BOOK THIS SPACE FOR AD
ARTICLE ADSetting up the Burp suite with an android device is simple but a little tricky.
There are several ways to set up this environment.
1. Setting up Burp suite with Android VM (Needs Genymotion with virtual box).
2. Setting up Burp suite with Android physical Device (Needs Rooted android device).
Setting up Burp suite with Android VM (Needs Genymotion with virtual box) or with Android physical device.
Follow the below-mentioned steps:
Prerequisite:
i. Burp suite.
ii. Genymotion (With virtual box.).
or
ii. Android device (Rooted.).
iii. adb tools. Click here to download.
iv. Setting up proxy and Certificate in Android VM/device.
v. Frida installed in host PC and Frida server file to run Frida from the Android device. (python installed in the host machine.(PC/laptop))
i. Burp Suite.
Step 1: Certificate export: Open Burp Suite. Go to Proxy → Options → Proxy Listener → click on import/ export CA certificate. → At the export choose Certificate in DER format.(eg. cacert.der) → Click on next → select any file name having extension as .der → Click on next.
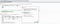
Step 2: Go to the folder where you saved the Burp CA certificate. → Change the extension from .der to .crt (eg. cacert.crt)→ and save it.
Step 3: Proxy setting in burp: Go to Proxy → Options → Proxy Listener → Click on add → Select specific address and then select IP of the device where burp is running or Simply select All interfaces (It will intercept traffic all the traffic going through your system.). → Enable this config.
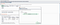
ii. Genymotion (With virtual box.).
Step 1: Installing Genymotion: Download Genymotion (Please select with the virtual box) from Click here to download. → Register with Genymotion → Login → Click on Add icon to add a new Virtual Device. → Select Android API according to Android version → select Device from the list → Click on Next. (Recommended device and settings are in the attached screenshots.)


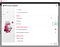
Step 3: Install Open Gapps/Google Play Services:
Power on the VM device.Click on Open Gapps icon on side bar. Follow the steps and it will automatically download and install Gapps in your VM device.or
ii. Android Physical Device.
Note: We need an android device having Android OS version 6.0 or newer. Along with this we need to root the device (there are different ways to root the device, flashing Magisk is one of the popular and recommended way to root an android device.).
Step 1: Just plug in the android device with USB cable into the system where want to capture the traffic.
iii. ADB tools. Click here to download.:
ADB tools are useful while doing the out of the box stuff on Android, like direct installing an app in device from your laptop/pc or pushing any file directly to any location. (We will see the use of ADB in the upcoming steps.)
iv. Setting up proxy and Certificate in Android VM/device.
Step 1: Setting up the proxy in Android: Power on the Android device/Android VM from Genymotion (If it shows IP related error at bootup, then go to virtual box start the device listed there and power off after it gets an IP.) → Go to Settings → go to WIFI → Hold on Wifi name listed there and select Modify Network. → Select proxy as Manual → Input Hostname as you Host machine’s IP/Port which was used to set as proxy listener at Burp proxy setting → Save.
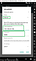
Step 2: Setting up the burp Certificate in Android:
Open cmd/terminal. Move to the directory where ADB tools are present.
Push burp certificate to the android device: There are two ways to add a certificate in the Android device.
i. Adding a Certificate into user-defined certificates.: (Recommanded) push burp certificate (having extension as .crt) using the command
"adb push path_to_certificate /sdcard/Download/".
Switch to android device → Go to settings → Security → install from Sdcard → Select the certificate from Download folder → it will ask to enter a name, Enter any name here (eg. Burp CA). → It will ask to add PIN security. → Enter the security Pin. → Next.
ii. Adding a Certificate into system-defined certificates.: Download and install OpenSSL form Click here. → open cmd and run command
"openssl x509 -inform DER -in path_to_certificate/cacert.der -out path_to_certificate/cacert.pem"
then run.
"openssl x509 -inform PEM -subject_hash_old -in cacert.pem"
it will show as hash value copy it save it for further use.
then run .
"mv path_to_certificate/cacert.pem path_to_certificate/<hash>.0" or simply rename the file cacert.pem as <hash_value>.0
Now copy the certificate tot the device. here is the list of commands to execute.
"adb remount" →
"adb push <hash_value>.0 /sdcard/Download" →
"adb shell" →
"mv /sdcard/Download/<hash_value>.0 /system/etc/security/cacerts/" →
"chmod 644 /system/etc/security/cacerts/<hash_value>.0"
Note: The benefit of adding a burp certificate into system-defined certificates is, we don’t need to follow step V. which is Frida setup. (But it’s not a recommended way because sometimes it misses some API calls.)
Reference: https://enderspub.kubertu.com/burp-suite-ssl-pinning
V. Frida installation in host PC and running frida server from Android device.
Step 1: Installation Frida in the host PC: run command to install Frida in host pc “pip install frida-tools".
Step 2: Running Frida from android device:
run command “adb shell getprop ro.product.cpu.abi" to know the processor architecture. →download the Frida server file from Click here. (Select your file according to the processor architecture if arm than arm file and if it is x86 than select x86 file.) →extract tile xz file → copy the file which is present in the extracted folder to the android device via the command “adb push ./frida-server-12.x.y-android-xyz /data/local/tmp/" →Now disable SELinux (This is one time process.): “adb shell" → in the shell: "su" → "setenforce 0".Start Frida server by command: “adb shell" → "/data/local/tmp/frida-server-12.x.y-android-xyz &"Step 3: Creating js file to do SSL pinning.: This needs to fix certificate-related errors and capture traffic in Burp suite.
create a js file named frida-ssl-pin.js And paste the following content in it and save the file.
Java.perform(function() {
var array_list = Java.use(“java.util.ArrayList”);
var ApiClient = Java.use(‘com.android.org.conscrypt.TrustManagerImpl’);
ApiClient.checkTrustedRecursive.implementation = function(a1, a2, a3, a4, a5, a6) {
// console.log(‘Bypassing SSL Pinning’);
var k = array_list.$new();
return k;
}
}, 0);
Step 4: Running the Frida receiver/client from the host machine.:
Open the app in android device. now find the process name by running the command from cmd: “frida-ps -U". and copy the process name.run Frida receiver/client by running the command: “frida -U -l path_to_js_file/frida-ssl-2.js --no-paus -f com.example.application". This will open the app again.. and now you are ready to capture traffic in Burp Suite.Special Notes:
Whenever the device restarts, We need to repeat the steps of running the Frida server from the android device.In the case mentioned in point 1, we need to start the Frida receiver/client in the host machine also.Please let me know in case of any query….
.png)
 4 years ago
231
4 years ago
231 














 Bengali (Bangladesh) ·
Bengali (Bangladesh) ·  English (United States) ·
English (United States) ·