/releases/download/<version>/frida-server-<version>-android-x86.xz# Decompress using unxz
$- unxz frida-server-<version>-android-x86.xz# Rename for ease
$- mv frida-server-<version>-x86.xz frida-server# Transfer into the emulated device using adb
$- ./adb push ~/Downloads/frida-server /data/local/tmp# Change its permissions
$- ./adb shell chmod 755 /data/local/tmp/frida-server# Run Frida-server in the background
$- ./adb shell /data/local/tmp/frida-server &
Now, after setting up Frida server, we will be able to use our scripts but for that first we need to find APK’s name which you can find by either way
# Old method using pm$- ./adb shell pm list packages | grep someapp# Another way using Frida but for this app first need to be started
$- frida-ps -U | grep someapp
For this demonstration purpose my target is Skrill and i am using this bypass script, simply save this into a js file
Now lets see if Skrill is throwing any SSL error
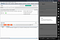
As expected it does, now use Frida with a bypass script to intercept network traffic
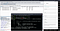
And as you can see now we can continue our testing after successful SSL pinning bypassed using FRIDA 😃
Static analysis is a straightforward process to look how an application performs by reviewing its source code. However decompiling its source code can be hard and for this purpose there are some decompilers like jadx
But I personally liked Bytecode Viewer due to its wide range of different Java decompilers, two bytecode editors and many other features.
Download link
After downloading, simply run the decompiler and drag & drop your files into the Files section to decompile.
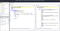
That’s it for now 😃
Hope this make some of your doubts clear and you are able to create your own android LAB.
Happy Hacking!
.png)
 4 years ago
228
4 years ago
228 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·